The cybersecurity community has finally woken up to a harsh reality: supply chain attacks aren't just targeting your final products anymore—they're compromising the entire infrastructure that builds your software. From the Ultralytics hijack through the devastating Shai-Hulud campaigns, to the recent TrustWallet compromise, attackers have realized that the highest ROI comes from targeting the factories, not just the products.
While the industry rushes to create frameworks and threat models to understand these attacks, organizations are left with a critical question: How do I actually protect my software development lifecycle today?
Building on Industry Research: From Framework to Implementation
The recent introduction of SITF (SDLC Infrastructure Threat Framework) by Wiz represents important progress in mapping supply chain threats. Their framework correctly identifies the five critical pillars under attack:
- Developer Endpoints/IDEs: Where code is written and dependencies are consumed
- Version Control Systems (VCS): Where source code and secrets are stored
- CI/CD Pipelines: Where software is built, tested, and deployed
- Package Registries: Where dependencies and artifacts are published
- Production Environments: Where software ultimately runs
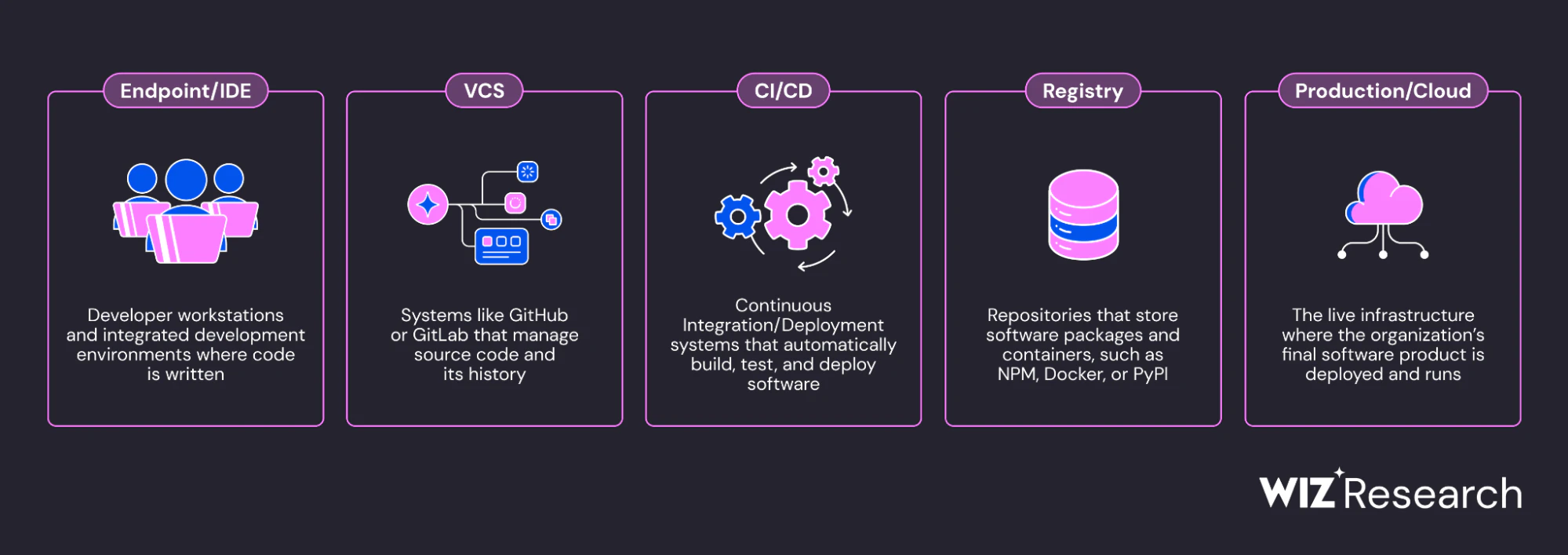
This comprehensive mapping validates what StepSecurity has been building toward - complete coverage across the entire software development lifecycle. The framework provides excellent guidance for organizations looking to understand their threat landscape.
