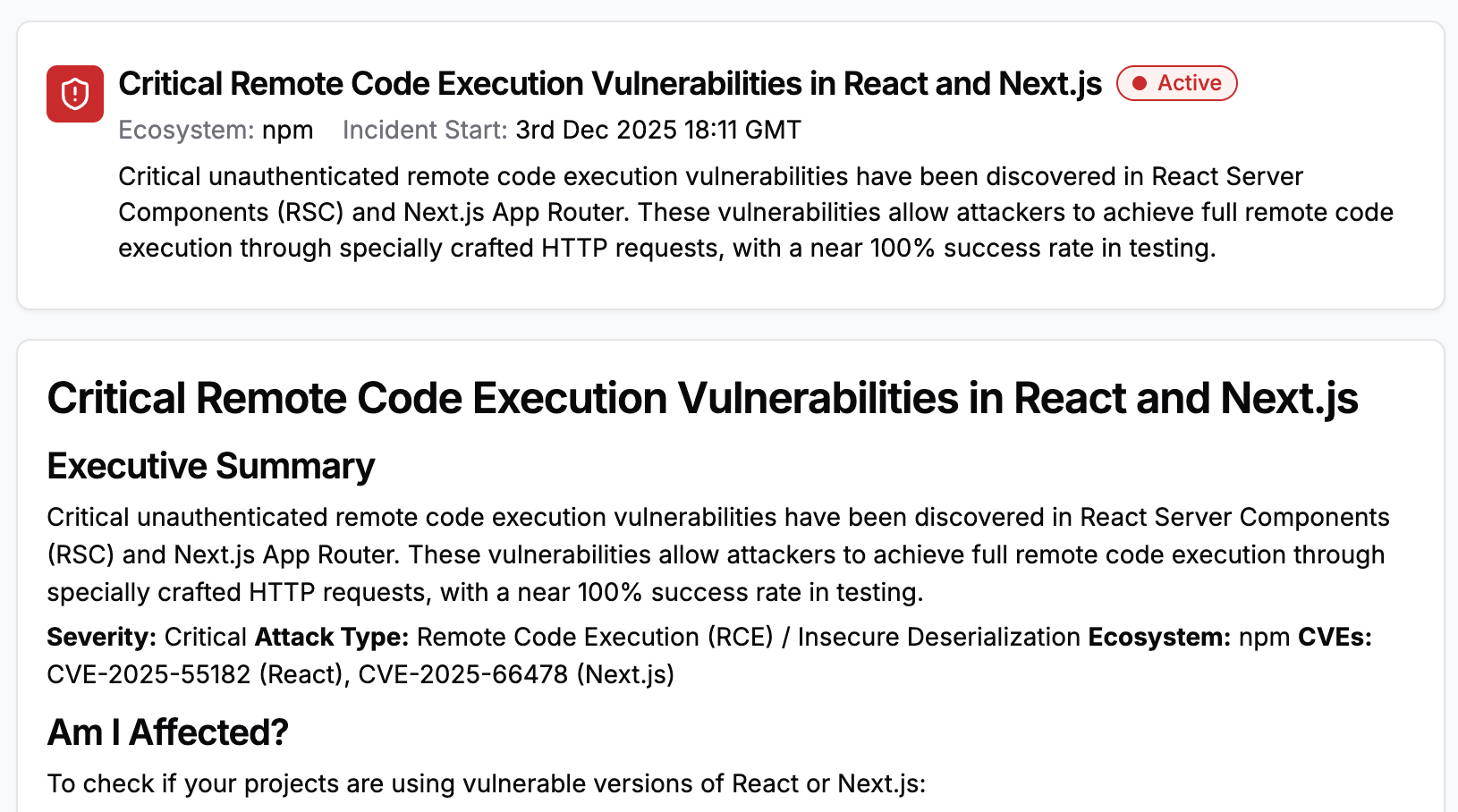
The React Core Team and Vercel have disclosed critical security vulnerabilities affecting React Server Components (RSC) and Next.js App Router that enable unauthenticated remote code execution through specially crafted HTTP requests. These vulnerabilities, tracked as CVE-2025-55182 (React) and CVE-2025-66478 (Next.js), pose an immediate threat to applications using React Server Components.
Understanding the Vulnerability
The root cause lies in insecure deserialization within the React Server Components "Flight" protocol. When servers process RSC payloads, insufficient input validation allows attacker-controlled data to influence server-side execution logic. According to the React Core Team's disclosure, this creates a reliable attack vector with near 100% success rate in testing environments.
The vulnerability is particularly concerning given its scope. Research from Wiz reveals that 39% of cloud environments contain instances of Next.js or React in vulnerable versions, while 44% of all cloud environments have publicly exposed Next.js instances—creating a massive attack surface for threat actors.
Affected Versions
Impact
Applications using affected versions of the React Server Components implementation may process untrusted input in a way that allows an attacker to perform remote code execution. The vulnerability is present in the following React Server Components packages:
- react-server-dom-parcel (19.0.0, 19.1.0, 19.1.1, and 19.2.0)
- react-server-dom-webpack (19.0.0, 19.1.0, 19.1.1, and 19.2.0)
- react-server-dom-turbopack (19.0.0, 19.1.0, 19.1.1, and 19.2.0)
These packages are embedded in the following frameworks and bundlers:
- Next.js using App Router with versions ≥14.3.0-canary.77, ≥15 and ≥16
- Other frameworks and plugins that embed or depend on React Server Components implementation, including Vite, Parcel, React Router, RedwoodSDK, and Waku
React:
- 19.0 (patched in 19.0.1)
- 19.1 (patched in 19.1.2)
- 19.2 (patched in 19.2.1)
Next.js App Router:
- 14.3.0-canary through 14.3.0-canary.87 (patched in 14.3.0-canary.88)
- 15.0.0 through 15.0.4 (patched in 15.0.5)
- 15.1.0 through 15.1.8 (patched in 15.1.9)
- 15.2.0 through 15.2.5 (patched in 15.2.6)
- 15.3.0 through 15.3.5 (patched in 15.3.6)
- 15.4.0 through 15.4.7 (patched in 15.4.8)
- 15.5.0 through 15.5.6 (patched in 15.5.7)
- 16.0.0 through 16.0.6 (patched in 16.0.7)
Identifying Your Exposure
StepSecurity provides tools to quickly identify vulnerable packages across your organization:
NPM Package Search: Use our tenant-wide package search to locate all instances of affected React and Next.js versions across your repositories.
Threat Center Monitoring: StepSecurity's Threat Center provides real-time alerts for critical vulnerabilities like these, enabling rapid response when new threats emerge in your dependency chain.
Immediate Remediation Steps
- Upgrade immediately to patched versions of React (19.0.1, 19.1.2, or 19.2.1) and Next.js (see version table above)
- Verify your upgrades using
npm list reactandnpm list next - Review indirect dependencies that may bundle vulnerable React versions
- Monitor for exploitation attempts in your application logs
Important Note on NPM Cooldown Check
The StepSecurity NPM Cooldown check, which helps protect against supply chain attacks by flagging recently released packages, will initially fail for these patched versions. The StepSecurity Research Team has reviewed and verified these security patches as safe. You can approve the failed cooldown checks for these specific versions through the StepSecurity platform.
Additional Resources
For detailed technical analysis and proof-of-concept information:
- React Core Team Security Advisory
- Vercel Security Update
- Wiz Research: Critical Vulnerability in React