Developer machines hold your most sensitive credentials such as GitHub credentials with permissions, npm publishing tokens, and other secrets with access to production infrastructure. And now, AI coding agents are autonomously installing dependencies and executing tools with those same privileges. Campaigns like Shai Hulud and the Nx s1ngularity incident harvested developer tokens and keys, then used them to spread further and publish malicious updates. There's finally a purpose-built solution to protect both Developer Machines and AI Coding Agents against software supply chain attacks.
The New Attack Surface: Developer Machines and AI Coding Agents
Over the past year, we have witnessed a fundamental shift in how attackers target software supply chains. While CI/CD pipelines and source code repositories remain a critical attack vector, we have seen sophisticated threat actors increasingly pivot further left to an even more vulnerable target: developer machines.
The logic is simple. Developer machines are treasure troves of sensitive credentials: elevated GitHub permissions, publishing credentials to package registries like npm and PyPI, SSH keys, and access to both development and production infrastructure.
Compounding this challenge is the explosive adoption of AI coding agents. Tools like Claude Code, GitHub Copilot, Cursor, and Gemini are transforming how software is written. But they're also introducing entirely new blind spots for supply chain security. These AI agents autonomously install dependencies, execute tools, and interact with external services, often with the same elevated privileges as the human developers they assist.
This gap hasn't gone unnoticed by attackers.
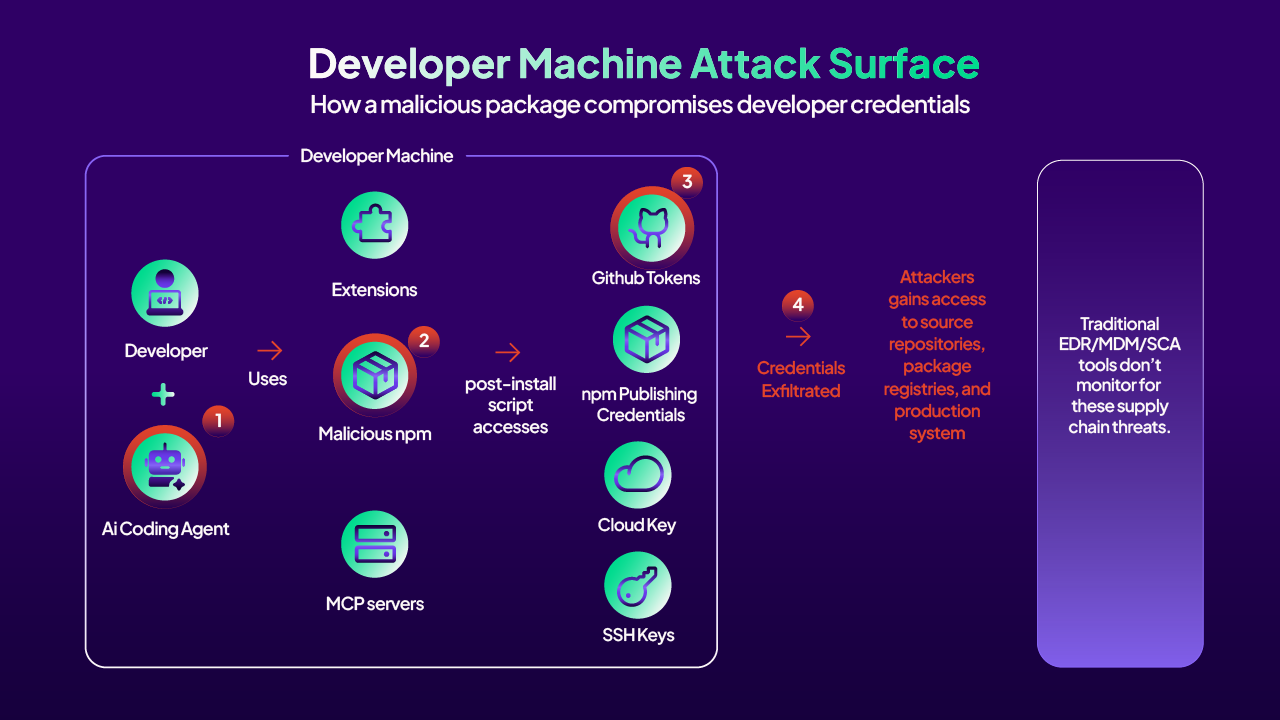
How the attack unfolds:
- An AI coding agent starts using a compromised npm package to complete a development task.