At StepSecurity, we've taken this understanding and built actual deployed solutions across each of these critical areas.
StepSecurity's Implementation: Comprehensive Coverage Across Critical SDLC Pillars
Building on the comprehensive threat mapping that frameworks like SITF provide, StepSecurity has developed and deployed solutions across four of the five critical pillars. Our platform delivers active protection at the stages where modern supply chain attacks most commonly initiate and propagate.
Here's how StepSecurity provides comprehensive coverage across the SDLC:
Stage 1: Developer Environment Protection
Product: Developer MDM Protection: IDE extension monitoring, dependency visibility for human and AI actions, AI coding agent security, MCP server monitoring, policy enforcement
Modern attacks increasingly target developer machines as the entry point into your software supply chain. Developer MDM monitors what's actually happening on developer endpoints—from malicious packages being installed to AI coding agents making suspicious network calls.
.png)
Stage 2: Source Code & Dependency Security
Product: npm Package Search + GitHub Checks Protection: Package risk assessment, cooldown periods, compromised package detection, provenance verification
Your VCS and dependency management represent critical control points. npm Package Search provides real-time intelligence on package risks, allowing you to directly search for and view all compromised packages in the ecosystem, while GitHub Checks integrates directly into your pull request workflow to enforce security policies before code is merged.
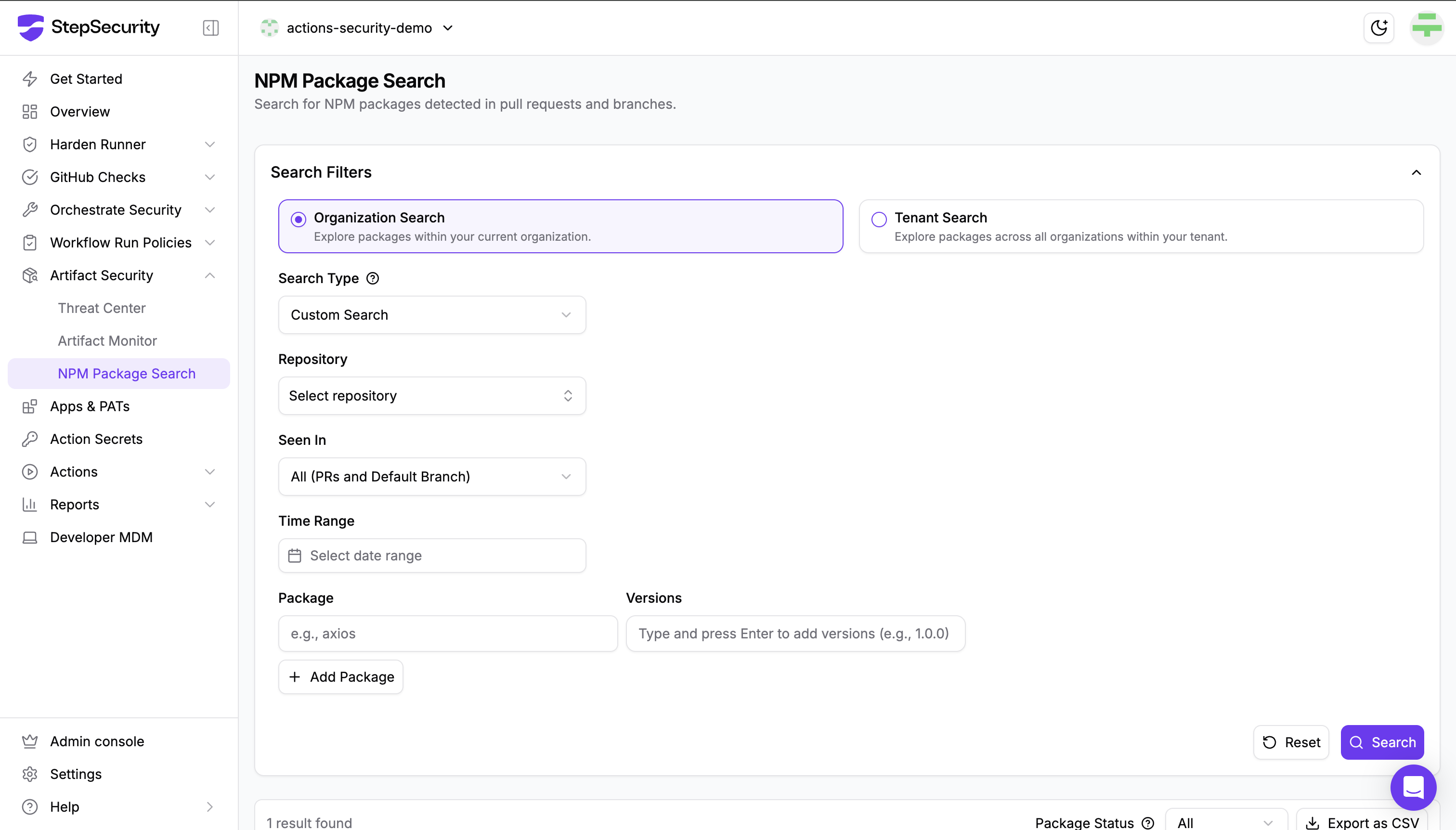
Key protections include:
- Cooldown Check: Automatically blocks dependencies published within the last 2 days (configurable), preventing the adoption of unvetted packages during the critical window when most supply chain attacks are discovered
- Compromised Updates Check: Maintains a real-time database of compromised packages, often updated before official CVEs are published, blocking known malicious dependencies at the pull request level
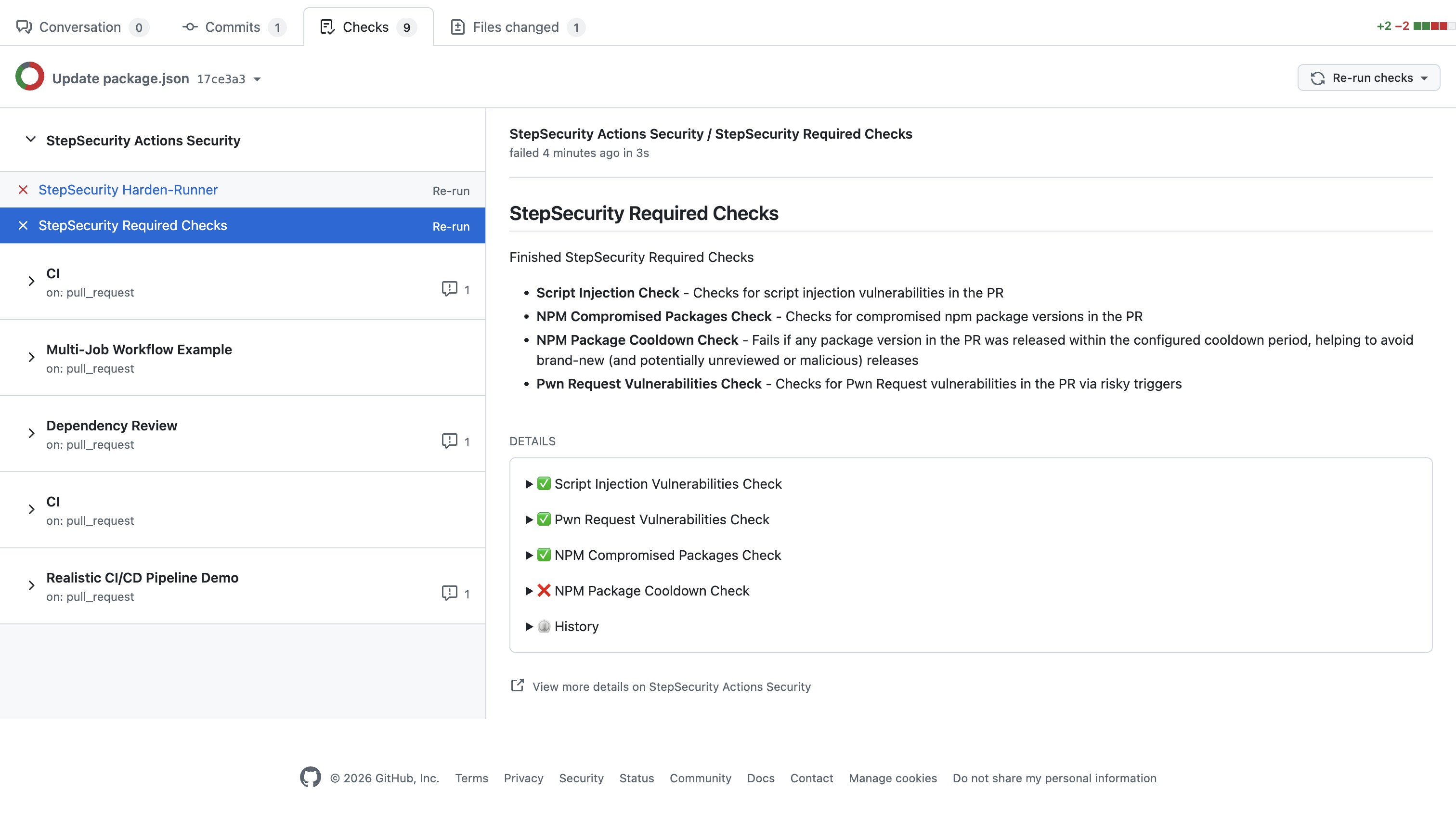
Stage 3: CI/CD Pipeline Security
Product: Harden-Runner + Actions Governance
Protection: Runtime monitoring, network egress control, baseline anomaly detection, secret protection, third-party Actions security
Your CI/CD pipelines have become the primary target for sophisticated attackers. Harden-Runner provides "EDR for CI/CD," monitoring every process, network call, and file access during your builds, establishing baselines and detecting anomalous behavior that indicates