Trusted By Enterprises Worldwide















NPM Supply Chain Threats
The Growing NPM Security Crisis Threatening Your Applications

November 23, 2025
Shai-Hulud - The Second Coming
Self-Propagating Malware
Supply Chain Attack Compromises Zapier and ENS Ecosystems, creates 22,000+ repositories with exfiltrated secrets

September 15, 2025
Shai-Hulud
Self-replicating malware compromised 500+ packages, stealing credentials from developer environments.

August 27, 2025
S1ngularity - Nx Package Breach
Build Tool Compromise
The first known case where malware harnessed developer-facing AI CLI tools.

Comprehensive NPM Protection
The Complete Platform for
NPM Supply Chain Security
Prevent
Stop NPM supply chain attacks before they reach your codebase. Proactive controls block malicious packages and anomalies at the source.
01
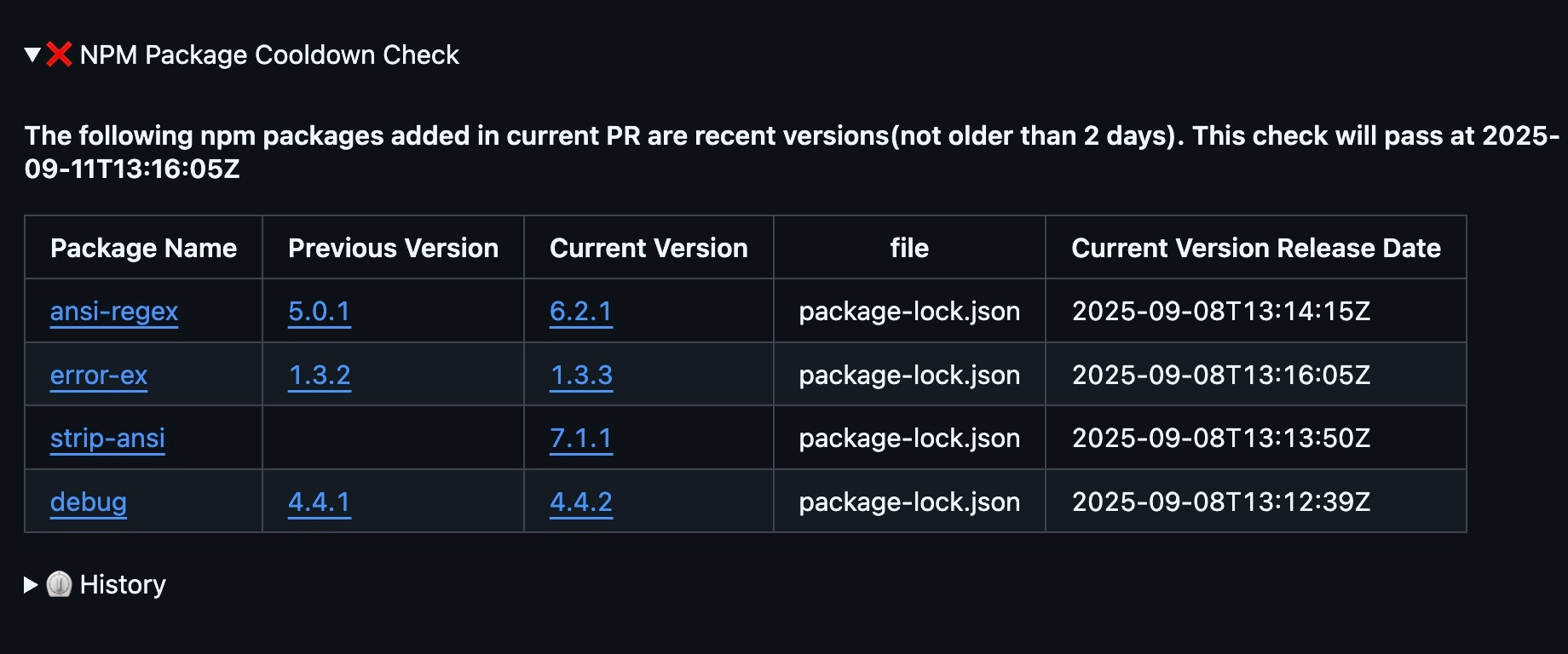
Cooldown Period for New Packages
Block newly published NPM packages for a configurable period. Most supply chain attacks exploit fresh packages before the community can review them as cooldown policies give you time to verify legitimacy.
