In the first article of this series, we explored the unique security considerations when running AI coding agents in CI/CD environments. Now, let's examine GitHub Copilot's security features and demonstrate how runtime monitoring with Harden-Runner creates defense-in-depth protection. As we'll see in the final article, these principles apply equally when securing Claude Code's flexible architecture.
Understanding GitHub Copilot's Network Firewall
GitHub Copilot includes thoughtfully designed security features, notably its agent firewall that controls internet access for the Copilot coding agent in GitHub Actions. This firewall, enabled by default, represents a proactive approach to security by limiting the agent's ability to make arbitrary network connections.
This design allows teams to maintain security while accommodating legitimate needs for external resources. The firewall effectively prevents many common attack vectors by blocking unauthorized network connections at the application layer.
The Black Box Problem: Limited Visibility in Agent Operations
While Copilot’s firewall provides critical protections, it doesn't offer visibility into what the coding agent is actually doing. This is especially problematic when:
- An AI-generated script installs dependencies or makes outbound requests.
- Enterprises need to verify which APIs were accessed.
- Teams need to trace a network call back to a specific code suggestion.
Questions that remain unanswered without deeper monitoring include:
- What processes were spawned by the agent?
- Which process made a particular network call?
- What endpoints were contacted?
- Which GitHub APIs were invoked?
This creates a black box scenario. When troubleshooting or performing a post-incident analysis, traditional GitHub Actions logs are insufficient to answer these questions.
Enhancing Security With Harden-Runner
StepSecurity Harden-Runner closes this visibility gap by monitoring the runtime behavior of GitHub Actions workflows, including those executed by Copilot. It extends GitHub’s native protections with:
- Complete Transparency: Capture every file access, process execution, and outbound connection made by Copilot-generated code.
- Behavioral Intelligence: Understand the context behind activity - e.g., which suggestion or prompt led to which system operation.
- Audit Logging: Maintain a forensically complete log of what transpired during each run.
- Anomaly Detection: Flag unusual or unexpected behaviors, even those that aren’t explicitly blocked by the firewall.
This transforms Copilot from a black-box assistant into a fully observable agent, giving teams the confidence to use coding agents securely in GitHub actions.
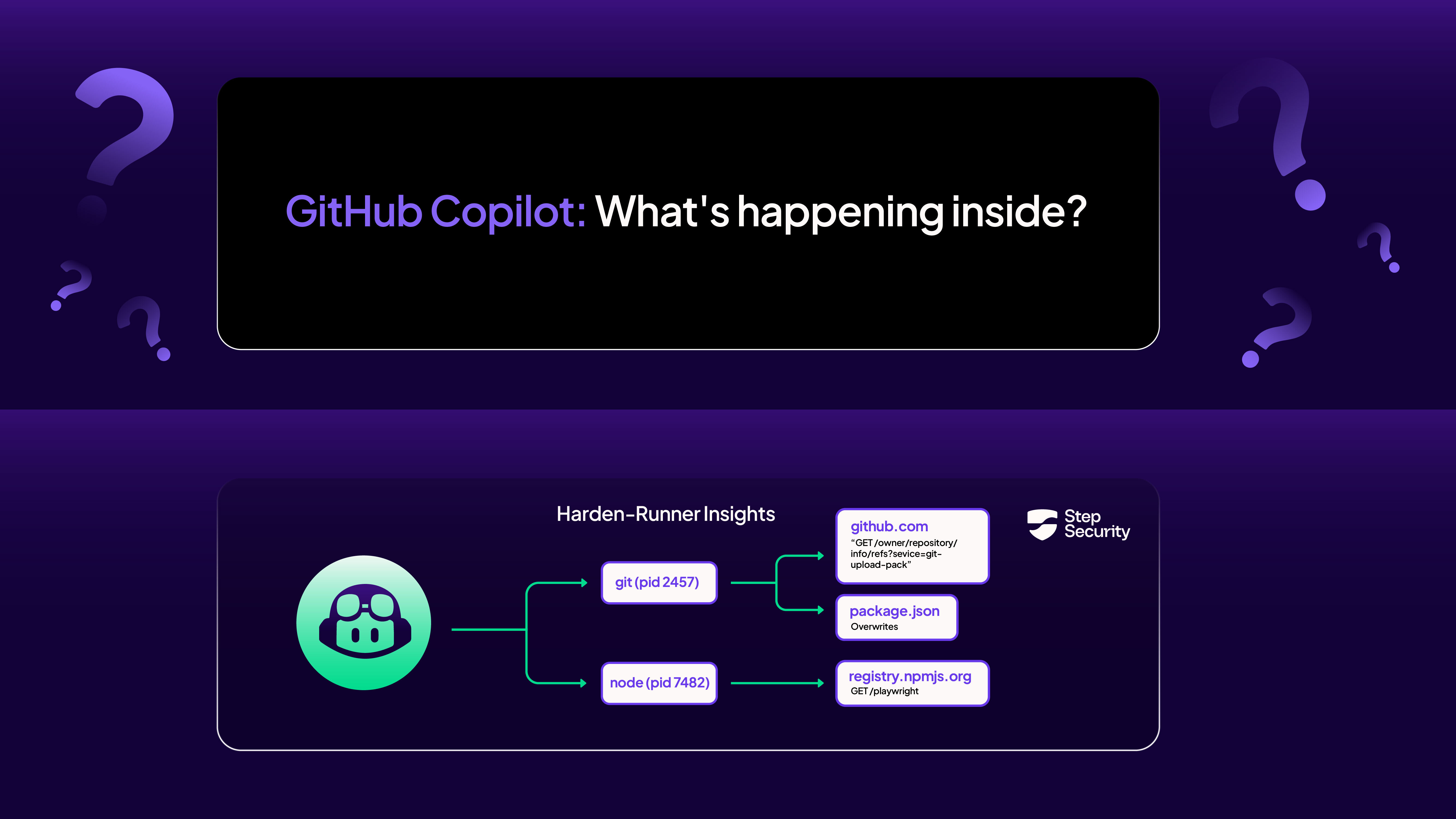
Implementing Harden-Runner with GitHub Copilot
GitHub Copilot allows users to customize the GitHub Actions environment by running a special GitHub Actions workflow before Copilot is executed. This GitHub Actions workflow must be stored at .github/workflows/copilot-setup-steps.yml. You can add Harden-Runner in this workflow file to monitor and secure Copilot sessions for your repository. Here's an example:
