At StepSecurity, our mission remains clear: make CI/CD pipelines secure by default. Today, we're proud to announce that Harden-Runner now protects over 9,000 open-source repositories—a milestone reached just two months after passing the 8,000 mark. This rapid growth reflects the growing recognition that CI/CD security is no longer optional.
Harden-Runner is essentially an EDR solution for CI/CD runners. Just as traditional EDR protects endpoints like laptops and servers by monitoring activity, detecting threats, and enforcing protections, Harden-Runner extends the same security model to CI/CD runners. It continuously observes workflows, inspects runtime behavior, and blocks malicious activity
We're now monitoring over 12 million jobs per week across workflows from individual developers to Fortune 500 companies. This sustained growth signals a fundamental shift in how organizations approach pipeline security: from reactive incident response to proactive, continuous protection.
OWASP Elevates Supply Chain Security: CI/CD Pipelines Are Now a Top 10 Risk
The latest 2025 OWASP Top 10 introduces a major shift:
“A03: Software Supply Chain Failures” has been added and was ranked the #1 concern in the global community survey.
For the first time, OWASP explicitly calls out CI/CD pipelines as a critical point of failure:
“A complex CI/CD pipeline with weaker security becomes a major supply chain vulnerability.”
This aligns with what we’ve been seeing across the industry.
Attacks no longer target only application dependencies — they increasingly target the build process itself, leveraging trusted automation to inject malicious code, steal credentials, or alter artifacts.