02
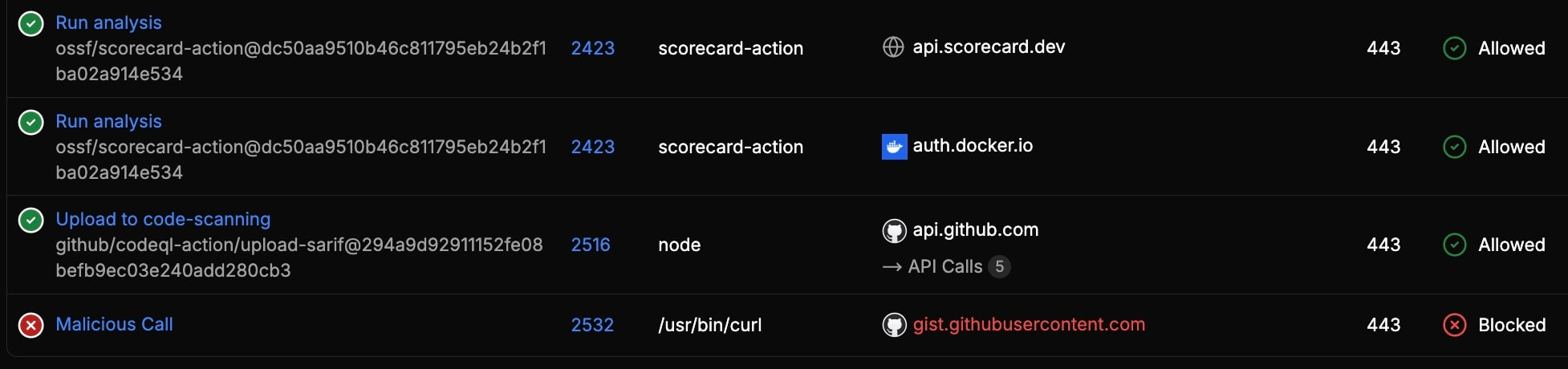
Harden-Runner Network Block Policies
Prevent anomalous network calls at runtime in your CI/CD pipelines with egress network policies. Block malicious exfiltration attempts and unauthorized outbound connections before secrets can be stolen.
03
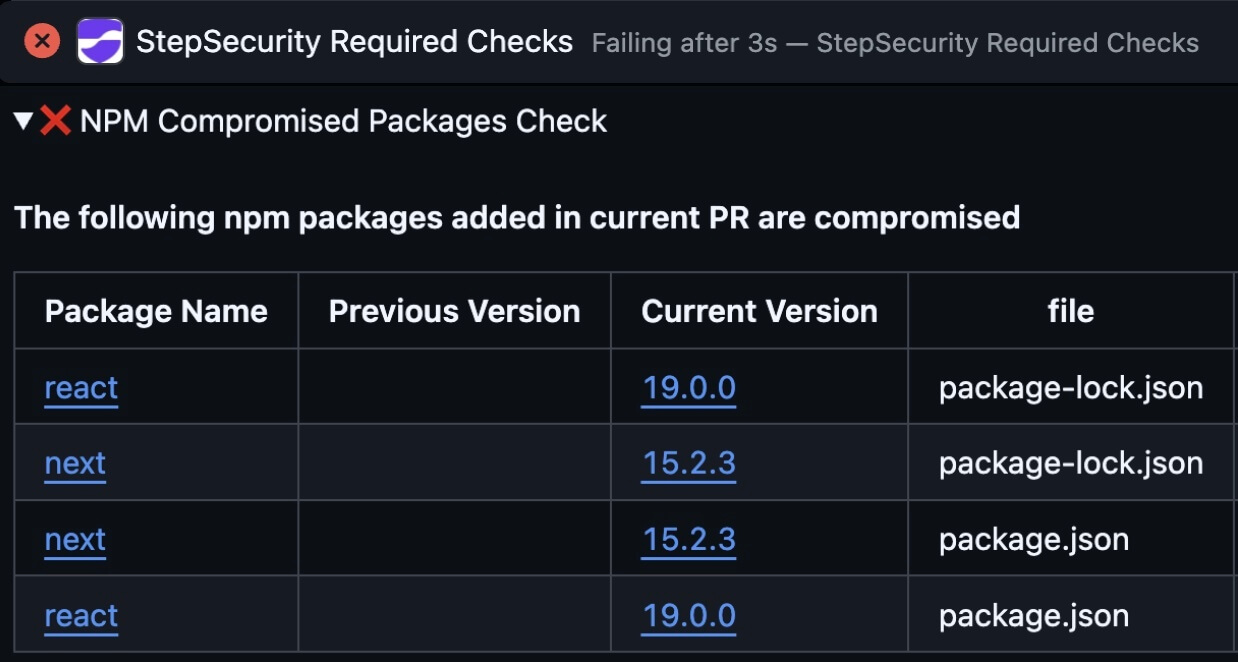
PR Block Policies
Automatically block pull requests that introduce known compromised or suspicious NPM packages. Enforce security policies at the PR level to prevent malicious dependencies from ever being merged.
Detect
Identify compromised packages and supply chain threats across your entire organization. Continuous monitoring, expert research, and automated scanning ensure nothing slips through.
