Introduction
This is the story of how StepSecurity Harden Runner's runtime security monitoring uncovered an unexpected and widespread infrastructure change that affected a large number of GitHub Actions workflows worldwide. When Microsoft Defender was unintentionally deployed to some Ubuntu runners on GitHub's infrastructure, it was our automated anomaly detection that raised the alarm, demonstrating the critical importance of runtime visibility in modern CI/CD pipelines.
While this was not a security incident, such anomalous calls have in the past been associated with supply chain attacks. For example, in March 2025 an anomalous outbound call led to the discovery that the tj-actions/changed-files action had been compromised.
What makes this discovery particularly significant is that without runtime monitoring, this change would have remained invisible to most organizations – silently consuming resources, generating unexpected network traffic, and potentially interfering with builds.
Here's how we detected it, what it means for CI/CD security, and why every organization needs runtime monitoring for their pipelines.
The Discovery: Anomalous Network Calls Raise Red Flags
Starting July 15th 2025, StepSecurity Harden Runner began detecting unusual network activity across multiple GitHub Actions workflows running on GitHub-hosted Ubuntu runners.
What Happened: Unintended Defender Deployment
Through Harden Runner's network monitoring capabilities, we identified that the wdavdaemon process (Microsoft Defender's daemon) was making calls to various Microsoft endpoints including:
- x.cp.wd.microsoft.com
- global.endpoint.security.microsoft.com
- wdcp.microsoft.com
These calls were observed across both our enterprise and community tier customers, affecting Ubuntu runners on both standard and larger GitHub-hosted runners.
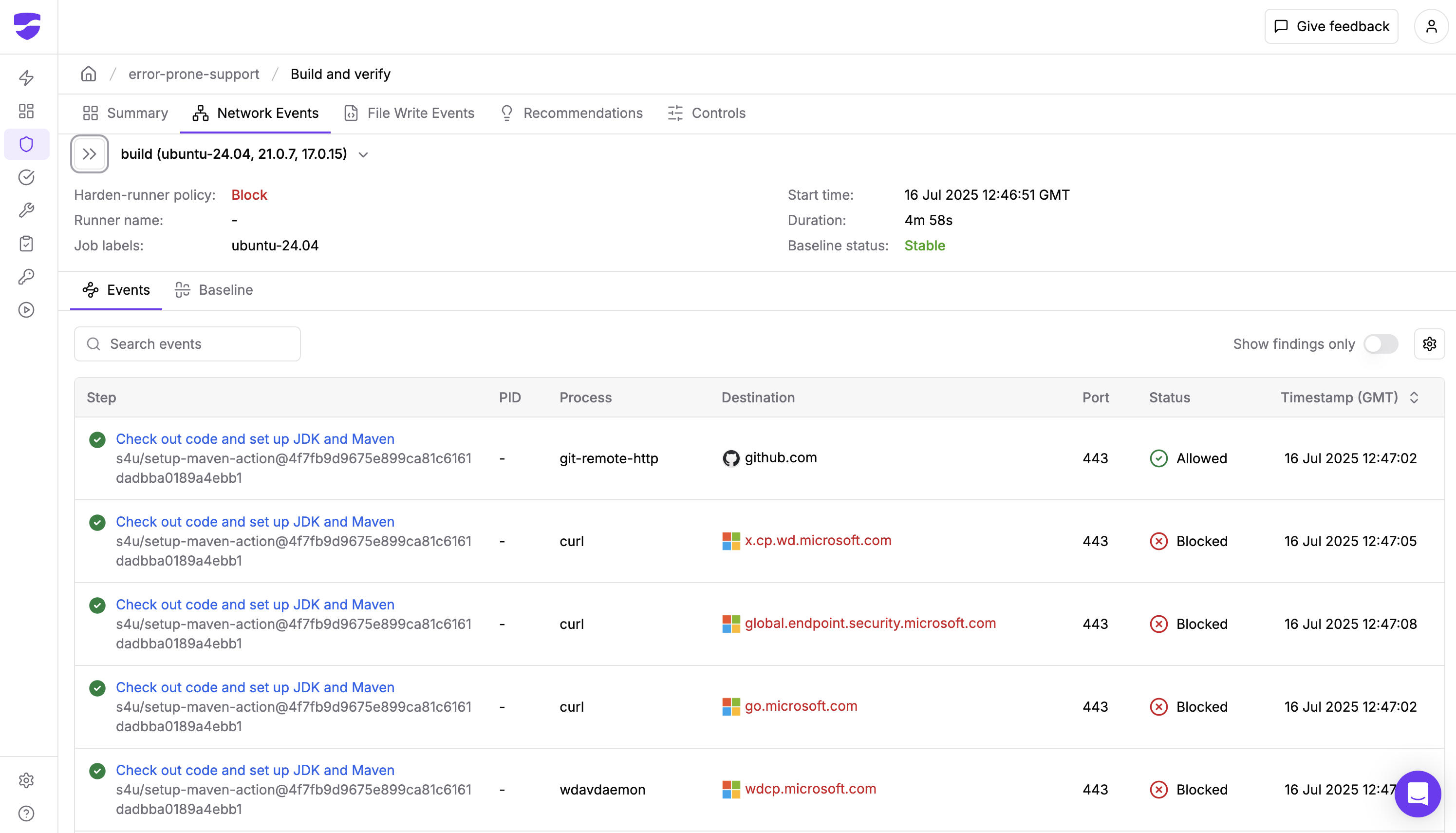
One concrete example was captured through our community tier's public insights in the PicnicSupermarket/error-prone-support repository (Run #16319862376), where Harden Runner clearly showed the unexpected network activity.
