∞ Software Supply Chain
Close the Software Supply Chain Security Gap
AI coding agents, developer machines, code repositories, and CI/CD pipelines are all targets for software supply chain attacks. StepSecurity provides end-to-end defense against these attacks.



Trusted By Enterprises Worldwide















Overlooked Attack Surfaces
Unaddressed Software Supply Chain Security Risks Leave Companies Open to Compromise
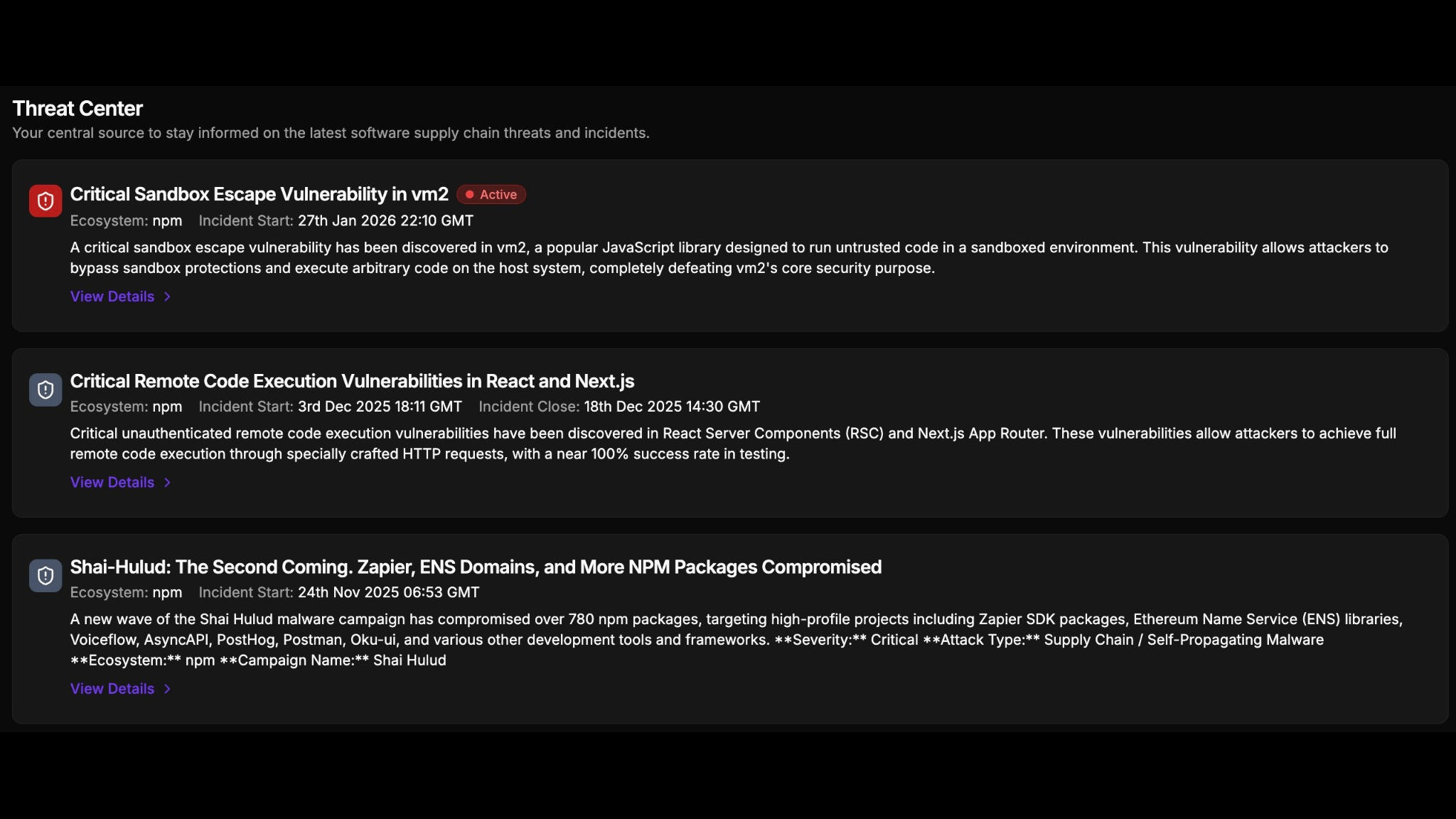
Breaking News -- CI/CD Supply Attack Chains on the Rise

March 2025
tj-actions/changed-files action is compromised
Application Security