compromise. Actions Governance assesses the risk of third-party Actions and provides secure alternatives (StepSecurity Maintained Actions). For workflow files, StepSecurity identifies and remediates insecure workflow configurations org-wide with a single policy update.
.jpg)
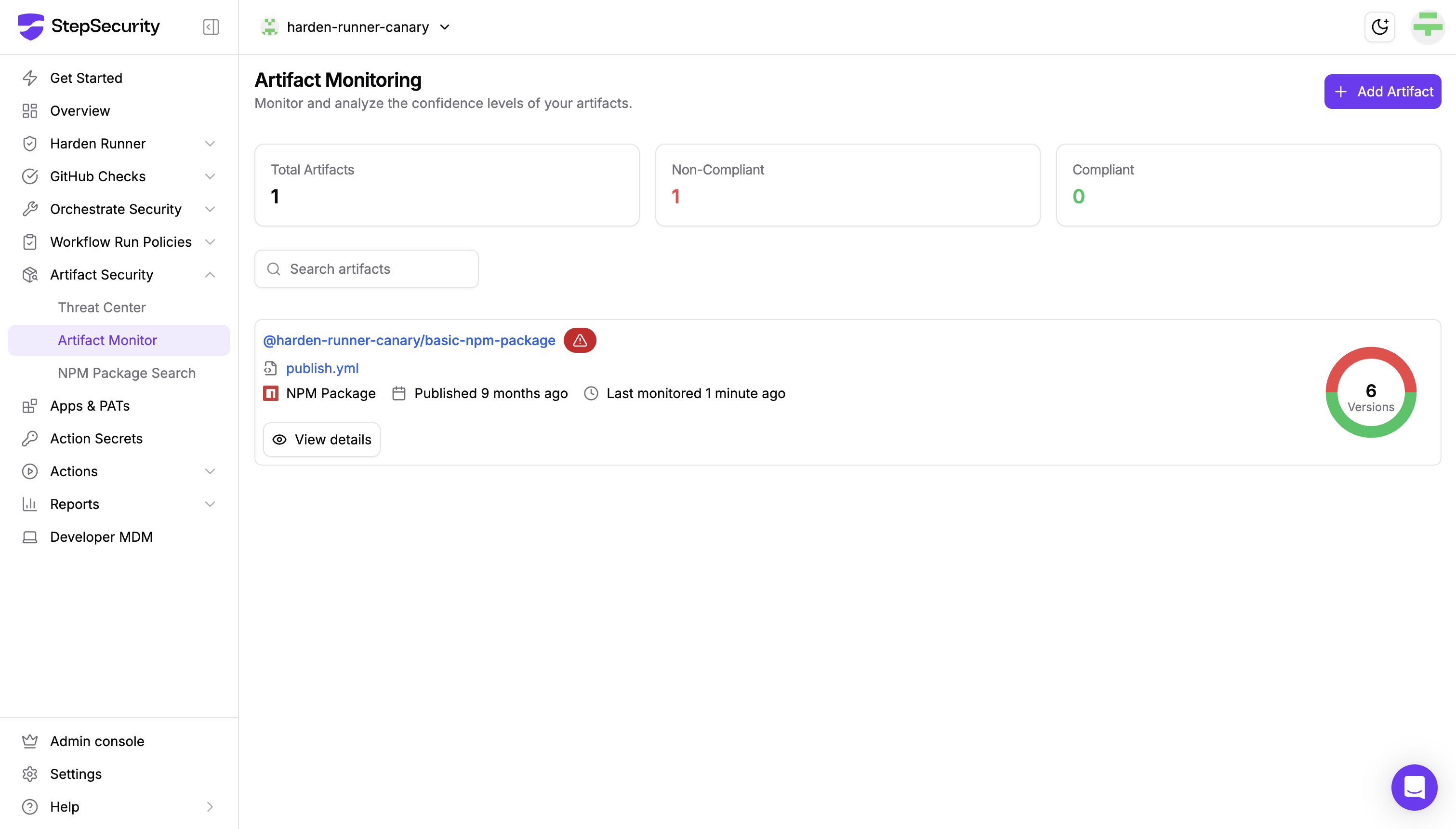
Stage 4: Registry & Artifact Security
Product: Artifact Monitor + npm Package Search Protection: Artifact integrity verification, malicious package detection, registry monitoring
Package registries serve as both attack vectors and propagation mechanisms. Our registry protection monitors for malicious artifacts, verifies integrity, and prevents compromised packages from entering your supply chain.
Why Complete Coverage Matters
Modern supply chain attacks succeed because they exploit the gaps between security tools. An attacker blocked at the CI/CD level will pivot to developer machines. A registry-focused defense will miss VCS compromises. Point solutions create point failures.
The Shai-Hulud campaign perfectly illustrates this reality—it succeeded by moving fluidly between developer endpoints, CI/CD systems, package registries, and back to endpoints. This validates the multi-pillar approach that frameworks like SITF advocate for, and demonstrates why StepSecurity built unified defense across these critical attack stages.
By securing the development and delivery pipeline comprehensively, StepSecurity prevents attacks from reaching production in the first place—stopping supply chain compromises at their source rather than trying to detect them after deployment.
With StepSecurity's comprehensive platform:
- Defense in depth: Multiple intervention opportunities across the development and delivery pipeline
- Unified visibility: Correlation of threats across all critical SDLC stages
- Coordinated response: Integrated incident response throughout the development lifecycle
- Continuous protection: Real-time defense at the stages where attacks most commonly begin and spread
Ready Today, Not Tomorrow
While the industry debates frameworks and threat models, StepSecurity customers are already protected. Our platform is deployed across thousands of organizations, actively blocking supply chain attacks every day.
The question isn't whether you need SDLC security—recent attacks have settled that debate. The question is whether you want theoretical frameworks or actual protection.
Don't wait for the next Shai-Hulud. The time for frameworks has passed—the time for protection is now. Start your free trial today and see StepSecurity block real CI/CD threats in real time.



.png)