01
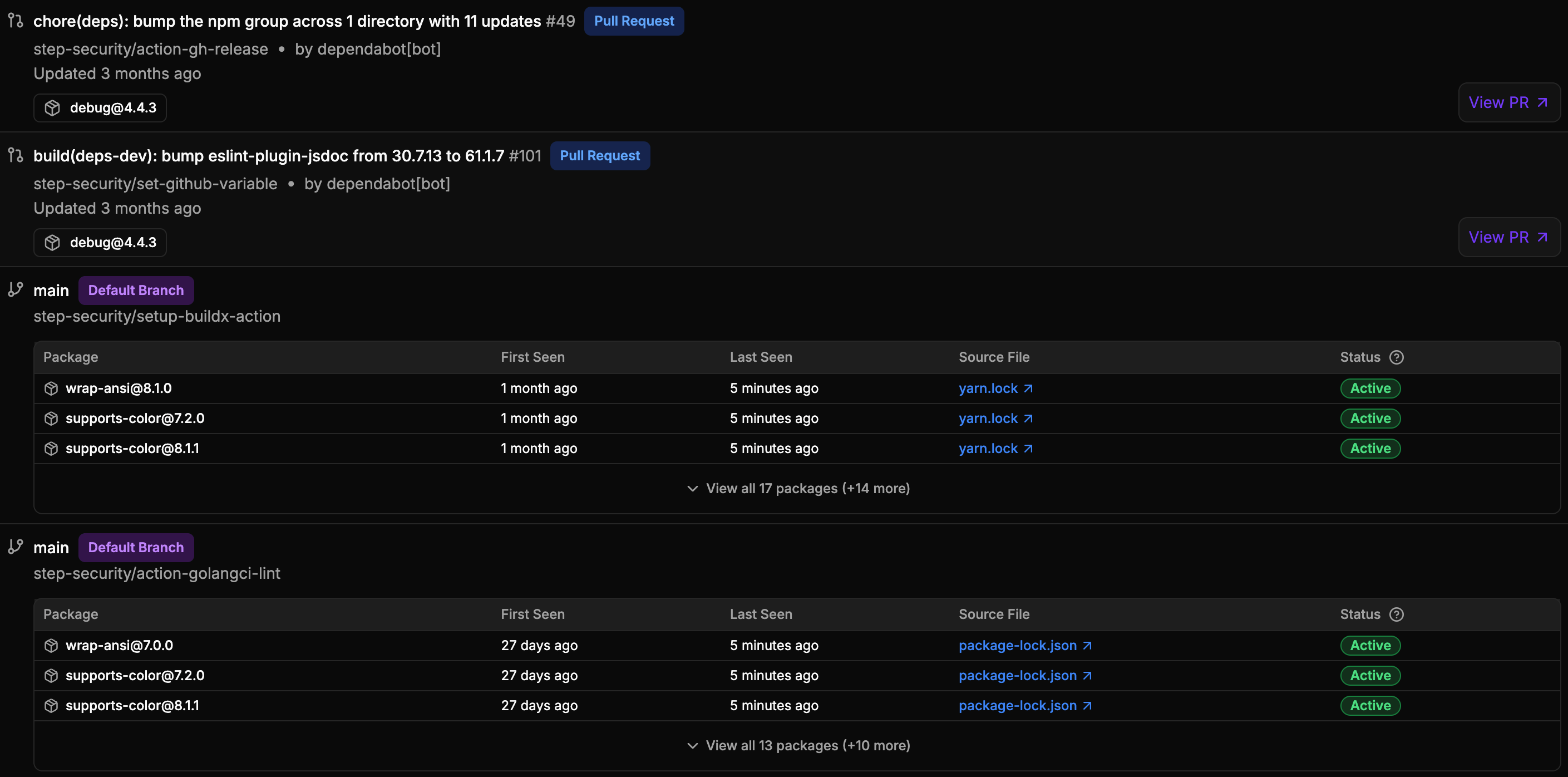
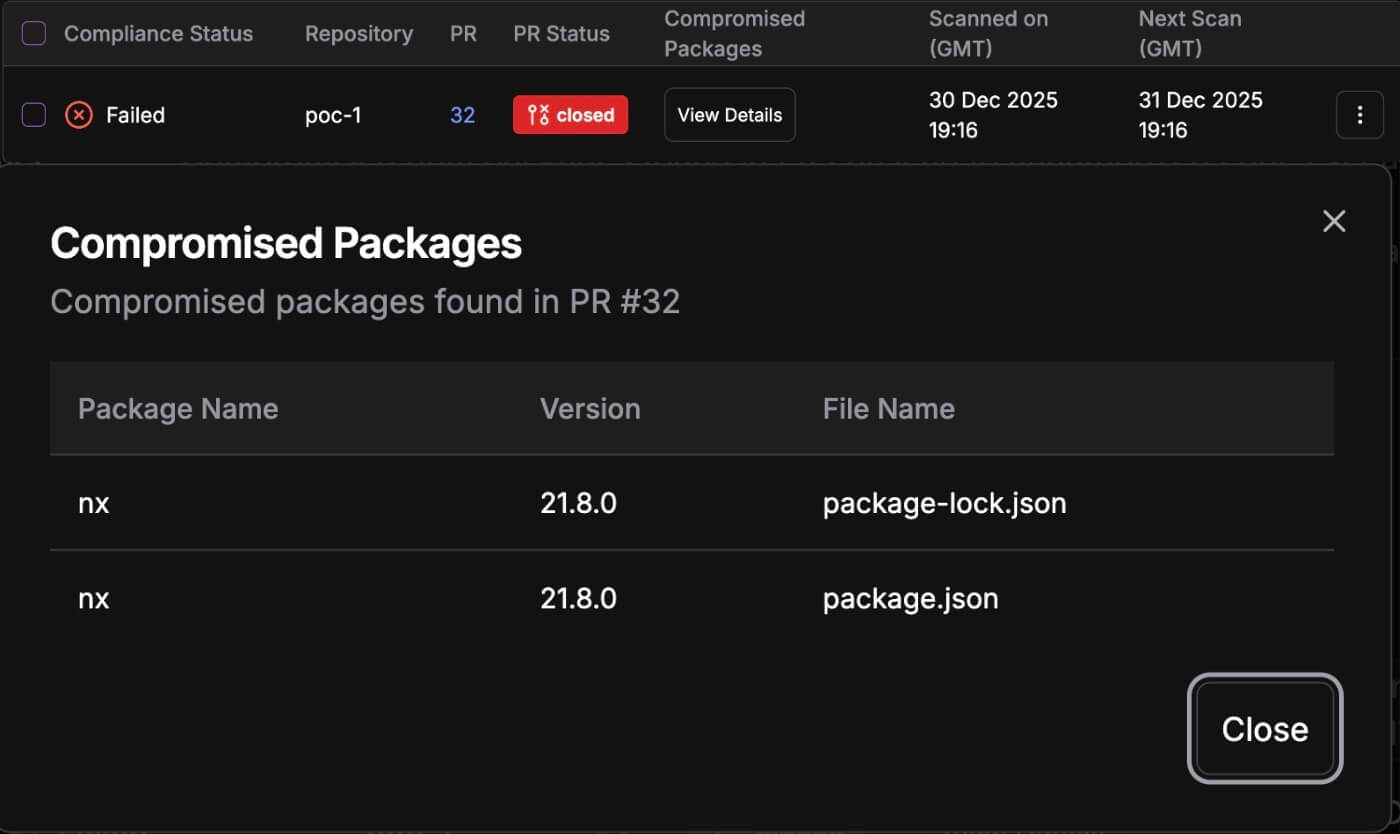
Compromised NPM Packages in PR Control
Automatically detect when pull requests introduce compromised NPM packages. Get instant alerts and detailed context on the threat, enabling your team to take action before merge.