Learn how StepSecurity Harden-Runner detected the tj-actions/changed-files supply chain attack

January 2024
PyTorch GitHub Actions Compromise
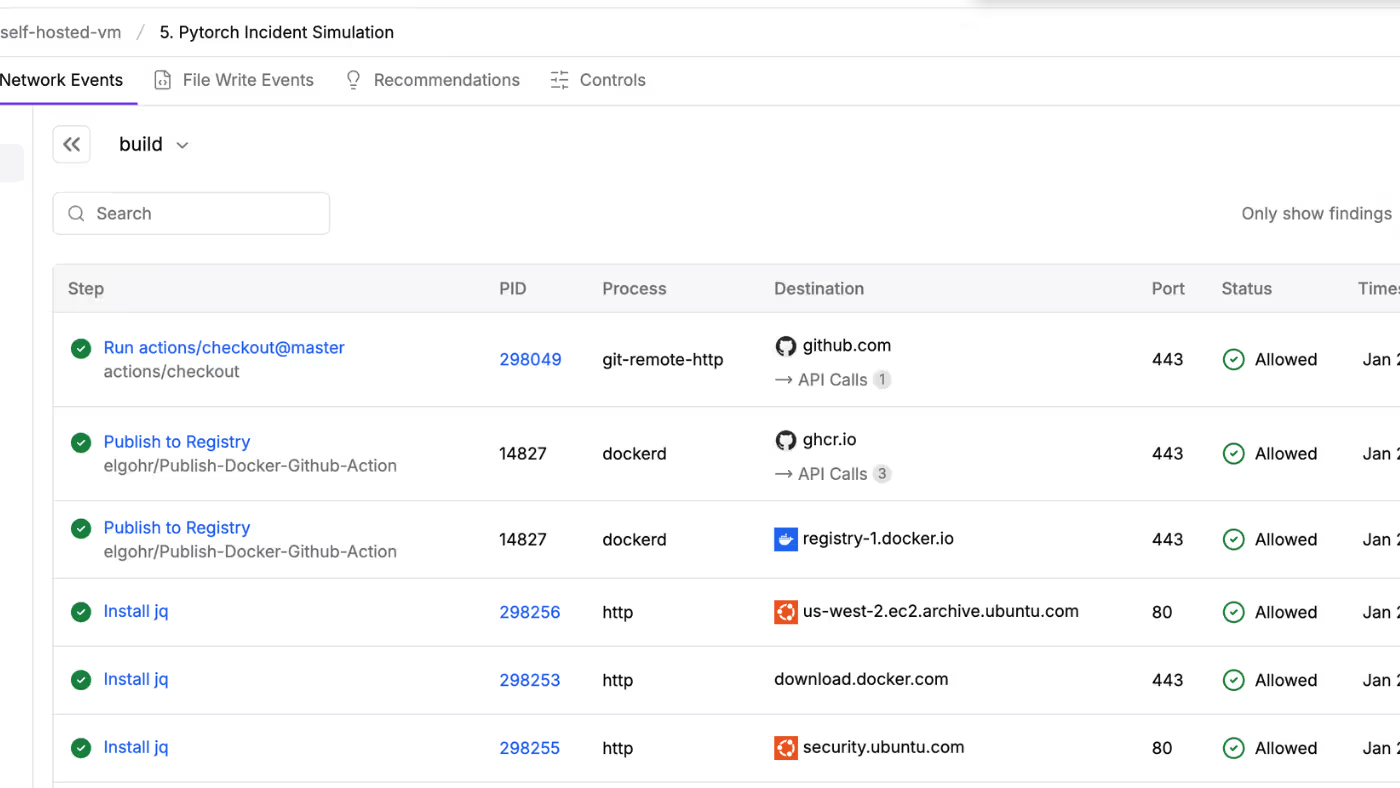
Researchers detail a CI/CD attack leading to PyTorch releases compromise via GitHub Actions self-hosted runners
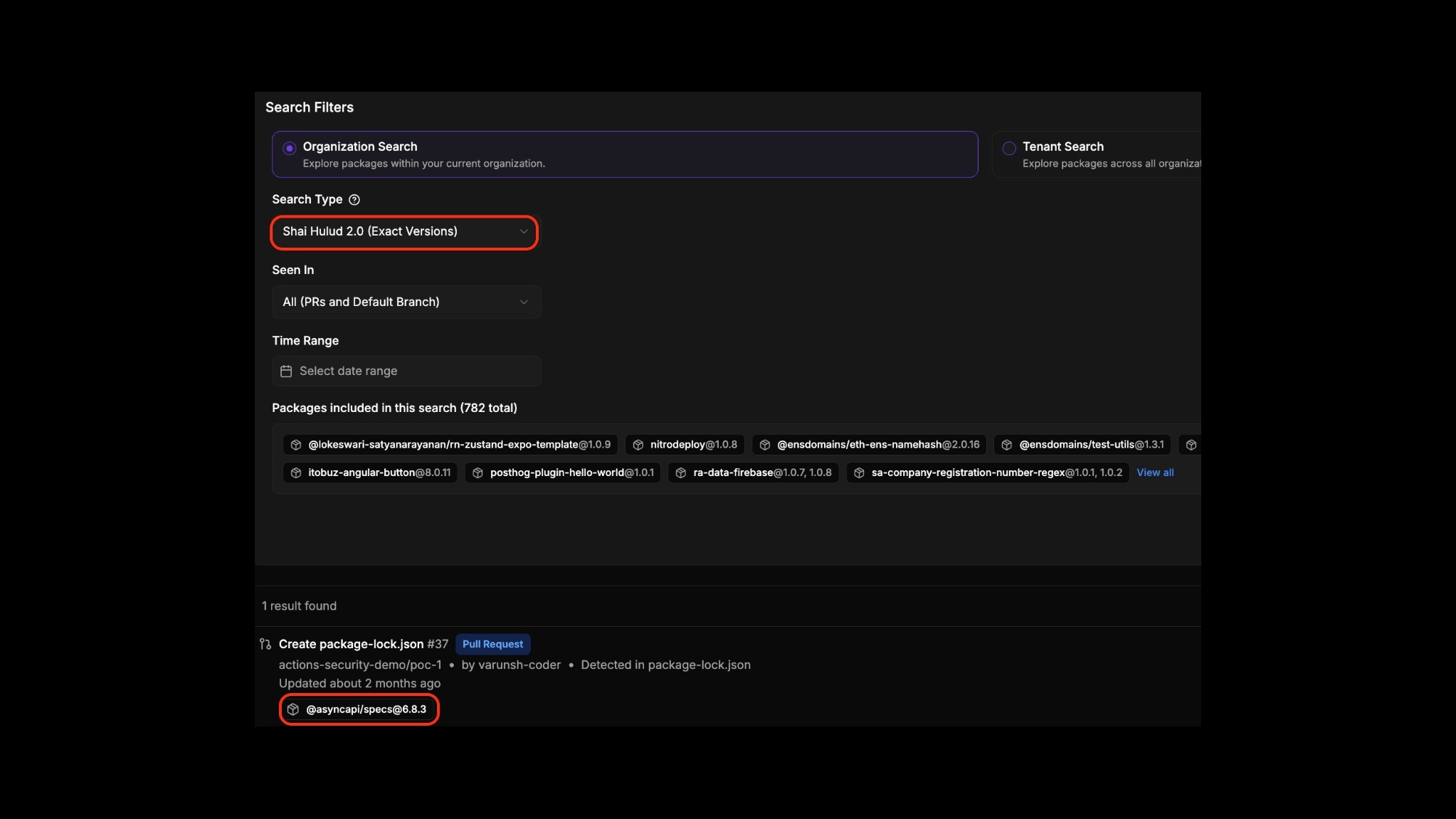
Shai Hulud- The Second Coming

Nov 2025
Malware

Oct 15, 2025
100+ VSCode Extensions Compromised
Access Token Leak
Publishers leaked access tokens, exposing 150,000+ developers to malicious auto-updates.

Testimonial
“Before StepSecurity, detecting the origin of a suspicious outbound network connection was