- When the application code is built or executed, the malicious package is installed.
- The post-install script in the package accesses secrets stored on the developer machine - GitHub tokens, npm publishing credentials, cloud keys, and SSH keys.
- These credentials are then exfiltrated to attacker-controlled infrastructure, enabling lateral movement into source repositories, package registries, and production systems.
Why AI agents change the game
AI coding agents are moving from autocomplete to autonomous behavior: writing code, debugging, installing dependencies, running tools, and calling external services, often with minimal human oversight. That introduces blind spots attackers love:
1. Autonomous dependency installation: Humans may pause before installing an unfamiliar package. Agents typically optimize for task completion and may install what is needed without review.
2. Tool and MCP server integration: Agents extend their capabilities through external tools and Model Context Protocol (MCP) servers. Each integration point can become a supply chain entry path.
3. Elevated privileges without visibility: Agents commonly inherit the same credentials and access a developer has. Many organizations have limited visibility into what those agents do with that access.
Why this isn’t just EDR, SCA, or MDM
If you are an enterprise buyer, the first question is fair: “Don’t we already have tools for endpoints and dependencies?”
Here’s the gap:
Endpoint Detection and Response (EDR) excels at detecting malware and suspicious behavior, but it often lacks developer ecosystem context, such as extension provenance, package lifecycle risk, and guardrails tailored to supply chain threats.
Software Composition Analysis (SCA) finds issues in what you build and commit. It often cannot see what’s installed and executed locally, especially by agents, before anything reaches a PR.
Mobile Device Management (MDM) is great for device posture and configuration (OS versions, disk encryption, baseline settings). It does not understand software supply chain risk inside developer workflows.
Developer MDM fills the missing layer: supply chain visibility and guardrails directly on developer machines, where many modern compromises begin.
Real-World Impact: Trust Wallet shows how a developer machine compromise becomes a release compromise
A recent incident involving the Trust Wallet browser extension illustrates the new “endpoint to release” attack path.
Trust Wallet reported that an unauthorized, malicious version of its browser extension (v2.68) was published to the Chrome Web Store, impacting users who logged in during December 24 to 26, 2025. Trust Wallet reported 2,520 affected wallet addresses and estimated about $8.5M in assets impacted. Trust Wallet+1
Trust Wallet also stated they had high confidence the incident was linked to the industry wide Shai Hulud supply chain attack in November 2025. In their update, they described how exposed developer GitHub secrets enabled attacker access to the browser extension source and publishing credentials (including a Chrome Web Store API key). The attacker used those credentials to publish a malicious release outside Trust Wallet’s internal approval process. Trust Wallet+1
This is the pattern we see more often now:
- Malicious code reaches a developer machine via a dependency, extension, or tool
- Developer secrets are harvested (GitHub tokens, registry tokens, SSH keys, cloud credentials)
- Attackers pivot into source control and publishing systems
- Malicious releases reach end users by abusing stolen credentials
If you want to stop modern supply chain attacks earlier, you need defenses where these pivots begin, on developer machines.
.png)
Recent incidents show how exposed the developer ecosystem is
The Trust Wallet breach isn't an isolated incident. Over the past several months, we've tracked an alarming acceleration in attacks targeting developer workstations, attacks that would be equally effective against human developers and AI coding agents:
Over 100 VSCode Extensions Exposed 150,000+ Developers
In October 2025, security researchers discovered that publishers of over 100 VSCode extensions had leaked access tokens, enabling attackers to push malicious updates to more than 150,000 developers automatically. The leaked tokens could allow complete takeover of extensions with automatic distribution of malware through VSCode's auto-update feature.
s1ngularity Nx Compromise: 4 Million Weekly Downloads Affected
In August 2025, the popular Nx build system package was compromised in what became known as the s1ngularity attack. Developers were compromised simply by opening VSCode, which auto-downloaded the infected version. The malicious scripts stole GitHub and npm tokens, SSH keys, and weaponized AI CLI tools installed on developer machines.