02
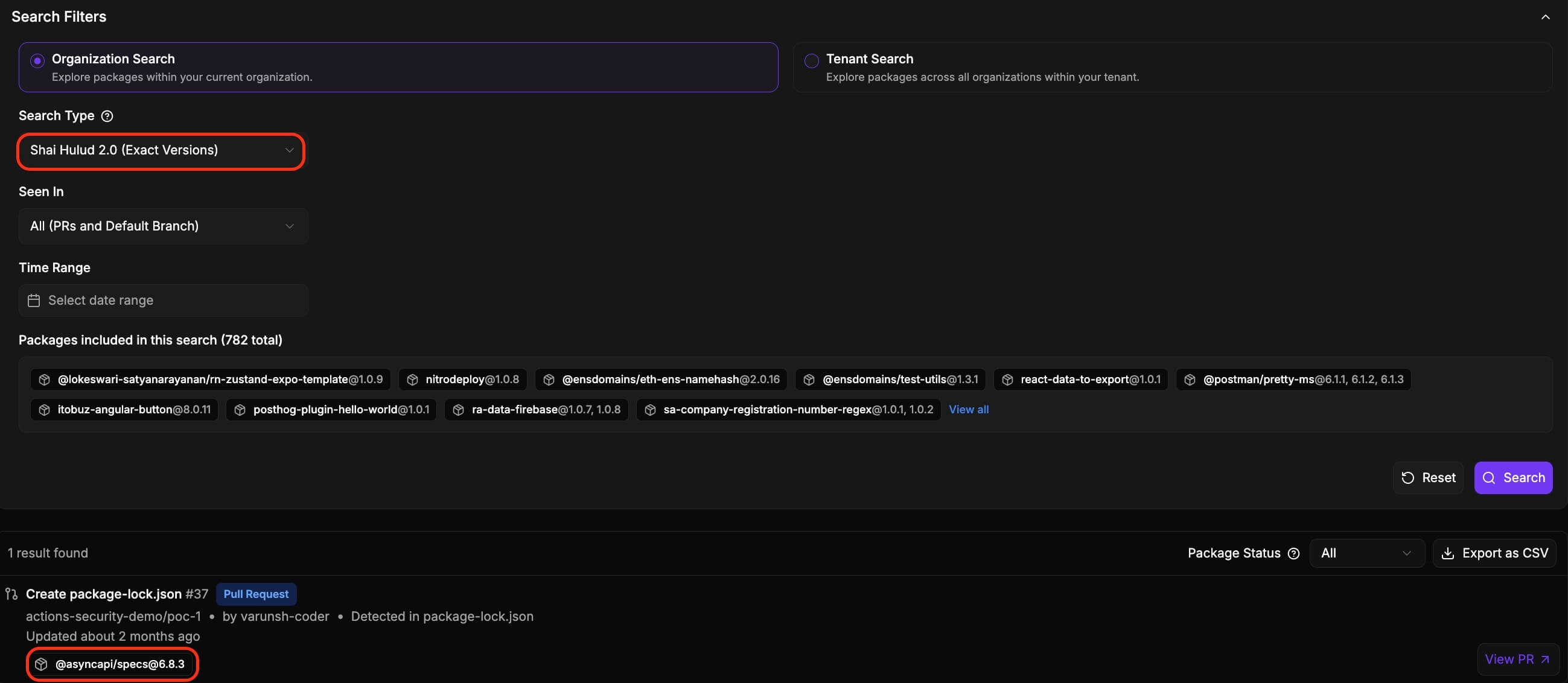
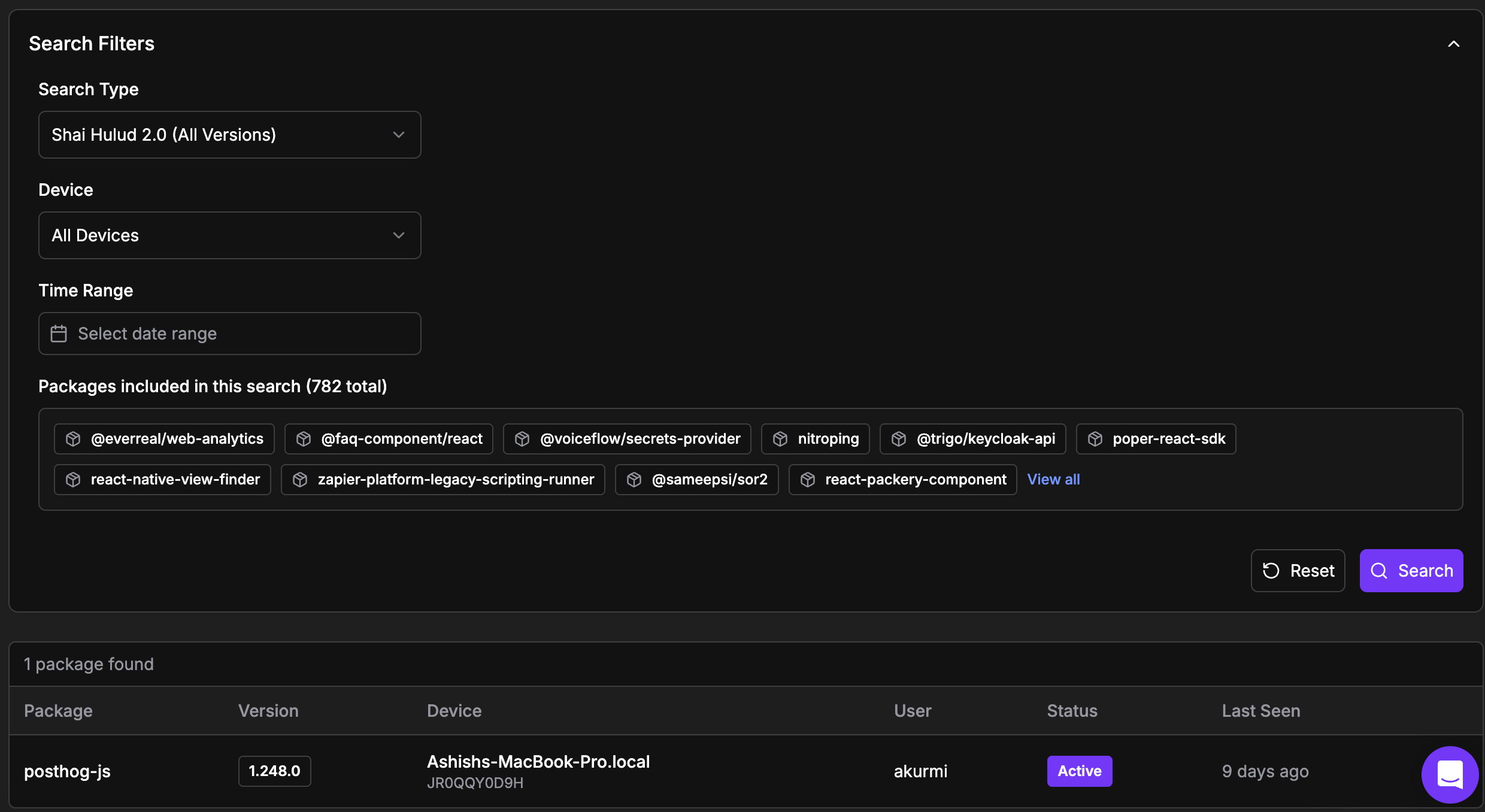
Enterprise-Wide NPM Package Search
Instantly identify every instance of a specific NPM package across your organization’s default branches and PR’s, enabling rapid assessment and response during supply chain incidents
03
Historical Dependency Timeline
Track your dependency history over time to detect if you were vulnerable in the past. Even if a malicious package has been removed, understand your historical exposure window.