challenging with traditional CNAPPs or IDS solutions, as we’d only see a general alert. StepSecurity gives us complete visibility into which specific Action triggered a connection and even lets us drill down into host processes tied to that Action. Now, we have a clear and actionable picture of every network connection our runners make, and we can respond with confidence.”
Testimonial
"StepSecurity provided an immediate large scale effect by providing a single pane-of-glass visibility into all traffic egressing from our GitHub Actions CI/CD infrastructure. This provided immediate real-world visibility and enhanced our ability to detect and respond to incidents."
Testimonial
"It's easy to get started with GitHub Actions, but using it securely has historically required manual effort and configuration which isn't as straightforward. StepSecurity solves this by automating security best practices for Workflows as well as through their harden-runner Action which provides protection against exfiltration and source code tampering throughout the lifecycle of a Workflow. Leveraging the harden-runner Action is both painless and an absolute must for any project!"
Testimonial
StepSecurity has filled a critical gap in our CI/CD security stack. It gave us visibility into what our GitHub Actions runners are actually doing, not just what they’re configured to do. StepSecurity is now an integral part of how Neon secures its CI/CD pipelines.





Complete SDLC Protection
The Definitive Platform for Software Supply Chain Protection
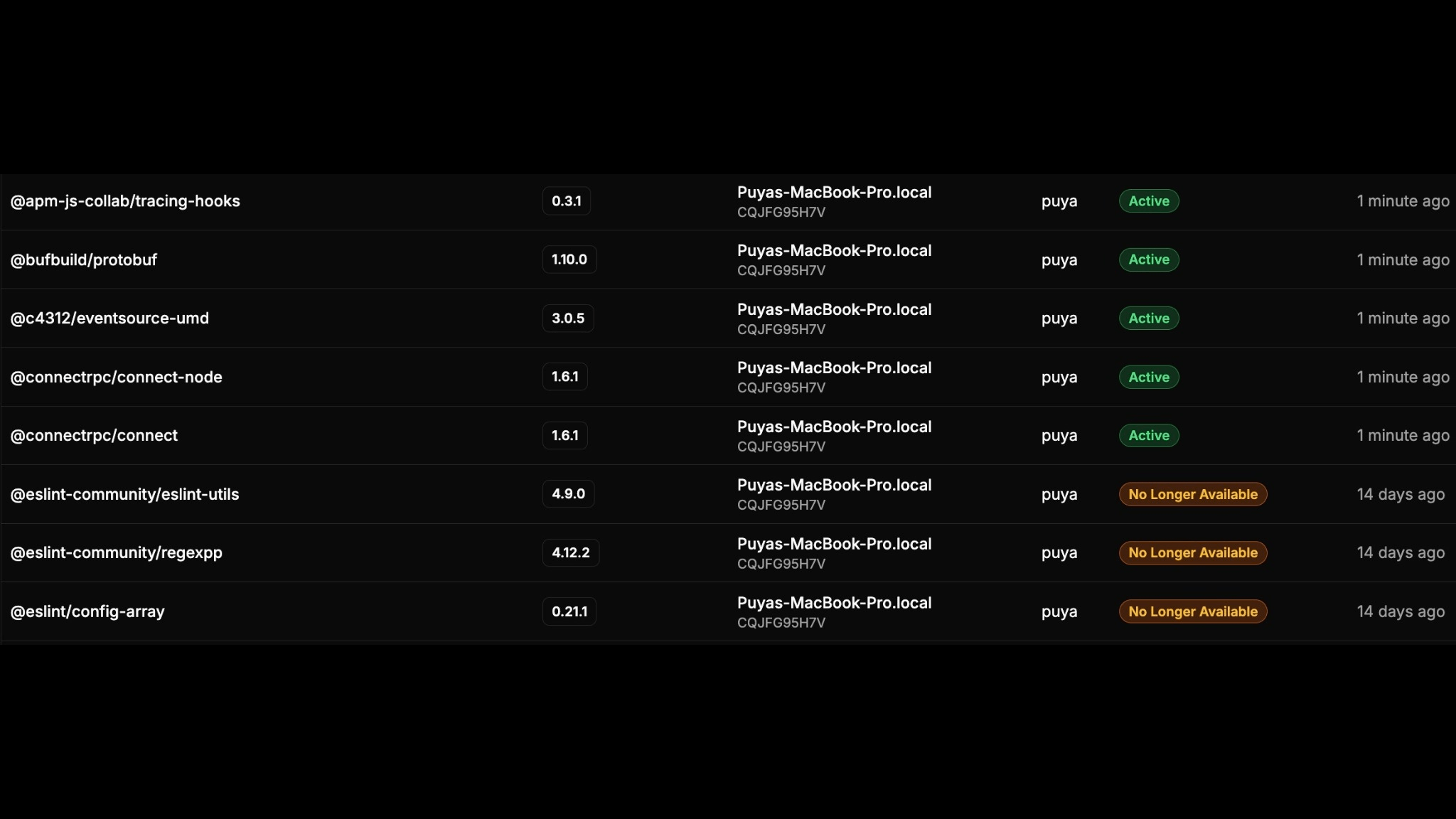
Dev Environment
Code Repository
GitHub Actions
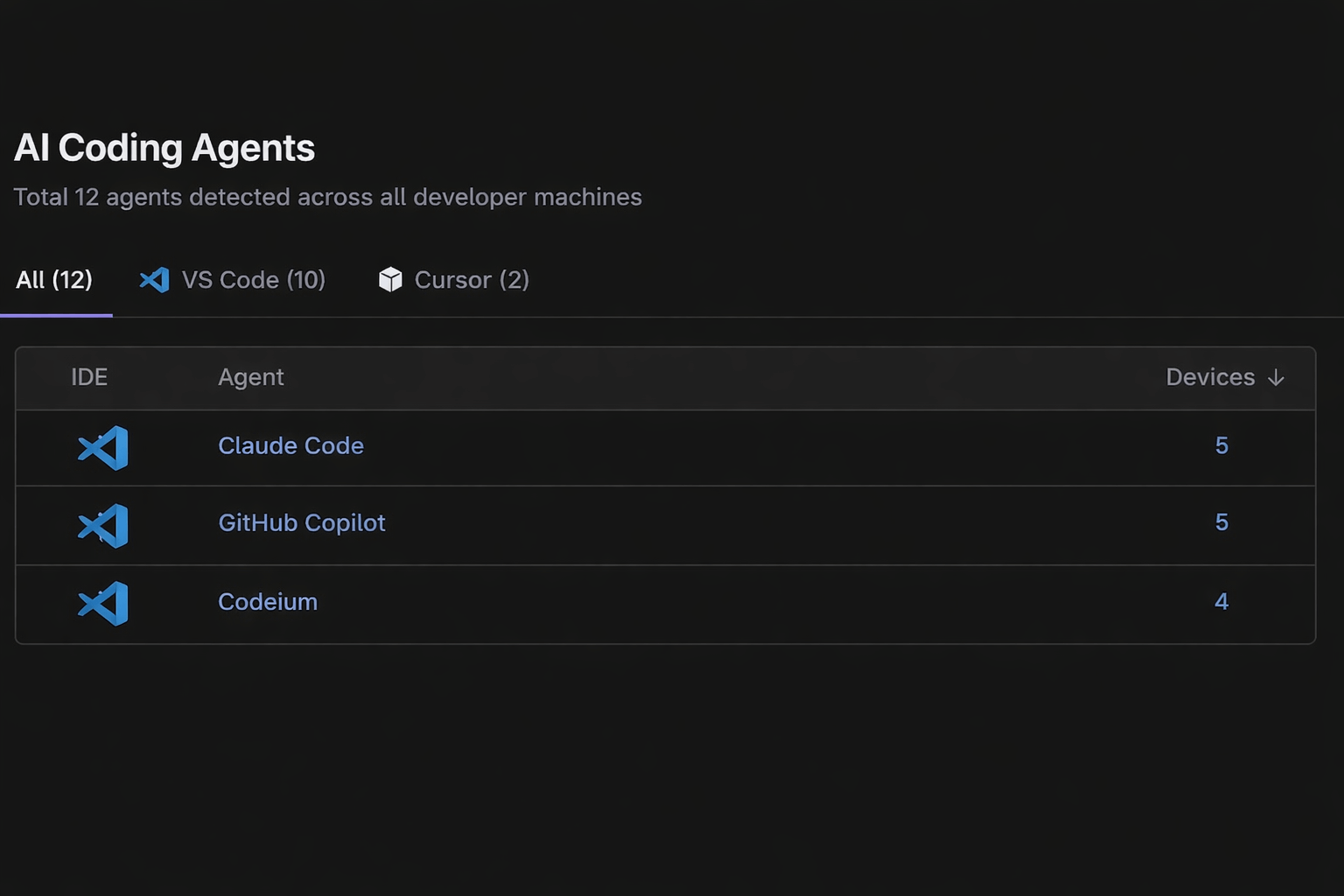
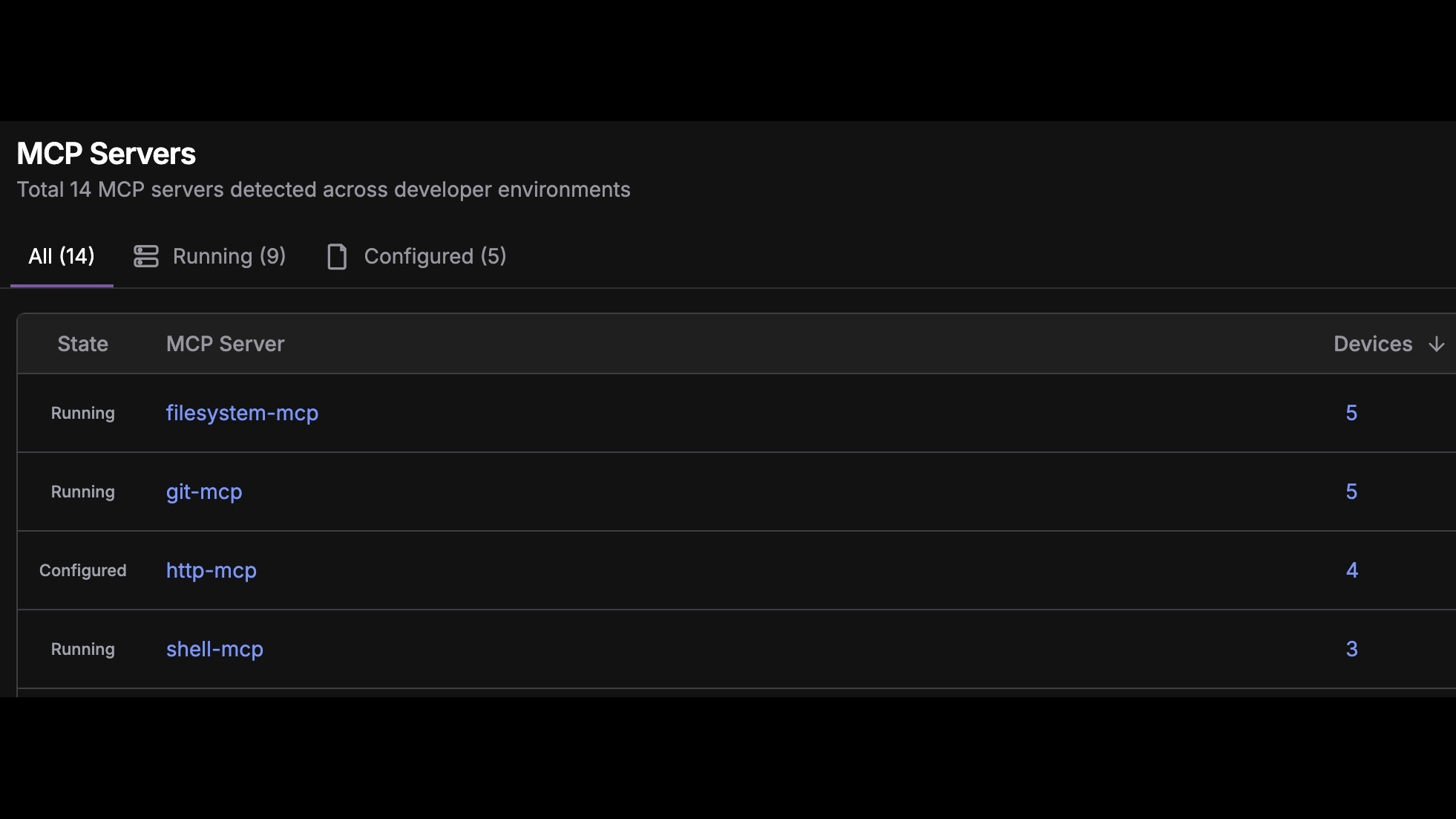
AI coding agents, along with human developers have direct access to your source code and credentials, making developer environments ground zero for supply chain attacks.
