Key Takeaways
- The Python package num2words version 0.5.15 was published to PyPI without a corresponding tag in the official GitHub repository
- Security researcher @johnk3r identified potential links to the "Scavenger" threat actor, known for previous supply chain attacks
- PyPI has removed the compromised package, preventing further installations
- This incident highlights the ongoing risks in the Python ecosystem's supply chain security
The Incident
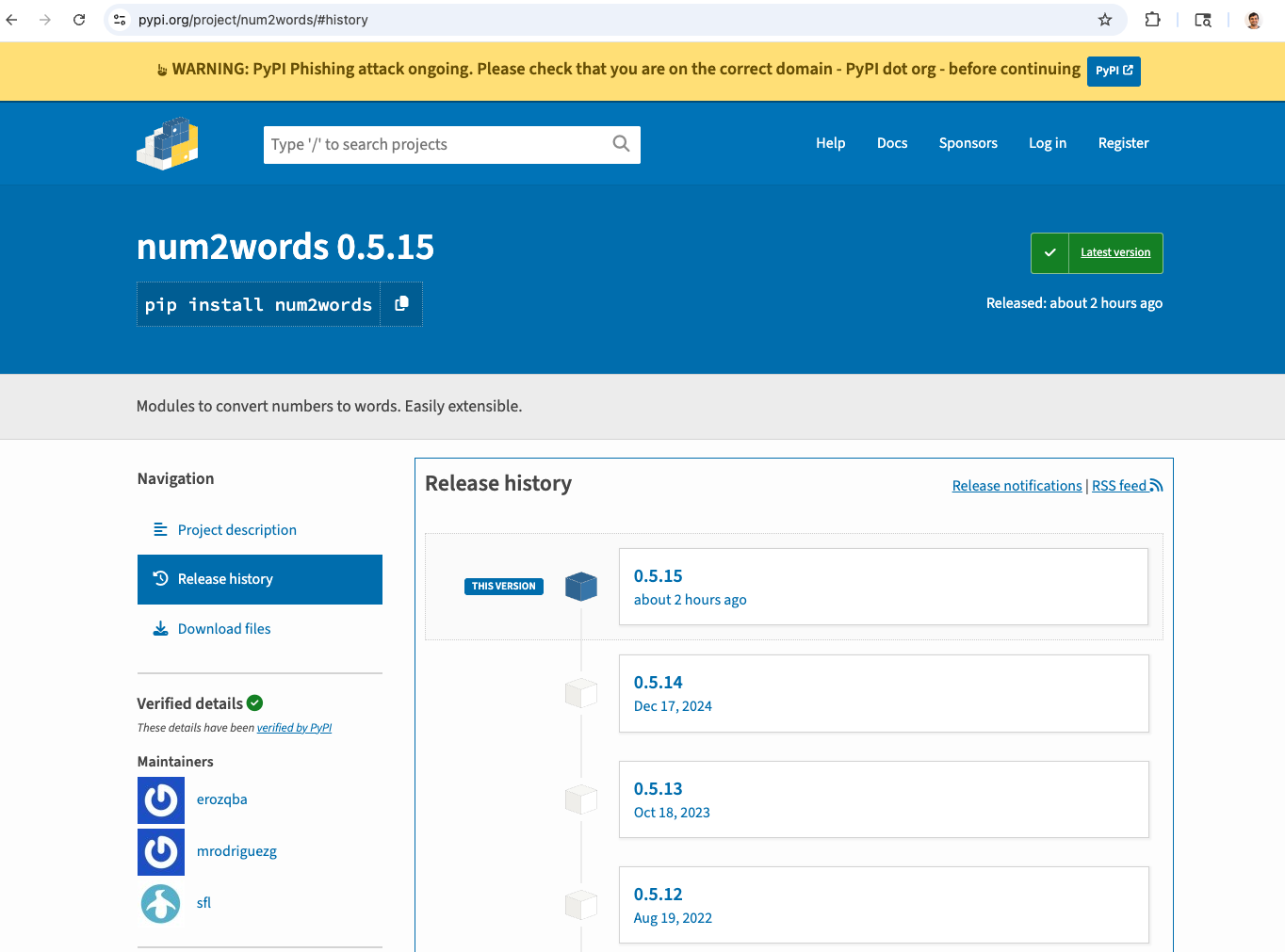
On July 28, 2025, the Python community was alerted to a potential supply chain attack involving the popular num2words package. Version 0.5.15 of this widely-used library for converting numbers to words was published to PyPI approximately 2 hours before being flagged as potentially compromised.