GitHub's Response: Confirming the Unintentional Installation
After reporting our findings to GitHub Support and creating an issue in the actions/runner-images repository (#12656), GitHub's engineering team investigated and confirmed our observations.
Their response on our enterprise support ticket validated what Harden Runner had detected:
"Our engineers identified cases where Virtual Machine resources erroneously had Microsoft Defender Endpoint applied, resulting in the behavior that you saw. This was unintentional, and we believe that we've now corrected this."

GitHub acknowledged that this was an unintended configuration error and has since corrected the issue while implementing measures to prevent similar incidents in the future.
How Harden Runner Detected the Anomaly
Intelligent Baseline and Anomaly Detection
Harden Runner's detection capabilities go beyond simple monitoring. The system automatically creates an intelligent baseline for each job, learning the normal network behavior patterns of your workflows. When new outbound calls occur that aren't part of this established baseline, Harden Runner immediately triggers detections and alerts.
In this case, calls to Microsoft Defender endpoints were immediately flagged as anomalous because they had never been part of the baseline behavior for any of the jobs. This automatic anomaly detection meant that the issue was caught within hours of its introduction, rather than potentially going unnoticed for weeks or months.
Active Blocking and Detection Triggers
Many of our users have configured Harden Runner in block mode based on their established baselines. When the Defender endpoints weren't in their allowed lists, these unexpected calls were automatically blocked, which:
- Prevented unwanted network traffic from leaving the CI/CD environment
- Triggered immediate detection notifications alerting teams to the anomaly
This proactive blocking meant that many teams were protected from the issue even before understanding what was happening, demonstrating the value of runtime security policies in CI/CD.
Community Tier: Network Visibility