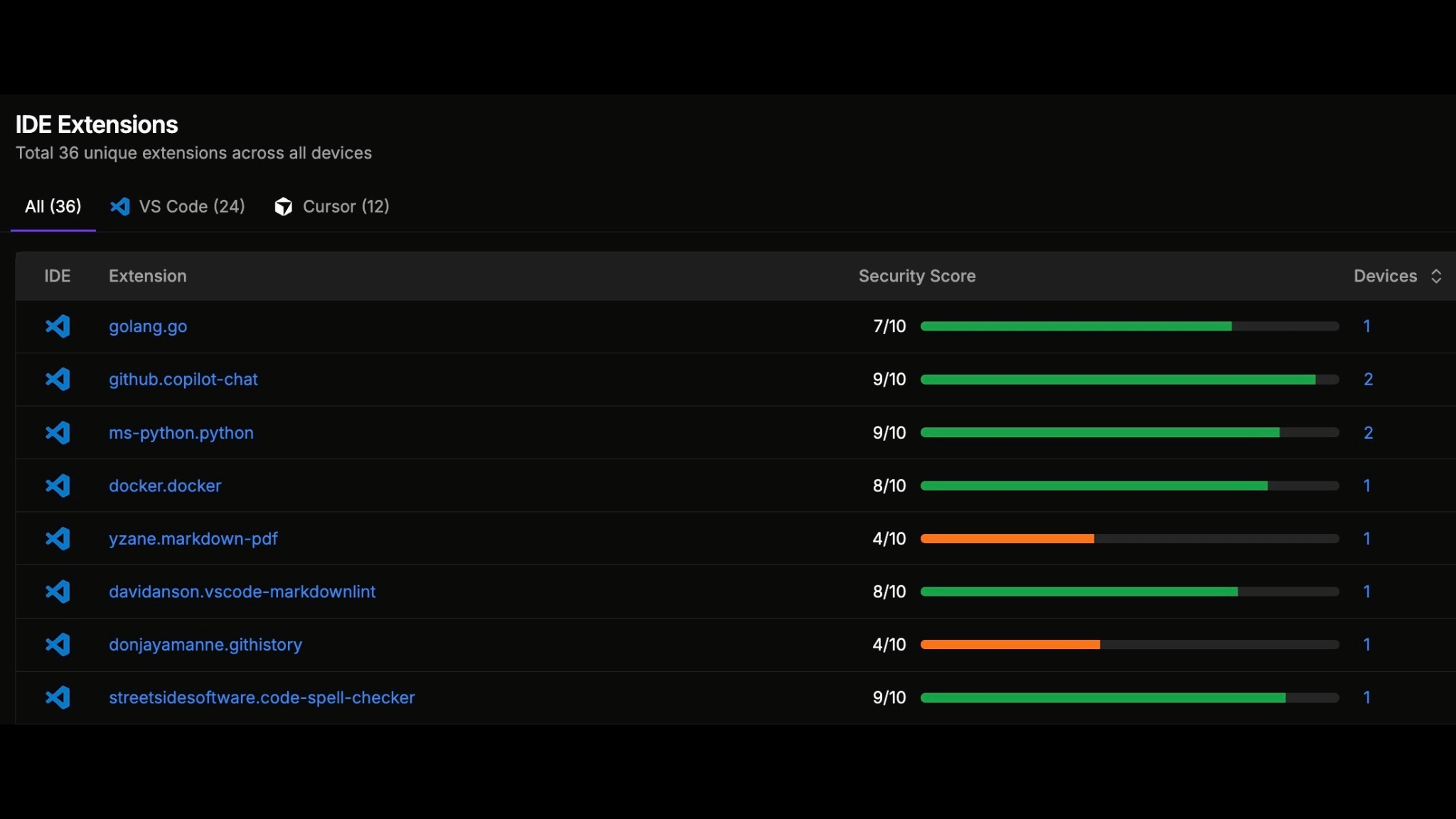
StepSecurity provides complete visibility and control over AI agents, IDE extensions, and dependencies.
Dev Environment
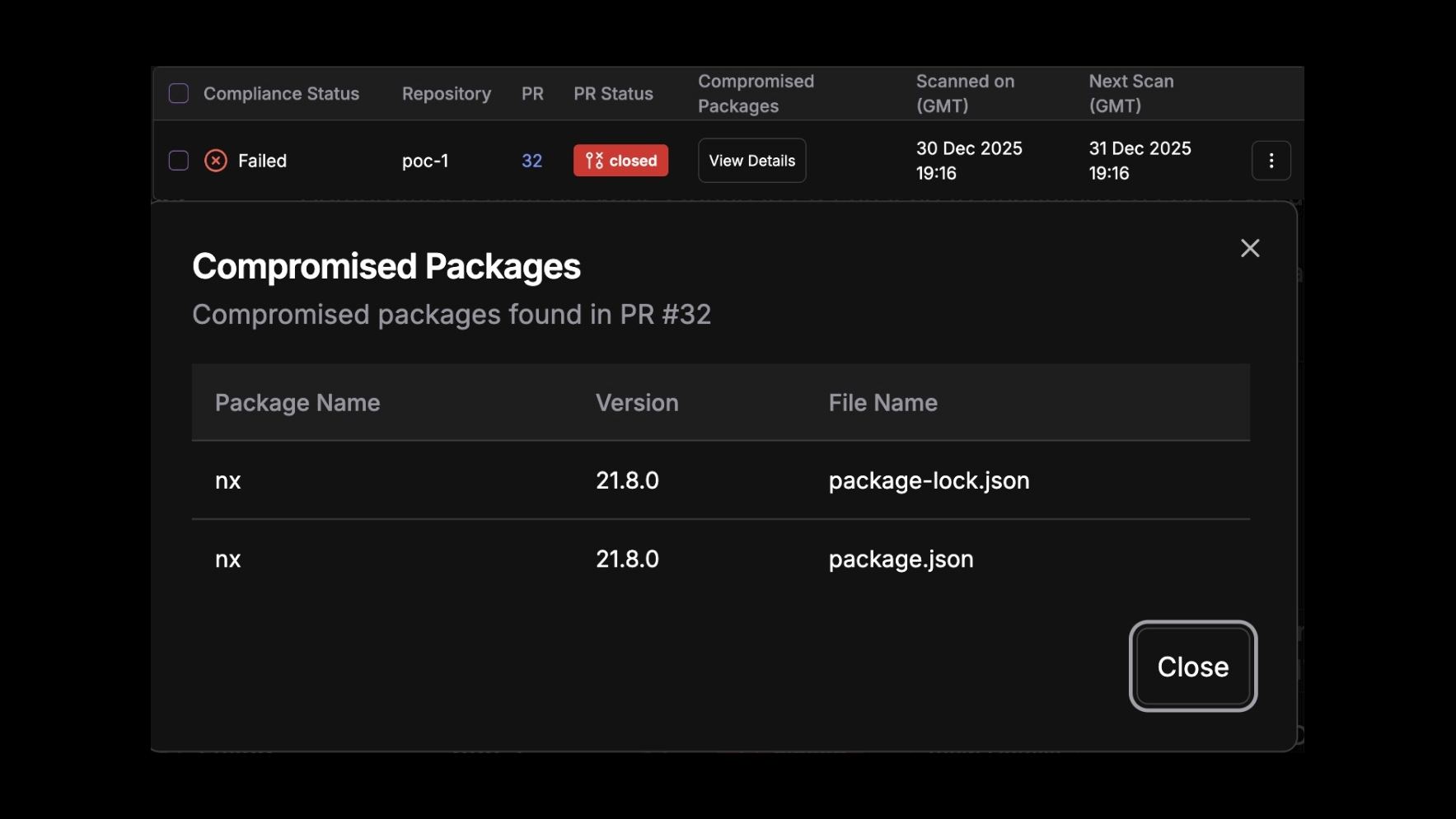
NPM supply chain attacks are escalating.