Sha1-Hulud: The Second Coming
The November 2025 Sha1-Hulud campaign that ultimately led to the Trust Wallet breach compromised over 70 npm packages with malicious code that harvested developer credentials. Within just 5 hours of initial detection, over 21,000 public GitHub repositories had been created containing stolen credentials.
Introducing StepSecurity Developer MDM
StepSecurity Developer MDM is built to secure the development environment, the place where credentials live and untrusted code executes, across both interactive developer workflows and agentic development.
Developer MDM extends the StepSecurity supply chain platform beyond repositories and CI/CD into the workstation. It provides:
- Visibility into installed npm packages and other local dependency ecosystems
- Visibility into IDE extensions
- Risk assessment with supply chain context
- Policy enforcement to reduce exposure to malicious update windows
- Monitoring and controls for AI coding agents and the tools they use
Beta note: Developer MDM is currently in beta. This post covers capabilities available today plus near-term roadmap items in active development.
StepSecurity Developer MDM Key Capabilities
IDE extension security (VSCode and Cursor)
- Inventory IDE extensions across your org, including AI-assisted IDE workflows
- Identify risky extensions and publishers
- Enforce allowlists and blocklists without disrupting developer productivity
Open-source dependency monitoring (local installs, not just commits)
- Monitor npm and Python dependencies installed on developer machines, whether installed by a person or an agent
- Flag risky versions and suspicious install behaviors
- Apply cooldown periods for newly published package versions to reduce exposure during the critical early window when malicious updates often spread
Policy enforcement (guardrails that match real dev workflows)
- Allowlists for approved extensions
- Cooldown policies for new releases
- Alerts and automated blocking for known malicious components
- Policies that apply consistently across human and agent-driven actions
AI coding agent security (visibility into the agent ecosystem)
Agentic development adds new surfaces: tool execution, context loading behavior, external integrations, and MCP servers.
Developer MDM helps you make AI-assisted development safe and answer questions like:
- Which AI-assisted IDEs and agent workflows are being used across the org?
- Which MCP servers or external tools are being invoked from developer machines?
- Where are high-risk integrations appearing, and how do we set sensible guardrails?
How StepSecurity Developer MDM Works
StepSecurity Developer MDM integrates seamlessly with your existing infrastructure, we don't require you to adopt new MDM or EDR tooling.
Step 1: Deploy Through Your Existing MDM/EDR
Review and deploy our lightweight monitoring script via your current MDM or EDR tooling. StepSecurity does not require access to your MDM/EDR solution. Instead, we provide a lightweight script that integrates with your existing infrastructure.
Step 2: Gain Visibility
The script runs periodically or on-demand on developer machines collecting various telemetry. This provides visibility into both human developer activity and AI coding agent actions.
Step 3: Enforce Controls
Configure and enforce security policies including extension allowlists, package cooldown periods, security risk alerts, and automated blocking of known-malicious components. Policies apply consistently whether actions are taken by human developers or AI agents.
.png)
Complete Coverage Across the Software Development Lifecycle
Modern supply chain attacks don't respect boundaries. The Sha1-Hulud campaign perfectly illustrates this reality. It compromised npm packages that executed on developer machines, stole credentials that provided access to source repositories, and ultimately enabled attackers to bypass release controls entirely.