CI/CD pipelines have become one of the highest-value targets because:
- Build systems often run with highly privileged access
- Actions, extensions, and build tools are pulled from third parties
- Many pipelines have no runtime monitoring at all
Traditional security controls — static analysis, dependency scanning, or periodic audits — cannot detect what happens during a CI/CD run.
And this is exactly where modern supply chain attacks are carried out.
Organizations now need runtime visibility and enforcement inside the CI/CD pipeline.
The growing class of threats requires continuous monitoring that adapts to each workflow, understands what “normal” looks like, and can block anomalies or malicious behavior in real time.
OWASP’s recognition formalizes what security teams have felt for years:
Securing CI/CD pipelines is no longer optional — it is foundational to software integrity.
Community Spotlight: Trust at Scale
Through our free Community Tier, we support open-source projects that form the backbone of modern development. Among the 9,000+ repositories now protected by Harden-Runner, we're particularly proud to secure critical infrastructure projects that millions of developers depend on daily.
CrowdStrike Open-Source Projects Adopt Harden-Runner
Another strong signal of the growing need for runtime CI/CD security is the adoption of Harden-Runner across several CrowdStrike open-source projects. CrowdStrike’s engineering teams maintain a wide range of community tools and integrations that are widely used across the security ecosystem — and securing their build pipelines is a critical part of maintaining trust and integrity.