With our community tier which is free for open-source projects using GitHub-hosted runners, Harden Runner provides valuable network monitoring that made this discovery possible. Users could see:
- Unexpected domains: Calls to *.microsoft.com endpoints that shouldn't exist on Ubuntu runners
- Blocked calls: Blocked calls to Microsoft Defender endpoints
- Public transparency: All network insights are publicly available for open-source projects
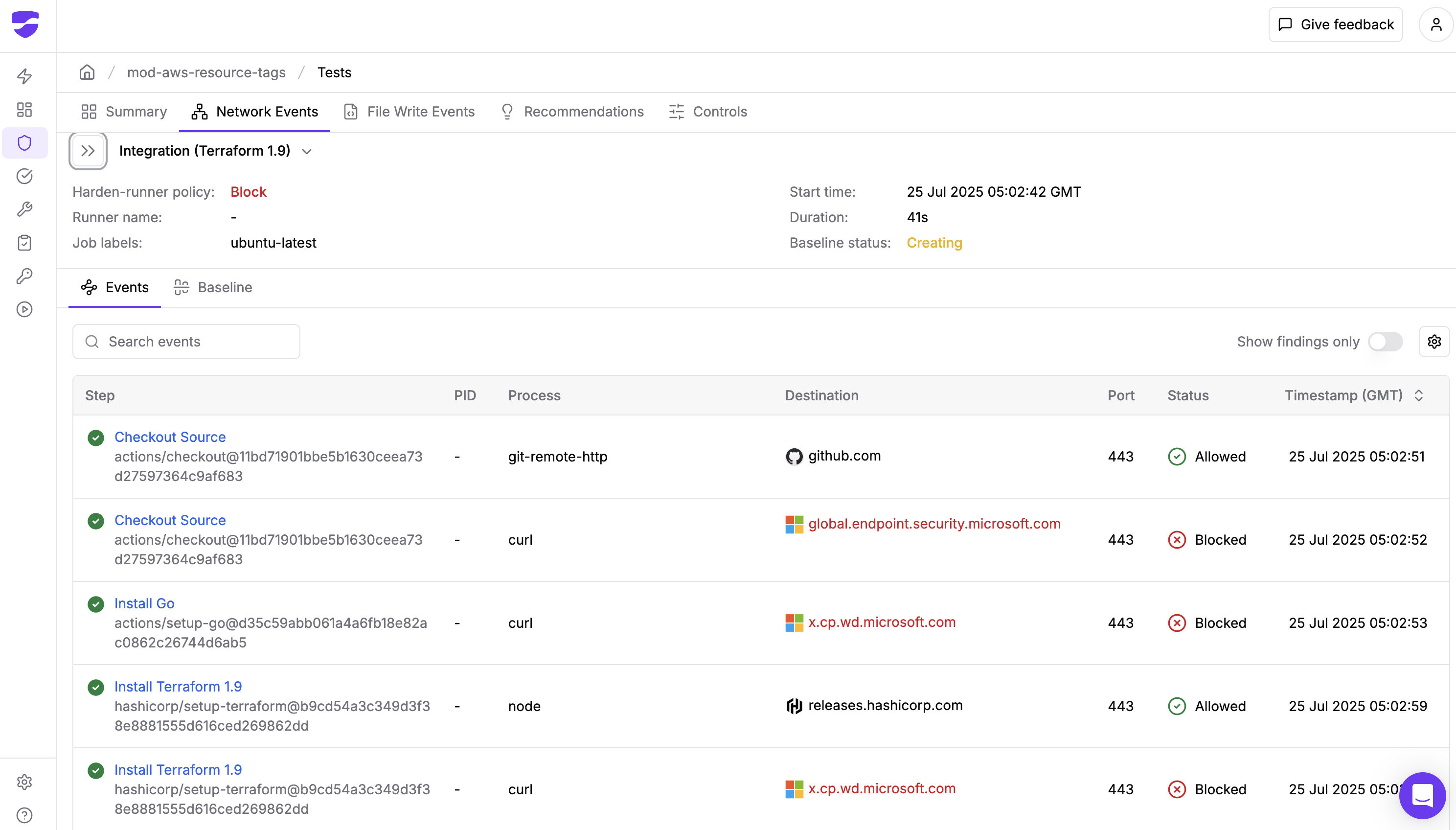
Enterprise Tier: Deep Process Intelligence
For our enterprise customers, Harden Runner provided even deeper visibility into the issue:
- Command arguments: Full command-line arguments showing how the Defender daemon was launched
- Process lineage: Understanding which processes spawned the Defender components
- Real-time notifications: Alerts via Slack/email when anomalies are detected
- SIEM integration: Integration with SIEM solutions for centralized security monitoring
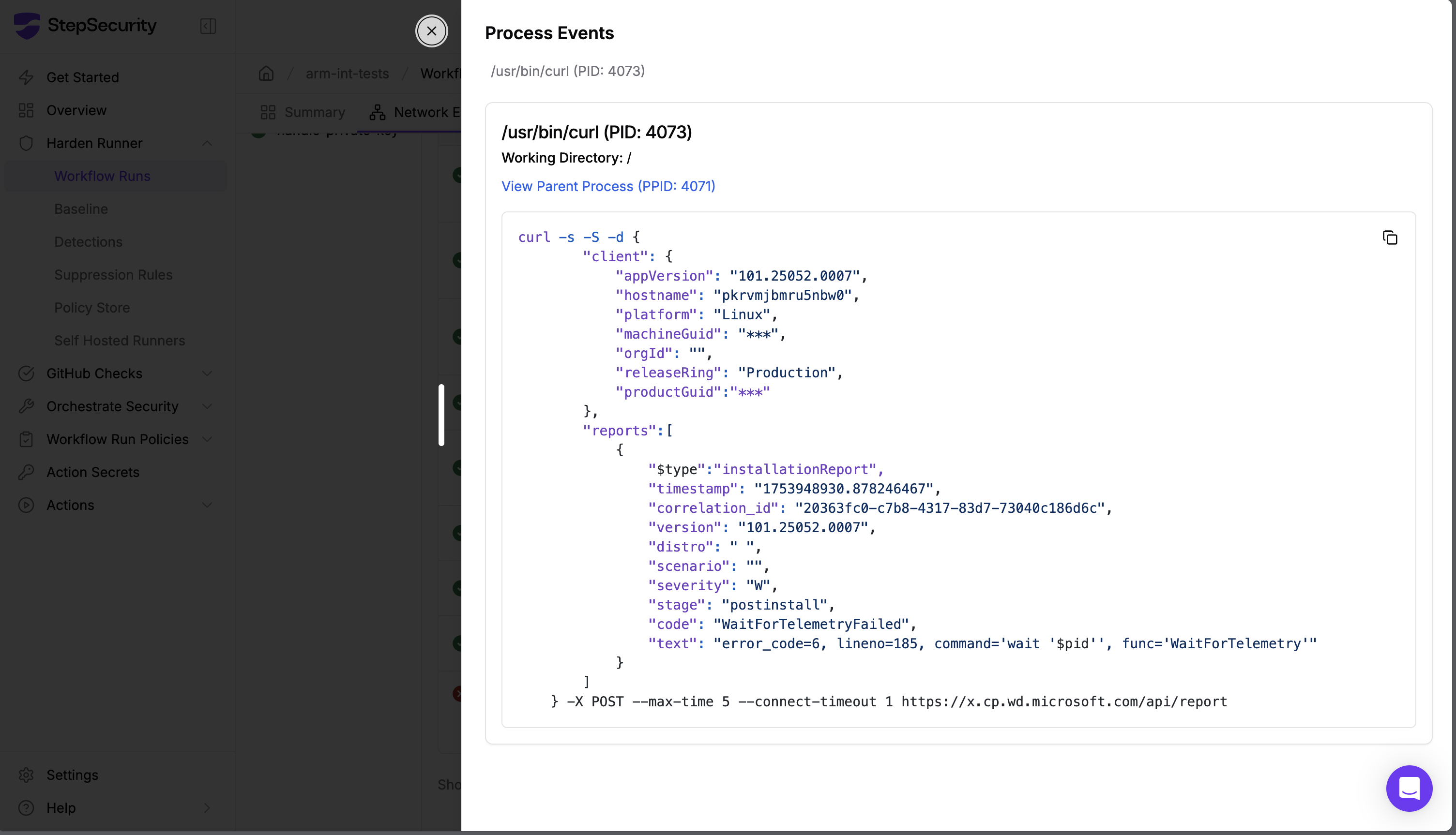
This granular visibility allowed enterprise users to immediately understand not just that something unusual was happening, but exactly what was running and how it was configured.
The Importance of Runtime Security in CI/CD
This incident underscores several critical points about CI/CD security:
1. Infrastructure Changes Can Happen Without Notice
Even unintentional changes to GitHub-hosted runners can impact your workflows. Without monitoring, these changes remain invisible until they cause problems.
2. Network Monitoring Reveals Hidden Behavior
Unexpected network calls are often the first indicator of unwanted software or security issues. Harden Runner's network monitoring caught behavior that would otherwise go unnoticed.
3. Process-Level Visibility is Critical
Understanding not just what network calls are being made, but which processes are making them, is essential for rapid diagnosis and response.
4. Community Benefits from Transparency
Our community tier's public insights meant that this issue could be identified and verified across multiple organizations, leading to faster resolution.
Protecting Your Pipelines with Harden Runner