04
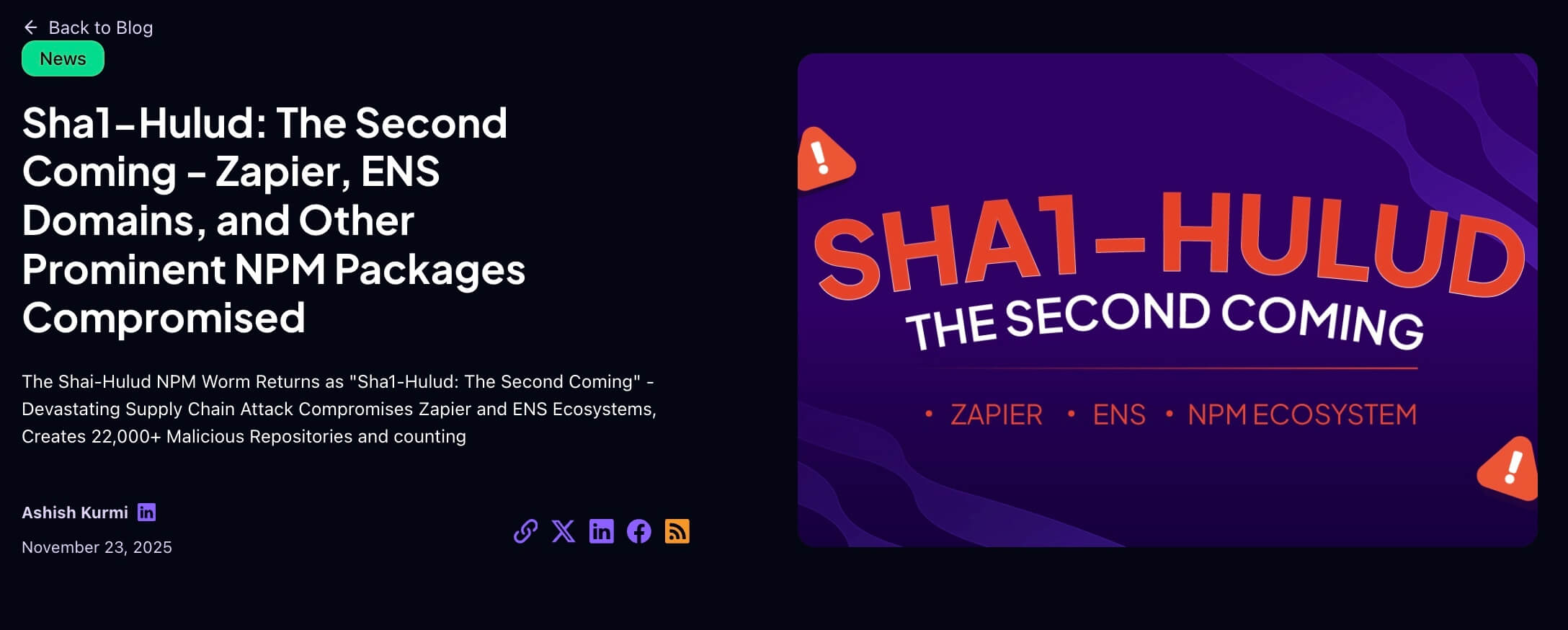
StepSecurity Research Team & Detection Systems
Benefit from our dedicated security research team and automated detection systems. StepSecurity is often first to detect major NPM attacks—like Shai-Hulud and S1ngularity—providing early warning before widespread impact.
05
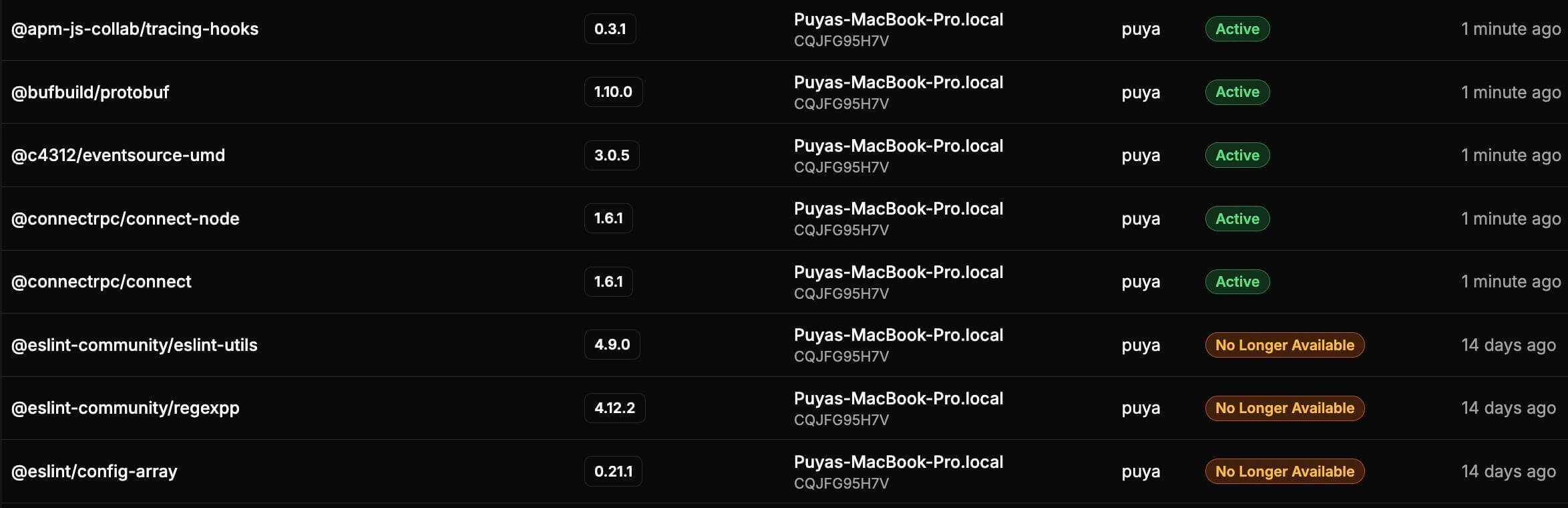
Developer Machine Dependency Monitoring
Extend detection beyond CI/CD to developer machines. Monitor npm packages installed locally across your organization's workstations to identify compromised dependencies before they're used in development.