With Developer MDM, the StepSecurity platform now covers all stages:
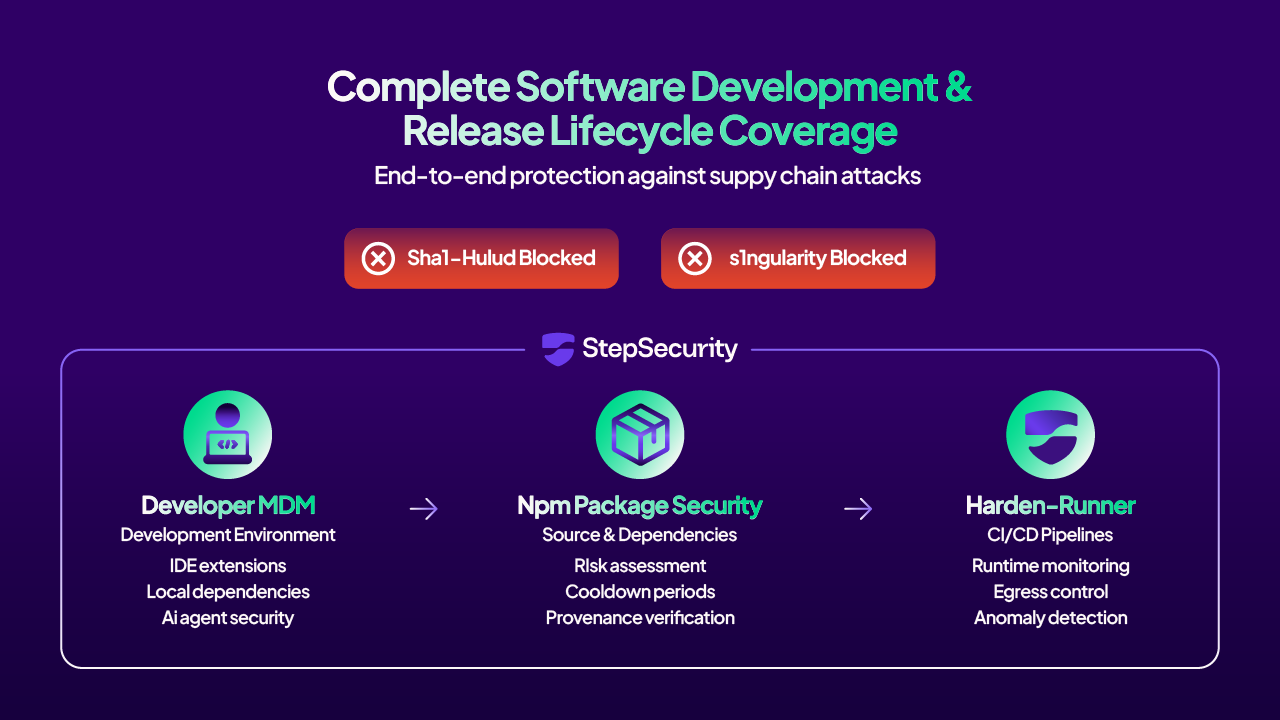
This unified approach means that even if an attack like Sha1-Hulud attempts to compromise your development pipeline, StepSecurity provides defense in depth:
- Developer MDM would detect the malicious npm package attempting to execute on developer machines, whether installed by a human developer or an AI coding agent
- npm Package Security would flag newly published malicious package versions via cooldown periods, preventing their adoption during the critical attack window
- Harden-Runner would detect anomalous network calls and process execution in CI/CD if the malicious package reached your build pipeline
No single point of protection is sufficient against modern supply chain attacks. With StepSecurity, you get comprehensive coverage across the entire software development and delivery lifecycle.
Get Early Access
StepSecurity Developer MDM is currently in beta, and the response from our design partners has been overwhelmingly positive.
"The threat landscape continues to evolve, with malicious and compromised VSCode extensions and npm packages posing a growing risk to developer environments. StepSecurity has built a strong reputation for securing CI/CD pipelines, and their new Developer MDM capability extends that same security rigour to developer endpoints. We've been impressed by the StepSecurity team's responsiveness and agility - they iterate quickly and consistently deliver value based on our feedback."
— Colin Barr, Head of InfoSec and IT at Paddle
We're working closely with several enterprise customers like Paddle to refine the product based on real-world requirements.
If you're concerned about developer machine security, we'd love to hear from you.
Interested in early access? Request a Demo
For existing StepSecurity customers, please contact your account team to discuss adding Developer MDM to your deployment.
Conclusion
Developer machines have become a critical link in the software supply chain—and AI coding agents are expanding that attack surface daily. StepSecurity Developer MDM gives you the visibility and controls to secure both, before attackers reach your CI/CD pipelines and release infrastructure.
.png)

.png)