Red Flags and Initial Detection
The compromise was first identified through several concerning indicators:
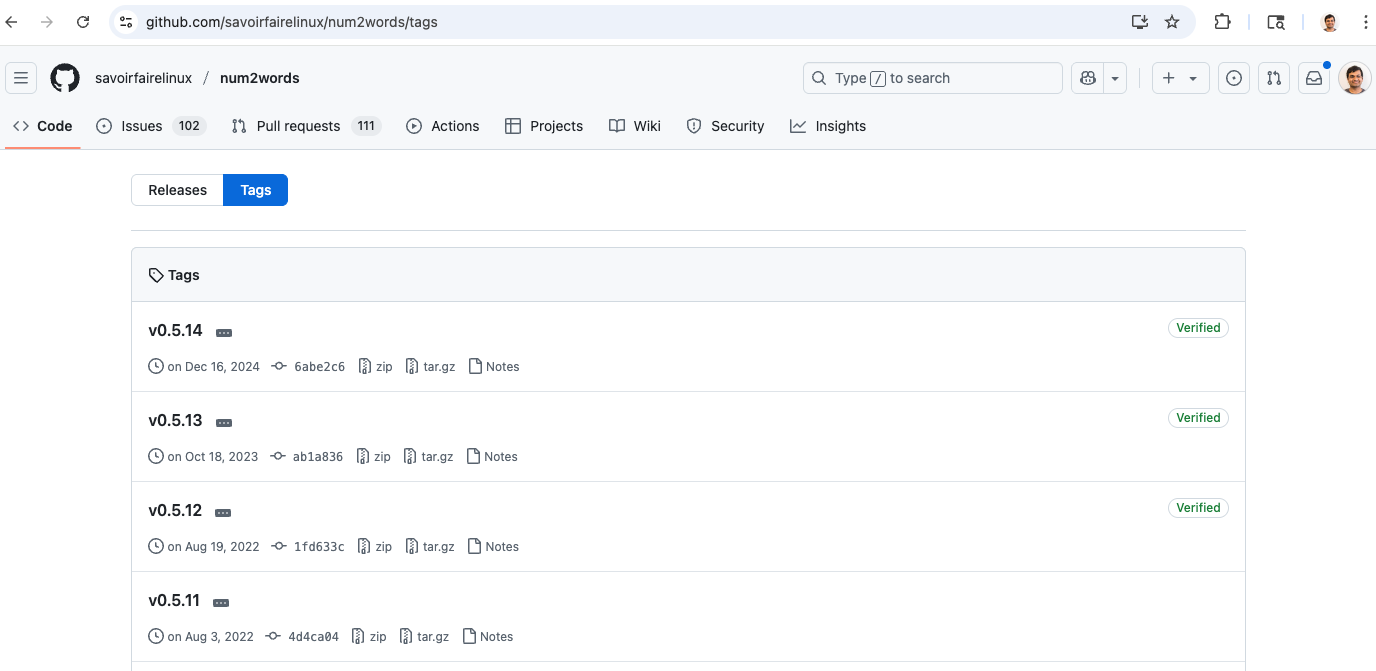
- Missing Repository Tag: Unlike previous releases, version 0.5.15 was published to PyPI without a corresponding tag in the official GitHub repository at https://github.com/savoirfairelinux/num2words/tags
- Timing Discrepancy: The package appeared on PyPI without any associated commits or release activities in the source repository
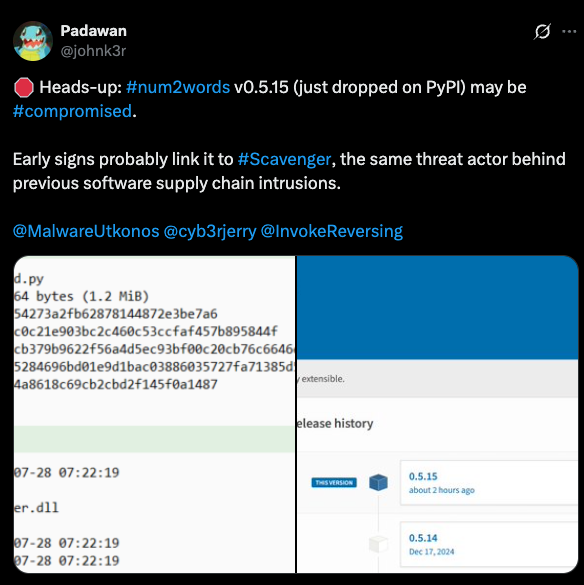
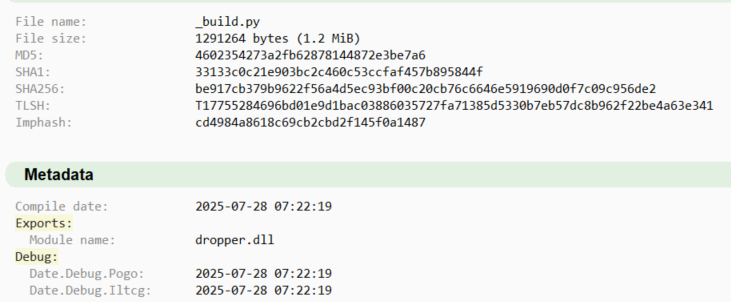
- Community Alert: Security researcher @johnk3r quickly raised the alarm on social media, warning the community about potential compromise
The Scavenger Connection
According to @johnk3r's analysis, early indicators suggest this incident may be linked to "Scavenger," a threat actor previously associated with software supply chain intrusions. While full attribution requires deeper investigation, the modus operandi matches previous attacks:
- Publishing malicious versions of legitimate packages
- Exploiting the trust users place in established package names
- Targeting popular packages to maximize potential impact
Automated Tools Already Upgrading to Malicious Version
Despite the quick response, automated dependency management tools had already begun creating pull requests to upgrade projects to the compromised version. A GitHub search reveals numerous automated PRs attempting to update num2words to version 0.5.15, demonstrating how quickly malicious packages can propagate through the ecosystem. Here is a sample pull request:
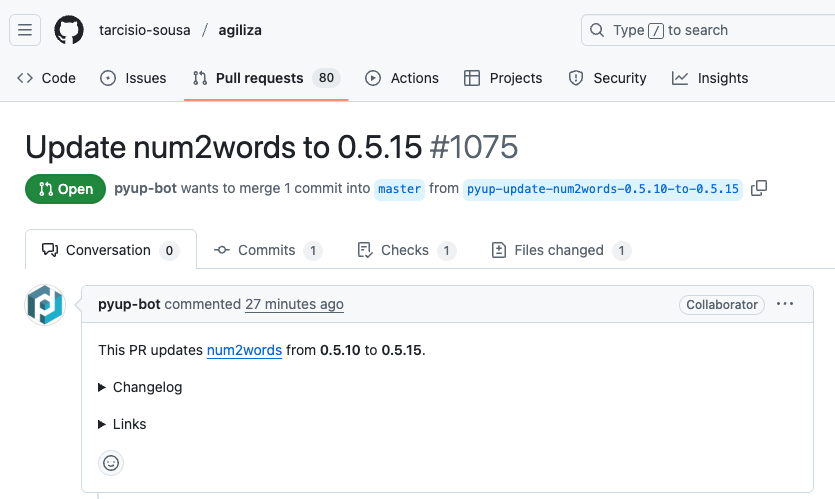
Impact and Response
The num2words package is a widely-used Python library that provides functionality to convert numbers into their word representations across multiple languages. With thousands of downloads daily, any compromise could have had significant reach across the Python ecosystem.
Fortunately, the rapid response from the community and PyPI administrators helped contain the potential damage:
- Quick Detection: The suspicious release was identified within hours of publication
- Swift Action: PyPI removed the compromised package, preventing new installations
- Community Warning: Security alerts spread quickly through social media and developer channels
What You Should Do
If you use num2words in your projects:
Check Your Environment
Run pip list | grep num2words to verify which version you have installed
Downgrade if Necessary
f you have v0.5.15 installed, immediately downgrade to v0.5.14 using pip install num2words==0.5.14
Audit Your Systems
Review logs and systems that may have installed the compromised version
Update Security Practices
Consider implementing additional supply chain security measures
For StepSecurity Enterprise Customers