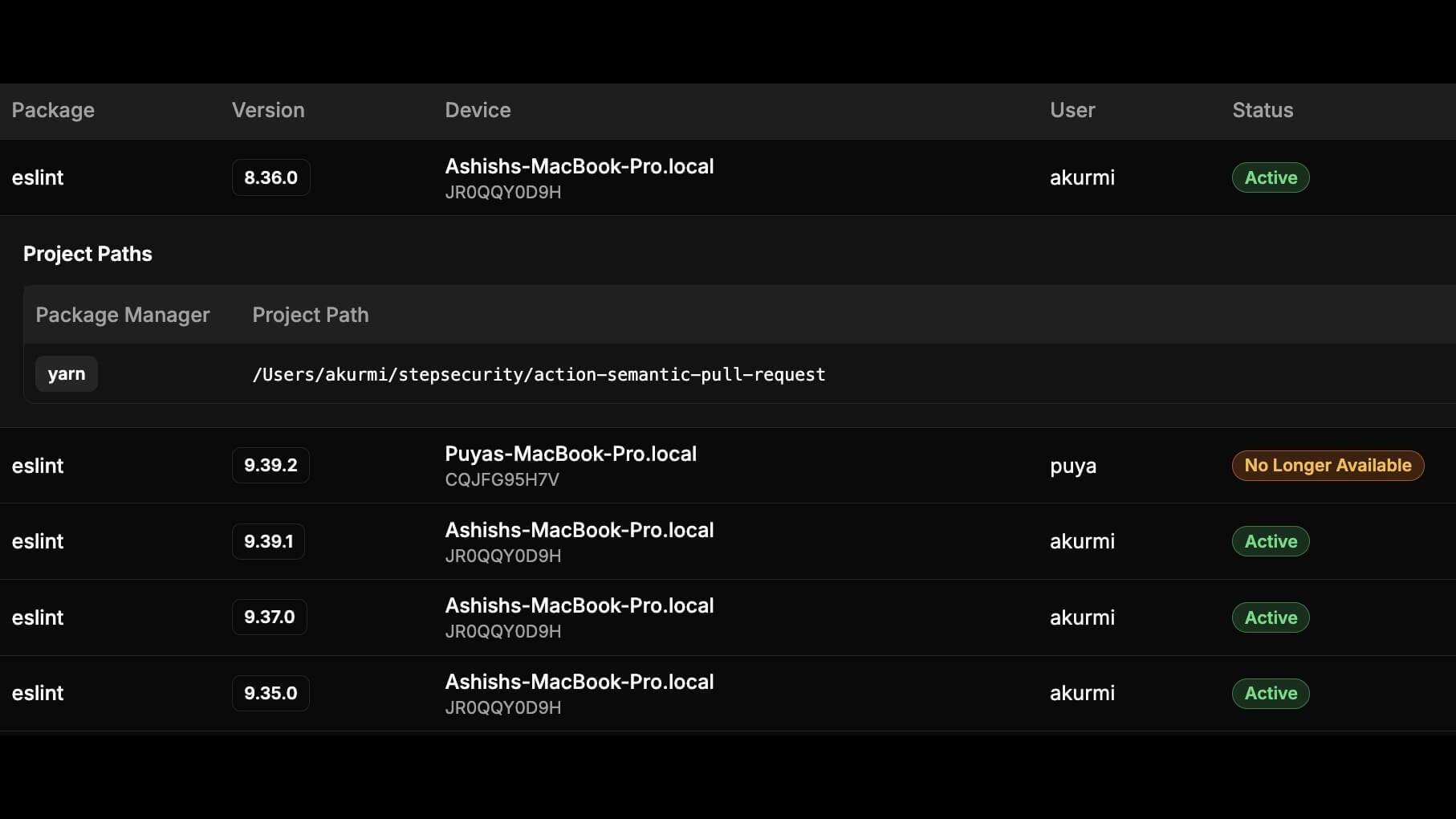
StepSecurity detects compromised npm packages across your organization and prevents them from entering your codebase with proactive controls.
