When implementing anthropics/claude-code-action in GitHub Actions, understanding its security implications is crucial for enterprise deployments. In our first article, we explored the unique security considerations when running AI coding agents in CI/CD environments. The second article demonstrated how runtime monitoring enhances GitHub Copilot's built-in security features. Now, let's examine Claude Code - an agent that prioritizes flexibility and power over built-in restrictions - and show how Harden-Runner provides the essential security layer for production deployments.
Claude Code: Power Without Built-in Network Restrictions
Claude Code in GitHub Actions takes a fundamentally different approach to security compared to GitHub Copilot. While Copilot includes a network firewall by default, Claude Code operates without network restrictions, giving it unrestricted access to external resources. This design philosophy prioritizes developer flexibility and agent capability, but it also means that security becomes entirely the responsibility of the implementation team.
This lack of built-in network controls isn't a weakness - it's a design choice that enables Claude Code to:
- Install any necessary dependencies without pre-approval
- Access APIs and services dynamically based on task requirements
- Adapt to diverse development environments without configuration overhead
- Execute complex multi-step workflows that may require various external resources
However, this flexibility makes runtime security monitoring not just important, but essential. Without visibility into Claude's network activities, organizations operate blind to potential security risks.
Configuration Controls: Necessary but Not Sufficient
Claude Code does provide configuration options through allowed_tools and disallowed_tools that help shape the agent's behavior:
allowed_tools: |
Bash(npm install)
Bash(npm test)These controls are valuable for defining what actions Claude can take, but they don't address the core security challenge: visibility into runtime behavior. You can restrict Claude to only use specific bash commands, but you still can't see:
- What those commands actually do when executed
- Which network endpoints are contacted
- What files are created or modified
- How the generated code behaves at runtime
.png)
Implementing Harden-Runner: Your Security Foundation
Given Claude Code's unrestricted network access, implementing Harden-Runner becomes your primary security control. Here's how to secure anthropics/claude-code-action in your GitHub workflows::
name: Claude Code
on:
issue_comment:
types: [created]
pull_request_review_comment:
types: [created]
issues:
types: [opened, assigned]
pull_request_review:
types: [submitted]
jobs:
claude:
if: |
(github.event_name == 'issue_comment' && contains(github.event.comment.body, '@claude')) ||
(github.event_name == 'pull_request_review_comment' && contains(github.event.comment.body, '@claude')) ||
(github.event_name == 'pull_request_review' && contains(github.event.review.body, '@claude')) ||
(github.event_name == 'issues' && (contains(github.event.issue.body, '@claude') || contains(github.event.issue.title, '@claude')))
runs-on: ubuntu-latest
permissions:
contents: read
pull-requests: read
issues: read
id-token: write
steps:
- name: Harden the runner (Audit all outbound calls)
uses: step-security/harden-runner@v2
with:
egress-policy: audit
- name: Checkout repository
uses: actions/checkout@v4
with:
fetch-depth: 1
- name: Run Claude Code
id: claude
uses: anthropics/claude-code-action@beta
with:
anthropic_api_key: ${{ secrets.ANTHROPIC_API_KEY }}
allowed_tools: "Bash"Real-World Example: Monitoring Claude Code's Network Activity
Let's examine a real example where anthropics/claude-code-action was deployed in a production workflow. The Claude Code agent was tasked with creating a Python program for image generation and OCR capabilities. You can see this GitHub issue here.
When a user asked Claude Code to implement the issue, it triggered the GitHub Actions workflow run Claude Code #2. This workflow run was monitored by Harden-Runner due to the copilot-setup-steps.yml workflow file created previously. As this is a public repository, you can explore the Harden-Runner insights for this run here.
On this insights page, you can find detailed information about:
Detailed Network Activity Analysis
The network events tab reveals fascinating insights into Claude Code's execution pattern.
