We're excited to introduce a new feature to our egress policy management in StepSecurity Harden Runner: the ability to use wildcard domains in block mode. This new feature was developed in response to direct user feedback, showcasing our commitment to addressing our users' needs. Before delving into this new feature, it's crucial to understand what Harden Runner is.
Harden Runner is a security agent for GitHub-hosted and Actions Runner Controller (ARC) based self-hosted GitHub Actions runners designed to block egress traffic and detect code overwrite, thereby preventing potential breaches, like the SolarWinds or the Codecov incidents. It fortifies your CI/CD pipeline by providing granular controls over network traffic and detecting tampering of files during release builds.
Now, with wildcard domain support in block mode, Harden Runner is even more powerful and flexible. This feature allows you to add wildcard domains to the allowed list and conveniently manage egress traffic.
See It in Action: Video Demo
The following video provides a step-by-step guide on how to effectively use wildcard domains in block mode.
Practical Application: Container Images from the Microsoft Container Registry
Previously, without wildcard support, you would need to explicitly state every subdomain to which you wanted to allow egress traffic. But now, with wildcard support, you can allow egress traffic to all subdomains with a single rule, simplifying the process of managing and configuring egress policies.
One of the scenarios where support for wildcard domains will come in handy is when using container images from mcr.microsoft.com. While mcr.microsoft.com is used for content-discovery, region-specific content-delivery endpoints are required to download image blobs. These endpoints follow the structure: <region>.data.mcr.microsoft.com.
In this case, using a wildcard in the allowed list can be incredibly beneficial. Rather than having to individually specify each region-specific endpoint in your policy, you can simply include *.data.mcr.microsoft.com:443 to allow egress traffic to all these endpoints.
Implementing Wildcard Domains: An Example
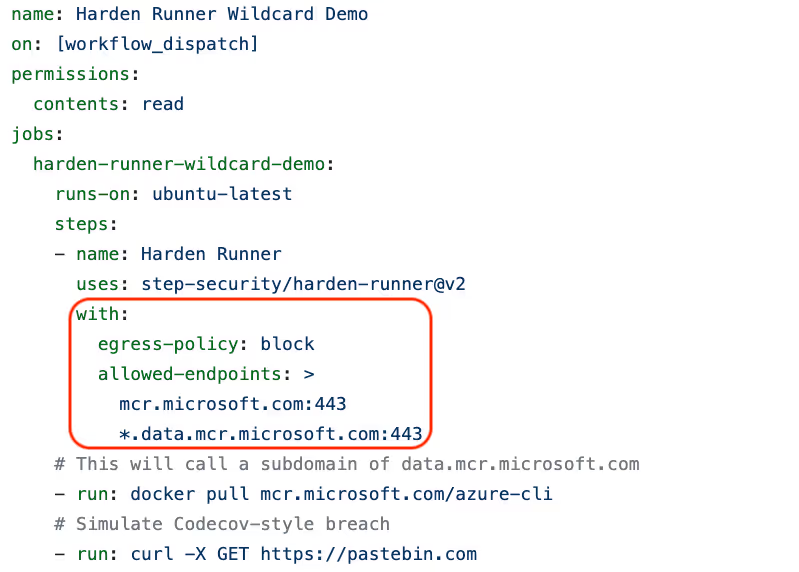
Let's take a look at an example of how to use this feature. Consider the following egress policy:
steps:
- name: Harden Runner
uses: step-security/harden-runner@v2
with:
egress-policy: block
allowed-endpoints: >
mcr.microsoft.com:443
*.data.mcr.microsoft.com:443
# This will call a subdomain of data.mcr.microsoft.com
- run: docker pull mcr.microsoft.com/azure-cli
# Simulate Codecov-style breach
- run: curl -X GET https://pastebin.com
In this YAML file, egress-policy is set to block, which means all outbound connections are blocked by default. The allowed-endpoints field then specifies a list of endpoints to which outbound connections are allowed. The inclusion of *.data.mcr.microsoft.com:443 as an allowed endpoint means that egress traffic will be allowed to all subdomains of data.mcr.microsoft.com on port 443.
Closing Thoughts
We're proud to say that the inspiration for this feature came directly from our users. We constantly listen to their valuable feedback and work hard to implement the features they request. This specific enhancement was suggested in Issue #236 on our GitHub repository.
We encourage you to experience the benefits of this feature firsthand. Try out Harden Runner today by visiting our GitHub repository and see how it can secure your CI/CD pipeline.

.png)

.png)