A quick look at GitHub shows multiple CrowdStrike repositories integrating Harden-Runner into their GitHub Actions workflows:
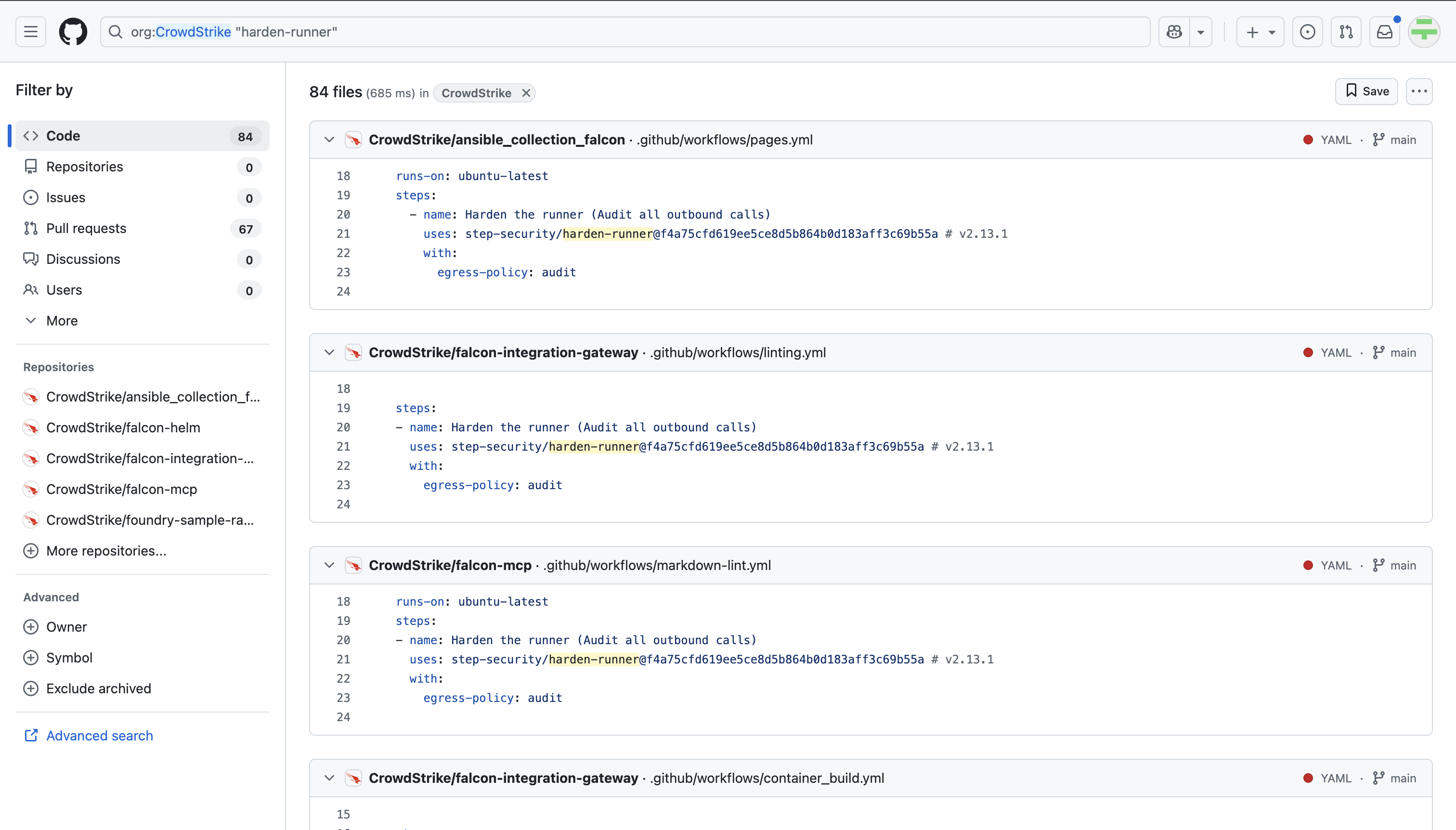
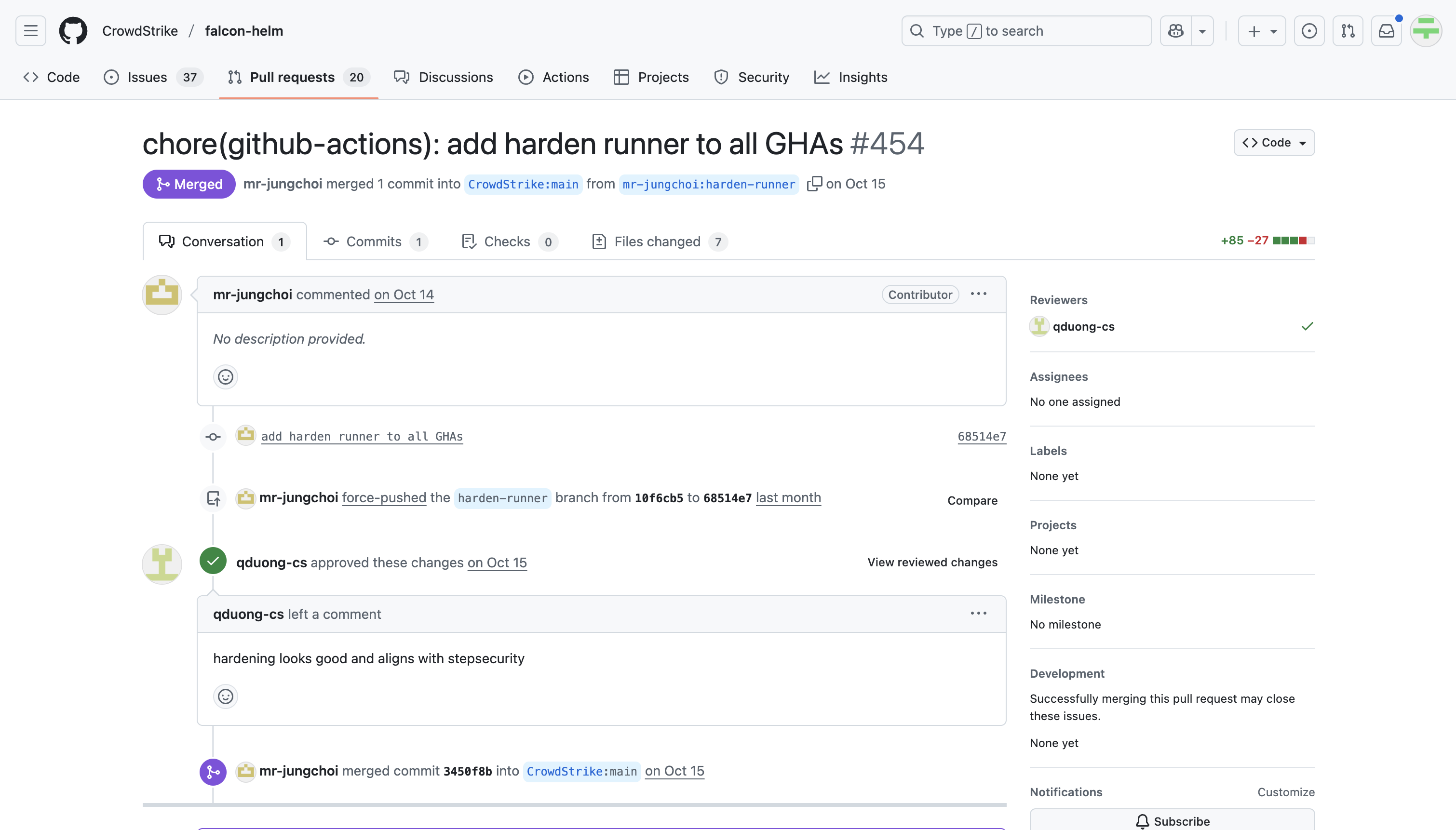
For example, the falcon-helm project added Harden-Runner in this PR:
Kong Open-Source Projects Strengthen CI/CD Security with Harden-Runner
Kong, the company behind one of the world’s most widely adopted API gateways, has also begun integrating Harden-Runner across several of its open-source projects. With Kong’s tooling central to API infrastructure and service connectivity for thousands of engineering teams, protecting the integrity of their build pipelines is mission-critical.
A quick search highlights multiple Kong repositories already adopting Harden-Runner:

One example is the sdk-konnect-go project, which added Harden-Runner in this PR:

TektonCD
A cornerstone of the modern CI/CD ecosystem, TektonCD provides the building blocks for creating powerful, cloud-native pipelines. With Harden-Runner, TektonCD’s workflows gain real-time protection and visibility—ensuring that every pipeline execution is transparent, tamper-resistant, and aligned with the highest security standards.
Explore this interactive demo to see how TektonCD leverages Harden-Runner to secure its GitHub workflow files:
Brotli (Google)
As a widely adopted compression algorithm used across the web—from browsers to CDNs—Brotli’s integrity is vital to global performance and security. By integrating Harden-Runner, the Brotli project benefits from continuous monitoring against supply chain threats, reinforcing trust in one of the most fundamental components of modern web infrastructure.