Respond
When incidents happen, respond faster with actionable threat intelligence and organization-wide visibility. Reduce MTTD and MTTR with centralized tools designed for rapid incident response.
01
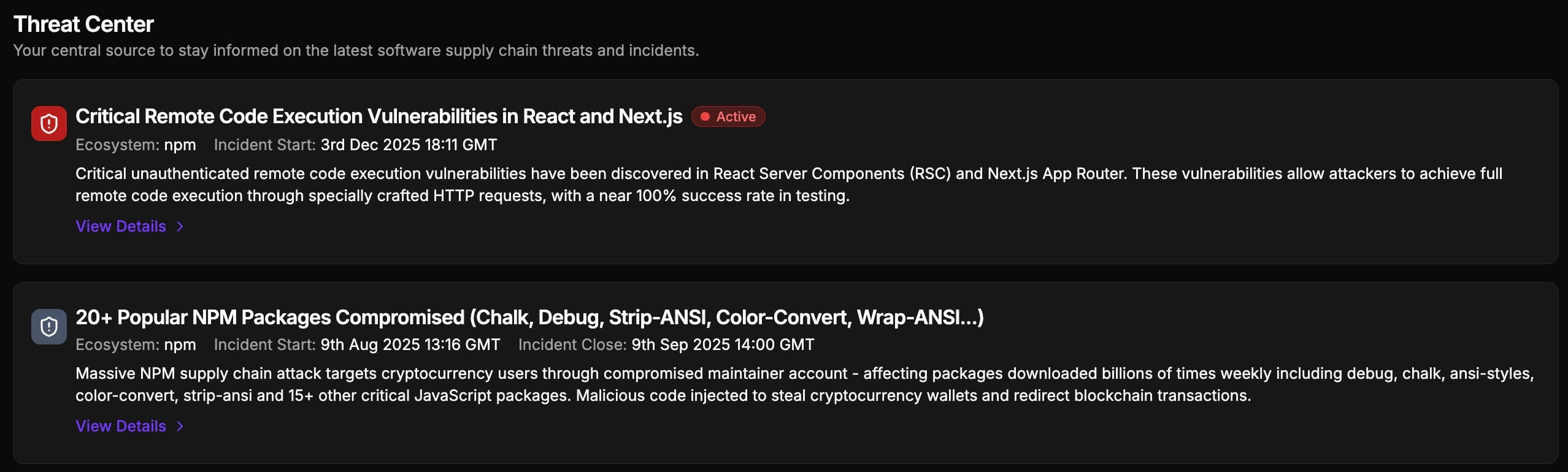
Threat Intelligence & Threat Centre
Access real-time threat intelligence with detailed technical analysis, IOCs, and remediation guidance. Our Threat Centre provides centralized, automated visibility into the latest supply chain compromises affecting your organization.