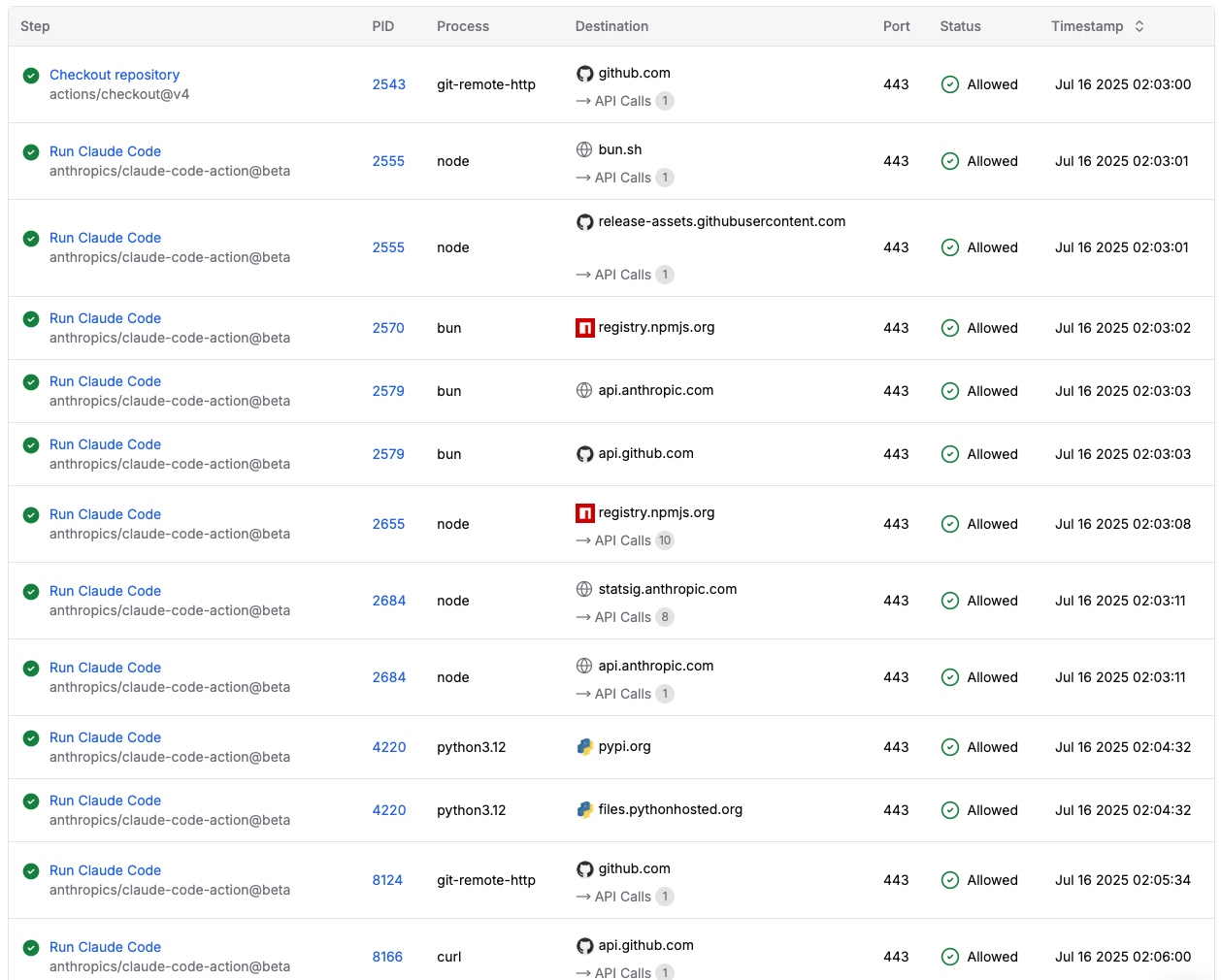
Here's what happened during the workflow run:
1. Initial Setup and Repository Operations
- The workflow began with git-remote-http (PID 2543) accessing github.com to clone the repository
- This process made a GET API call to "/step-security/coding-agent-security/info/refs?service=git-upload-pack" for git operations
2. Claude Code Runtime Initialization
- Multiple Node.js processes (PIDs 2555, 2684) established connections to various endpoints
- The main Claude Code process made POST API calls to api.anthropic.com at "/v1/messages?beta=true" for authentication and communication
- Node.js processes connected to registry.npmjs.org with GET requests for packages like:
- "/@anthropic-ai%2fclaude-code"
- "/@img%2fsharp-linux-arm"
- "/@img%2fsharp-linux-x64"
- "/@img%2fsharp-win32-x64"
- "/@img%2fsharp-darwin-x64"
- "/@img%2fsharp-linux-arm64"
- "/@img%2fsharp-darwin-arm64"
- Additional GET connections to release-assets.githubusercontent.com for downloading runtime components and binaries
- “/github-production-release-asset/357728969/56a3cc74-8a0b-48f7-9f05-3c8aa54d971a?sp=r&sv=2018-11-09&sr=...”