Explore this interactive demo to see how Brotli leverages Harden-Runner to secure its GitHub workflow files:
What's New: Greater Control and Flexibility
Since reaching 8,000 protected repositories, we've focused on giving teams more control over how Harden-Runner adapts to their unique workflow patterns and expanding platform support to meet growing demand.
Baking Harden-Runner into Custom GitHub Runner Images
GitHub now supports using custom runner images, allowing you to bake StepSecurity’s Harden-Runner directly into your image. With this capability, you no longer need to add the Harden-Runner action to each workflow—simply using the custom image automatically provides built-in runtime protection and monitoring.
Learn more about enabling it in our documentation.
Assign Policies Without Workflow Changes
You can now create and assign policies directly to repositories, jobs, or organizations—without modifying your workflow files.
This streamlines policy management and reduces configuration overhead, making it easier to enforce security standards consistently across environments. Learn more in our documentation.
Customizable Baseline Stability Thresholds
Not all workflows are created equal. High-frequency workflows that run dozens of times daily develop stable patterns much faster than weekly deployment pipelines. We've introduced customizable baseline detection thresholds that let you tune when anomaly detection activates based on your workflow characteristics.
- Run-Based Detection: Set a custom minimum number of workflow runs before anomaly detection begins. The default threshold remains 100 runs for most workflows, but you can adjust it by raising or lowering the limit to better fit your specific use case.
- Time-Based Detection: For workflows that run infrequently but still need protection, enable time-based detection to activate monitoring after a defined number of days. If your deployment workflow only runs weekly but you want protection within 30 days, time-based detection ensures you don't wait for 100 runs to build a baseline.
This flexibility means Harden-Runner adapts to your workflow rhythm instead of forcing your workflows to adapt to rigid thresholds. Learn more about configuring anomaly detection →
Streamlined Policy Creation from Baselines
Managing egress policies used to require manually adding every endpoint your workflows needed. We've simplified this with baseline-to-policy conversion, making it effortless to move from audit mode to enforcement.
Now, when creating policies in the Policy Store, you can automatically import all endpoints from an established baseline. Instead of manually transcribing dozens of domains, you can convert your proven workflow patterns directly into enforceable policies.
This approach combines the precision of established baselines with the convenience of centralized policy management, making it easier to enforce least privilege access across your entire organization. Learn more about creating policies from baselines →
Expanding Platform Support: macOS and Windows on the Horizon
While Linux runners have been our primary focus, we recognize that many teams rely on macOS and Windows environments for specific build requirements. We're actively developing Harden-Runner support for both platforms and are looking for design partners to help shape these implementations.
If your organization uses macOS or Windows self-hosted runners and wants early access to Harden-Runner capabilities for these platforms, we'd love to work with you. Design partners will get:
- Early access to macOS and Windows Harden-Runner builds
- Direct input on feature prioritization and implementation
- Dedicated support during the testing phase
- Recognition as a launch partner when we announce general availability
Interested in becoming a design partner? Reach out to us
Looking Forward: Building Momentum
Reaching 9,000 protected repositories isn't just a number—it represents thousands of teams choosing proactive security over reactive incident response. Key insights from this growth phase:
- Flexibility matters: Teams need security tools that adapt to their workflows, not one-size-fits-all solutions
- Visibility drives adoption: When developers understand what's happening in their pipelines, they embrace security controls
- Platform diversity is critical: Supporting teams wherever they build, whether on Linux, macOS, or Windows
Take Action: Secure Your Workflows Today
🔒 Ready to Join 9,000+ Protected Repositories?
Get started with Harden-Runner using our Secure Workflow tool—free through our Community Tier. It automatically integrates Harden-Runner into your GitHub Actions with minimal configuration.
Whether you're securing a solo project or enterprise infrastructure, Harden-Runner delivers the runtime visibility and control modern CI/CD demands.
Become part of the next wave, follow this interactive demo to see how to add Harden-Runner to your workflow:
Together, we're building a future where secure CI/CD is the default, not the exception.
.png)