name: "Copilot Setup Steps"
on:
workflow_dispatch:
push:
paths:
- .github/workflows/copilot-setup-steps.yml
pull_request:
paths:
- .github/workflows/copilot-setup-steps.yml
permissions: {}
jobs:
copilot-setup-steps:
runs-on: ubuntu-latest
steps:
- uses: step-security/harden-runner@v2
with:
egress-policy: auditThis setup ensures that any action Copilot performs is audited and can be inspected in real-time via Harden-Runner.
Monitoring GitHub Copilot with Harden-Runner
Let's examine a real example of how Harden-Runner monitors Copilot. For this demo, we created a GitHub issue to build a Python program that generates an image with text and extracts text from the image using OCR. You can see this GitHub issue here.
Once the GitHub issue was assigned to Copilot, it triggered the GitHub Actions workflow run "Fixing issue #1". This workflow run was monitored by Harden-Runner due to the copilot-setup-steps.yml workflow file created previously. As this is a public repository, you can explore the Harden-Runner insights for this run here.
On this insights page, you can find detailed information about:
- Network Events: https://app.stepsecurity.io/github/step-security/coding-agent-security/actions/runs/16314882241?tab=network-events
- Process Events: https://app.stepsecurity.io/github/step-security/coding-agent-security/actions/runs/16314882241?tab=process-events
- File Events: https://app.stepsecurity.io/github/step-security/coding-agent-security/actions/runs/16314882241?tab=file-events
Detailed Network Activity Analysis
The network events tab reveals detailed runtime and security insights into Copilot's execution.
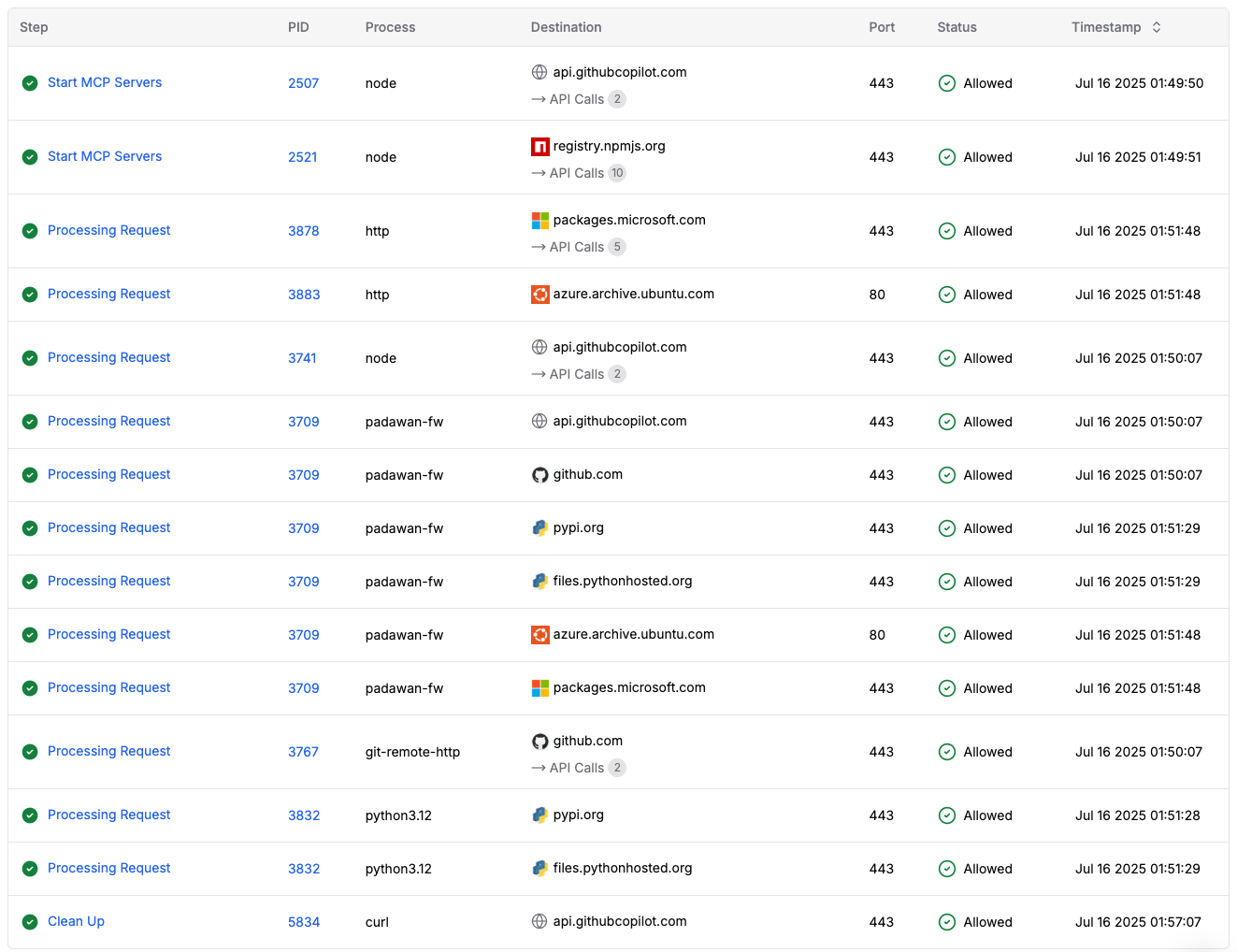
Based on the captured data, here's what happened during the workflow run:
1. Model Context Protocol (MCP) Server Initialization
- The workflow began with Node.js processes (PIDs 2507, 2521) starting MCP servers
- Node.js (PID 2507) made POST and GET calls to /mcp/readonly on api.github.copilot.com to establish MCP access
- Node.js (PID 2521) connected to registry.npmjs.org, downloading 10 packages including MCP SDK, playwright, commander, debug, mime, ws, and zod-to-json-schema, plus a security advisory check
- This phase set up the foundational tooling and security checks for Copilot's code generation capabilities
2. Repository and Git Operations
- Git-remote-http process (PID 3767) connected to github.com during the "Processing Request" step
- API calls were made to /step-security/coding-agent-security/info/refs for repository synchronization
- A POST request to /step-security/coding-agent-security/git-upload-pack indicated code changes being prepared
3. Copilot Agent Session Management
- Node.js process (PID 3741) connected to api.github.copilot.com
- Two key API calls were made:
- GET /models - to retrieve available AI models