02
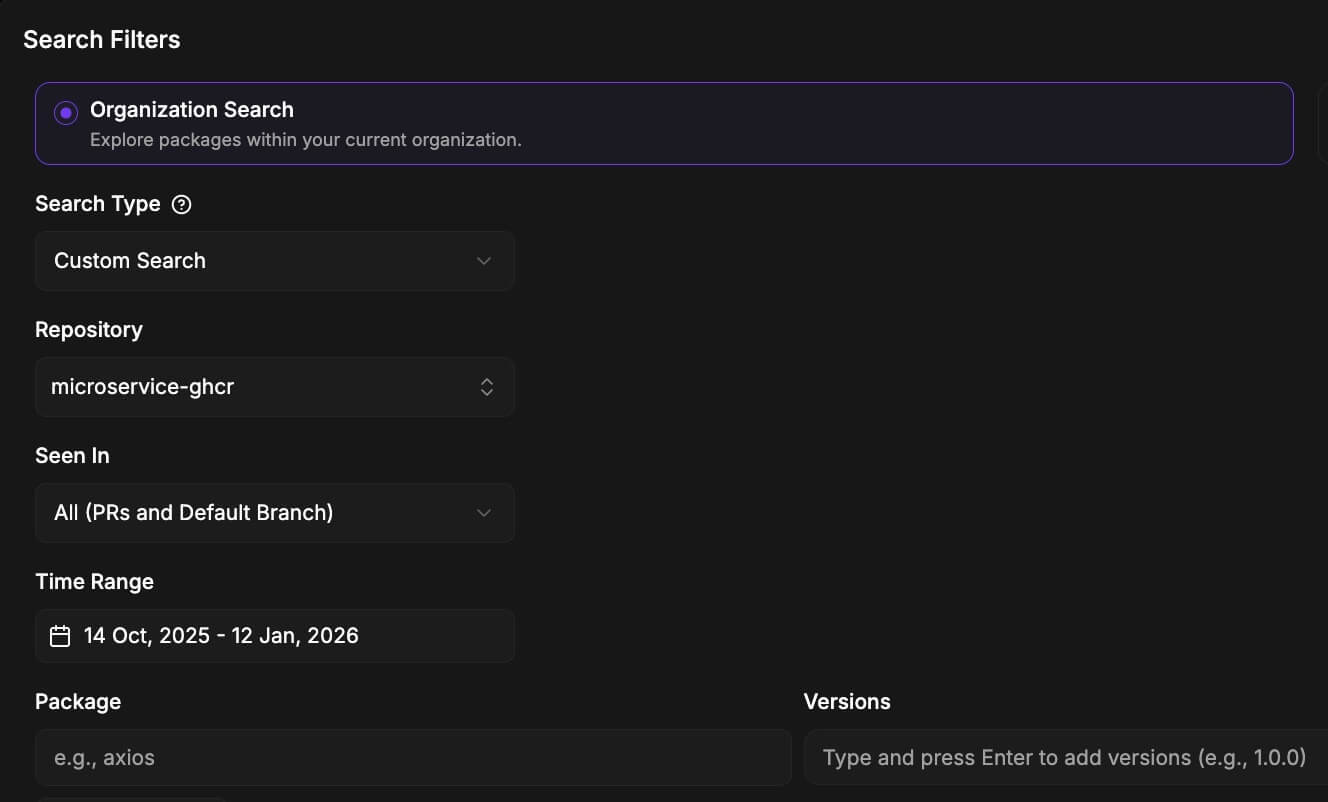
NPM Package Search for Impact Assessment
When a new compromise is discovered, instantly search across your entire organization to assess impact. Identify all affected repositories and prioritize remediation efforts based on real exposure.
03
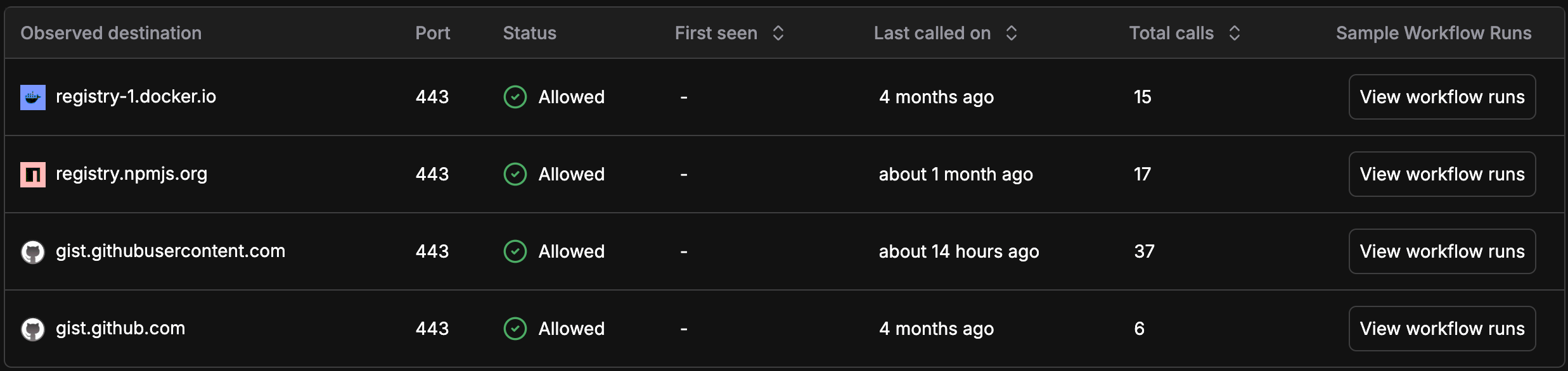
Harden-Runner Network Baselines
Search for malicious domains and suspicious network activity across your organization using Harden-Runner network baselines. Identify if any CI/CD workflows have communicated with known malicious infrastructure.
04
Secure Developer Machines from Compromised Packages
Take immediate action when compromised npm packages are detected on developer workstations. Remotely remove malicious dependencies from affected machines across your organization to stop credential theft and contain the blast radius.

Why Step Security
Experience the StepSecurity Difference
Without StepSecurity
With StepSecurity
Protect Your NPM Supply Chain Today
Stop supply chain attacks before they compromise your applications, credentials, and infrastructure. Gain deep visibility into your NPM dependencies, detect malicious packages early, and enforce security controls across your build and deployment pipelines to keep your software trustworthy and resilient.