The following steps are applicable only for StepSecurity enterprise customers. If you are not an existing enterprise customer, you can start our 14 day free trial by installing the StepSecurity GitHub App to complete the following recovery step.
Use StepSecurity Harden-Runner to detect compromised dependencies in CI/CD
StepSecurity Harden-Runner adds runtime security monitoring to your GitHub Actions workflows, providing visibility into network calls, file system changes, and process executions during CI/CD runs. In cases like the eslint-config-prettier compromise, Harden-Runner would detect and alert on suspicious behavior such as unexpected network connections to malicious domains or unauthorized file modifications during the build process. The tool creates an audit trail of all activities within your workflows, enabling rapid forensic analysis when investigating potential security incidents. By hardening your CI/CD pipelines with runtime monitoring, you can prevent compromised dependencies from executing malicious code in your build environment. The following screenshot shows how Harden-Runner detected the tj-actions supply chain incident.

Implement Harden-Runner in your workflows by following the guide at https://docs.stepsecurity.io/harden-runner.
The Broader Picture
This incident is part of a concerning trend of supply chain attacks targeting package repositories. Similar to the recent npm ecosystem attacks on packages like is and eslint-config-prettier, threat actors continue to exploit the trust-based nature of open source package distribution.
The Python community, like its JavaScript counterpart, must remain vigilant and continue strengthening security practices around package publication and consumption.
Moving Forward
While PyPI's quick response prevented widespread damage, this incident serves as another reminder that supply chain security requires constant vigilance. Package maintainers should:
- Implement strong authentication and authorization for package publishing
- Use signing mechanisms where available
- Establish clear release processes that include repository tagging
- Consider adopting tools and practices that verify package integrity
For package consumers, the message is clear: trust but verify. The convenience of package managers should not override security considerations.
Acknowledgments
Thanks to Cedric Brisson for alerting us to this incident and to @johnk3r for the rapid identification and public alert on X. Their quick action in raising awareness helped the community respond swiftly. We also thank the PyPI administrators for their swift response in removing the compromised package.
Stay informed about supply chain security threats by following security researchers and subscribing to relevant security advisories. If you identify suspicious package behavior, report it immediately to the appropriate package repository administrators.


.png)
.png)