3. Core Claude Code Operations
- The main Claude Code processes made extensive API calls to github.com
- Multiple curl processes (PIDs 8166, 8124) connected to api.github.com for GitHub API interactions. These API calls included operations like:
- DELETE request to "/installation/token" (PID 8166) for managing GitHub App installations
- GET request to "/step-security/coding-agent-security.git/info/refs?service=git-receive-pack" (PID 8124) for repository operations
- Managing GitHub integration states and authentication tokens
4. Package Management and Dependencies
- Node.js processes accessed multiple package registries:
- registry.npmjs.org for Node.js packages with specific GET requests:
- "/sharp-libvips-linux-x64/-/sharp-libvips-linux-x64-1.0.4.tgz"
- "/sharp-linux-x64/-/sharp-linux-x64-0.33.5.tgz"
- bun.sh (PID 2555) with GET request to "/download/1.2.11/linux/x64?avx2=true&profile=false" for the Bun runtime environment
- Multiple connections showed downloading of platform-specific binaries (linux-x64, darwin-x64, win32-x64, linux-arm, darwin-arm64)
5. Python Environment Setup
- Python-related processes (PIDs 4220) were spawned for the OCR task
- Connections to pypi.org indicated Python package installations
6. Runtime Monitoring and Telemetry
- Connections to statsig.anthropic.com indicated telemetry and monitoring data collection. Several POST calls were made to “/v1/initialize” and “/v1/rgstr” API endpoints.
- The anthropic API (PID 2684) received multiple POST requests to "/v1/messages?beta=true" showing active communication during task execution
7. Final Execution and Network Activity
- git-remote-http (PID 8124) made final repository synchronization calls with GET requests to "/step-security/coding-agent-security.git/info/refs?service=git-receive-pack"
Key Security Observations
From this network activity, we can observe several critical differences from GitHub Copilot:
- Unrestricted Network Access: Claude Code freely accessed multiple package repositories, CDNs, and API endpoints without any built-in firewall restrictions
- Process Proliferation: Claude spawned numerous child processes (curl, node, bun) to handle different aspects of the task, each potentially making network connections
- Dynamic Package Resolution: Unlike Copilot's more controlled approach, Claude dynamically determined and installed packages based on its analysis of the task
This level of visibility would be impossible without runtime monitoring. Standard CI/CD logs show only high-level job status, while Harden-Runner reveals:
- Every network endpoint contacted
- Which specific process (with PID) made each connection
- The temporal sequence of operations
- The relationship between different tools and their network activities
The unrestricted nature of Claude Code's network access makes this monitoring not just useful but essential for security teams to understand what's happening in their CI/CD pipelines. You can see end to end flow in the screen recording below:
Conclusion: The Future of Secure AI Development
The anthropics/claude-code-action Claude Code action represents a different philosophy in AI coding agents - one that prioritizes capability and flexibility over built-in restrictions. This approach enables powerful automation scenarios but requires thoughtful security implementation.
By pairing Claude Code with Harden-Runner, organizations get the best of both worlds: unrestricted AI capabilities with comprehensive security visibility. The network monitoring data we've examined shows that Claude Code's flexibility is both its greatest strength and its most significant security consideration.
.png)
The future of software development is AI-powered, and with tools like Harden-Runner, we can ensure that future is also secure.

.png)