- PUT /agents/sessions/890e7412-1208-49f9-b164-23526f1f4b40/logs - logging session activity
4. System Dependencies Installation
- HTTP processes (PIDs 3878, 3883) accessed packages.microsoft.com and azure.archive.ubuntu.com
- Specific packages were downloaded:
- Azure CLI components from /repos/azure-cli/dists/noble/InRelease
- Ubuntu packages including binary-amd64 and binary-armhf architectures
- System-level dependencies required for OCR functionality
5. Python Environment Setup
- The padawan-fw process (PID 3709) - Copilot's execution framework - orchestrated Python package installation
- Connections to pypi.org and files.pythonhosted.org downloaded Python dependencies
- Python 3.12 processes (PIDs 3832) were spawned to handle package installation
6. Package Management Activity
- Multiple padawan-fw processes connected to various package repositories:
- pypi.org for Python packages
- packages.microsoft.com for system tools
- azure.archive.ubuntu.com for Ubuntu packages
- The orchestrated installation pattern shows Copilot automatically resolved all dependencies for the OCR task
7. Code Generation and Completion
- Throughout execution, padawan-fw made calls to api.github.copilot.com
- A final curl process (PID 5834) during "Clean Up" connected to api.github.copilot.com
- This likely represented the session completion and pull request creation
Key Security Observations
From this network activity, we can observe several important security aspects:
- Legitimate External Access: All network connections were to legitimate services (GitHub, npm, PyPI, Microsoft packages) required for the task
- Process Attribution: Harden-Runner clearly shows which process made each network call, providing crucial context
- API Usage Patterns: Multiple GitHub API calls reveal how Copilot interacts with the repository throughout execution
- Package Management: The tool installation pattern shows Copilot automatically resolved dependencies for the OCR task
This level of visibility would be impossible without runtime monitoring, as standard CI/CD logs wouldn't capture these granular network interactions. You can see end to end flow in the screen recording below.
The Power of Runtime Network Security with Harden-Runner
Securing AI coding agents in CI/CD requires a multi-layered approach. GitHub Copilot's network firewall provides essential baseline protection, while Harden-Runner adds the enterprise-grade visibility and monitoring capabilities necessary for production environments.
The detailed network and runtime security insights by Harden-Runner show how even a simple task like implementing OCR functionality involves numerous external connections and package installations. Without proper monitoring, these activities remain invisible, creating potential security blind spots.
As we'll explore in the next article, these security principles become even more important when working with Claude Code, where the flexible architecture requires thoughtful security implementation from the start.

.png)