Code Repository
Real-time threat detection and response for your GitHub Actions CI/CD pipelines
CI/CD pipelines have privileged access to production secrets and infrastructure. StepSecurity provides runtime protection with Harden-Runner, a secure internal marketplace for GitHub Actions, and automated remediation, proven in the wild when we detected the tj-actions breach.
GitHub Actions
Case Study
StepSecurity detects a CI/CD supply chain attack on Microsoft’s Azure Karpenter Provider in real-time!
This case study discusses how StepSecurity Harden-Runner detected a CI/CD supply chain attack in real-time in Microsoft’s open-source project Azure Karpenter Provider. Key insights are:
- This could have compromised the cloud environment that the project had access to
- Within an hour of the exploit, StepSecurity reported the detection to the Microsoft Security Response Center (MSRC).
- Microsoft acknowledged StepSecurity for helping detect and remediate the incident
Case Study
StepSecurity Detects CI/CD Supply Chain Attack in Google’s Open-Source Project Flank in Real-Time
This case study discusses how StepSecurity Harden-Runner detected a CI/CD supply chain attack in real-time in Google’s open-source project Flank. Key Insights are:
- This could have caused an XZ Utils and SolarWinds style software supply chain attack.
- The researcher exploited a Pwn Request Vulnerability to exfiltrate CI/CD credentials
- Harden-Runner detected this malicious outbound network call in real-time

Why Step Security
Experience the StepSecurity Difference
Without StepSecurity
- AI coding agents operate without security controls
- No visibility into developer machine supply chain risks
- Reactive response to npm package compromises
- No runtime monitoring for GitHub Actions Runners
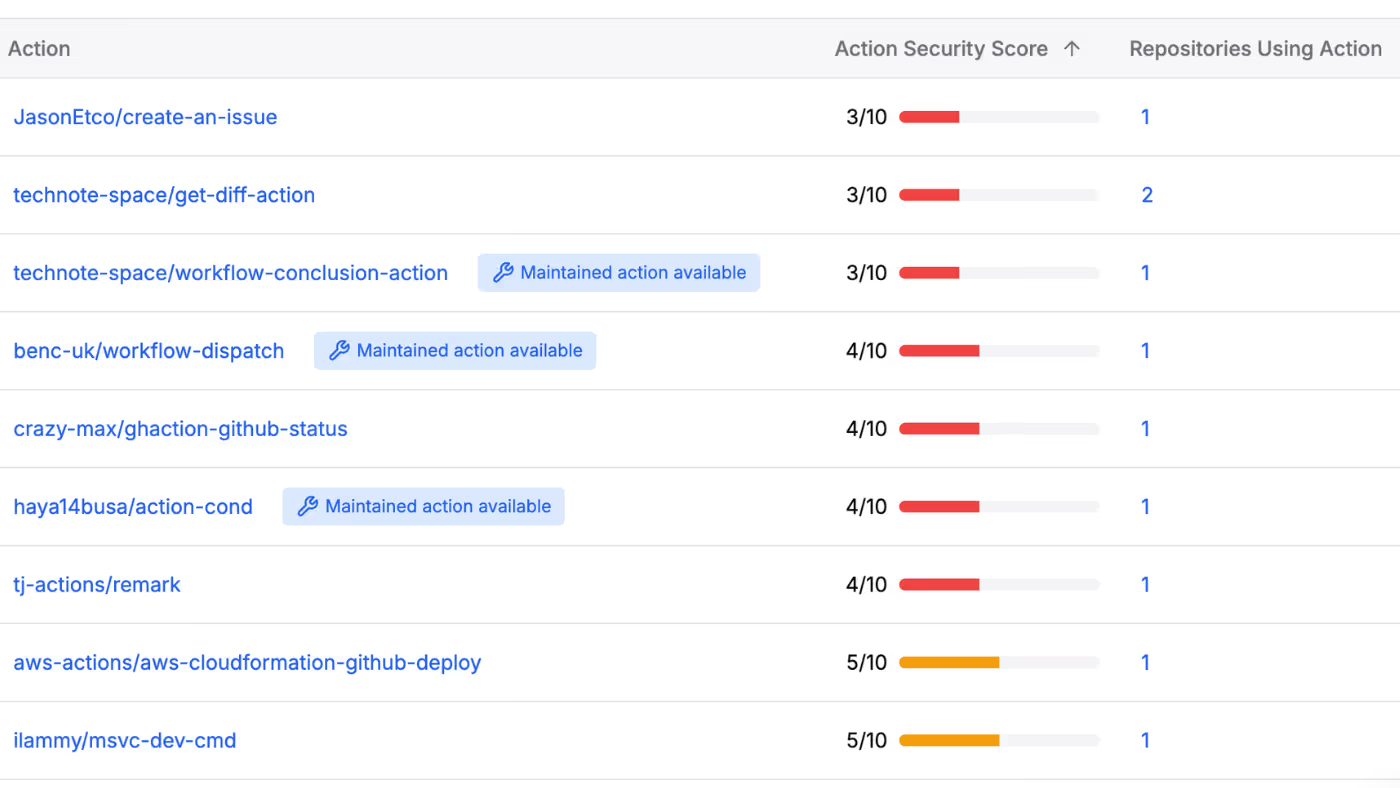
- Manual vetting of third-party actions and dependencies
With StepSecurity
- AI agent and MCP server monitoring and control
- Complete visibility from dev environment to production
- Proactive detection of compromised npm packages
- Real-time threat detection and response for GitHub Actions Runners
- Automated security policies and remediation

.png)