This Microsoft Defender incident is just one example of how runtime security monitoring can protect your CI/CD pipelines from unexpected changes and potential security risks.
In fact, Harden Runner's anomaly detection has proven its value in catching actual security incidents as well. In March 2025, Harden Runner detected the tj-actions/changed-files compromise by identifying an anomalous call to gist.githubusercontent.com – a domain that wasn't part of the action's normal behavior baseline. This early detection helped prevent potential supply chain attacks before they could spread.
Harden Runner provides:
- Real-time network monitoring to detect anomalous connections
- Intelligent baseline creation that learns your workflows' normal behavior
- Automated blocking of unexpected network calls to prevent data exfiltration
- Process monitoring (Enterprise) to understand exactly what's running in your workflows
Whether you're using our free community tier or our enterprise solution, Harden Runner acts as your early warning system for CI/CD anomalies.
Start Monitoring in 60 Seconds
Protect your GitHub Actions workflows running on GitHub-hosted runners today by adding Harden Runner to your pipelines:
- uses: step-security/harden-runner@v2
with:
egress-policy: audit For enterprise features including detailed process monitoring and private insights, start a 14 day free trial.
Conclusion
The unexpected installation of Microsoft Defender on GitHub-hosted Ubuntu runners demonstrates that even well-managed cloud infrastructure can experience configuration drift. Without StepSecurity Harden Runner's runtime monitoring, this issue might have gone undetected for much longer, potentially impacting build times, creating unexpected network traffic, and raising security concerns.
This incident reinforces our belief that runtime security monitoring is not optional for modern CI/CD pipelines – it's essential. As organizations increasingly rely on GitHub Actions and other CI/CD platforms, having visibility into what's actually happening during workflow execution becomes critical for both security and operational excellence.
Stay secure, stay informed, and keep your pipelines protected with StepSecurity Harden Runner.
.png)