At StepSecurity, we set out to solve a fundamental problem
CI/CD pipelines had become the highest-value target in the software supply chain, yet they operated with virtually no runtime security.
Today, we're celebrating a milestone that validates this mission.
Harden-Runner now protects over 10,000 open-source repositories. Harden-Runner is also used by companies across open source, security, and enterprise environments. A public list of organizations using Harden-Runner is available in our documentation
What Harden-Runner Actually Does
Harden-Runner is essentially an EDR solution for CI/CD runners.
Just as traditional endpoint detection and response (EDR) protects laptops and servers by monitoring activity, detecting threats, and enforcing protections, Harden-Runner extends the same security model to CI/CD runners. It continuously observes workflows, inspects runtime behavior, and blocks malicious activity before it can cause damage.
As strong believers in open-source, we also offer a free community tier for open-source projects, making it easier for maintainers to secure their CI/CD pipelines without added cost.
This number reflects a fundamental shift in how organizations approach pipeline security, moving from reactive incident response to continuous, proactive protection. It represents three years of relentless focus on making CI/CD secure by default
The Journey: From Zero to 10,000
When we launched Harden-Runner in March 2022, the CI/CD security landscape was vastly different. Most organizations treated their build pipelines as trusted environments—a dangerous assumption that attackers had already begun exploiting. We built Harden-Runner to change that assumption, bringing endpoint-style runtime security to CI/CD runners.
The growth trajectory tells the story:
- March 2022: Harden-Runner launches with core network monitoring and egress control
- End of 2024: 5,000 open-source repositories protected
- End of 2025: 10,000 repositories protected. We doubled our adoption in a single year
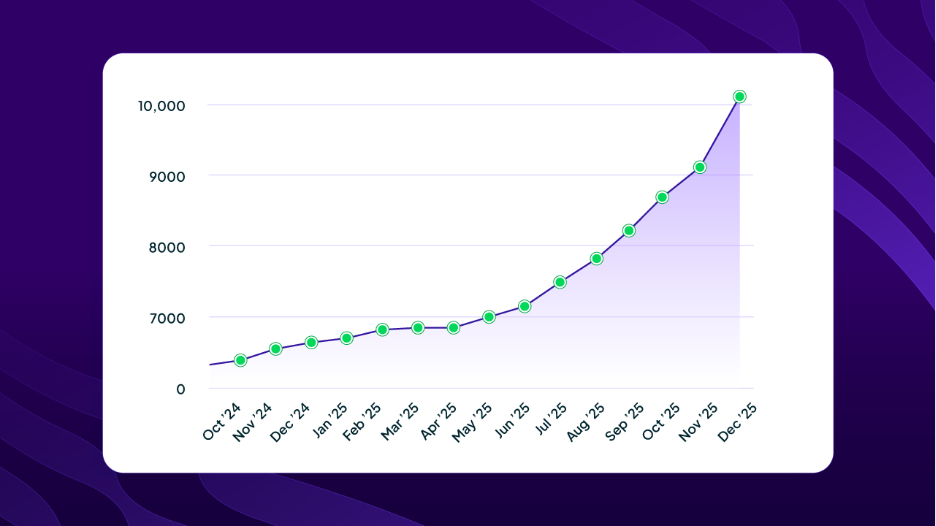
That acceleration reflects a critical industry awakening. Organizations now recognize that securing the build process is just as important as securing the application itself. With over 13 million jobs monitored weekly, we're seeing this shift play out across individual developers, open-source projects, and Fortune 500 enterprises.
Real-World Impact: When Detection Matters Most
Harden-Runner's value isn't just measured in features; it's measured in threats detected and attacks prevented. Over the past three years, we've caught supply chain attacks that others missed, often becoming the first line of defense when trusted components turned malicious.
The tj-actions Compromise: Detection Before Public Disclosure
In one of our most significant detections, Harden-Runner flagged suspicious behavior in the widely-used tj-actions/changed-files Action before any public disclosure. The Action had been compromised through a sophisticated supply chain attack, and malicious code was executing in thousands of workflows.
Harden-Runner detected anomalous network traffic patterns that didn't match established baselines. This early warning allowed affected organizations to respond immediately, preventing potential credential theft and code tampering. The incident demonstrated why runtime monitoring is critical: static analysis can't catch what happens when trusted dependencies turn malicious at runtime.
Shai Hulud: Catching a Novel Attack Pattern
When the Shai Hulud supply chain attack targeted CNCF's Backstage repository, Harden-Runner was there to catch it. This attack represented a new category of threat, one that traditional security tools weren't designed to detect. Our runtime monitoring identified the attack's signature behavior, providing immediate visibility into the compromise.
s1ngularity: Nx Package Compromise and AI CLI Weaponization
In August 2025, the popular Nx build system was compromised in an incident dubbed s1ngularity. Malicious versions were published to npm and delivered a data-stealing payload via a post-install script that harvested developer secrets like GitHub and npm tokens, SSH keys, environment variables, and wallet data.
The malware also attempted to abuse local AI CLI tools such as Claude, Gemini, and q to help with reconnaissance and data collection, marking a new escalation in supply chain attacker tradecraft.
Harden-Runner successfully flagged the activity as anomalous during runtime analysis. The compromised install path made unexpected outbound calls to api.github.com during npm install, which is not normal package-install behavior. The process chain also revealed the malicious post-install script spawning credential theft actions like gh auth token, which Harden-Runner surfaced clearly in workflow telemetry.
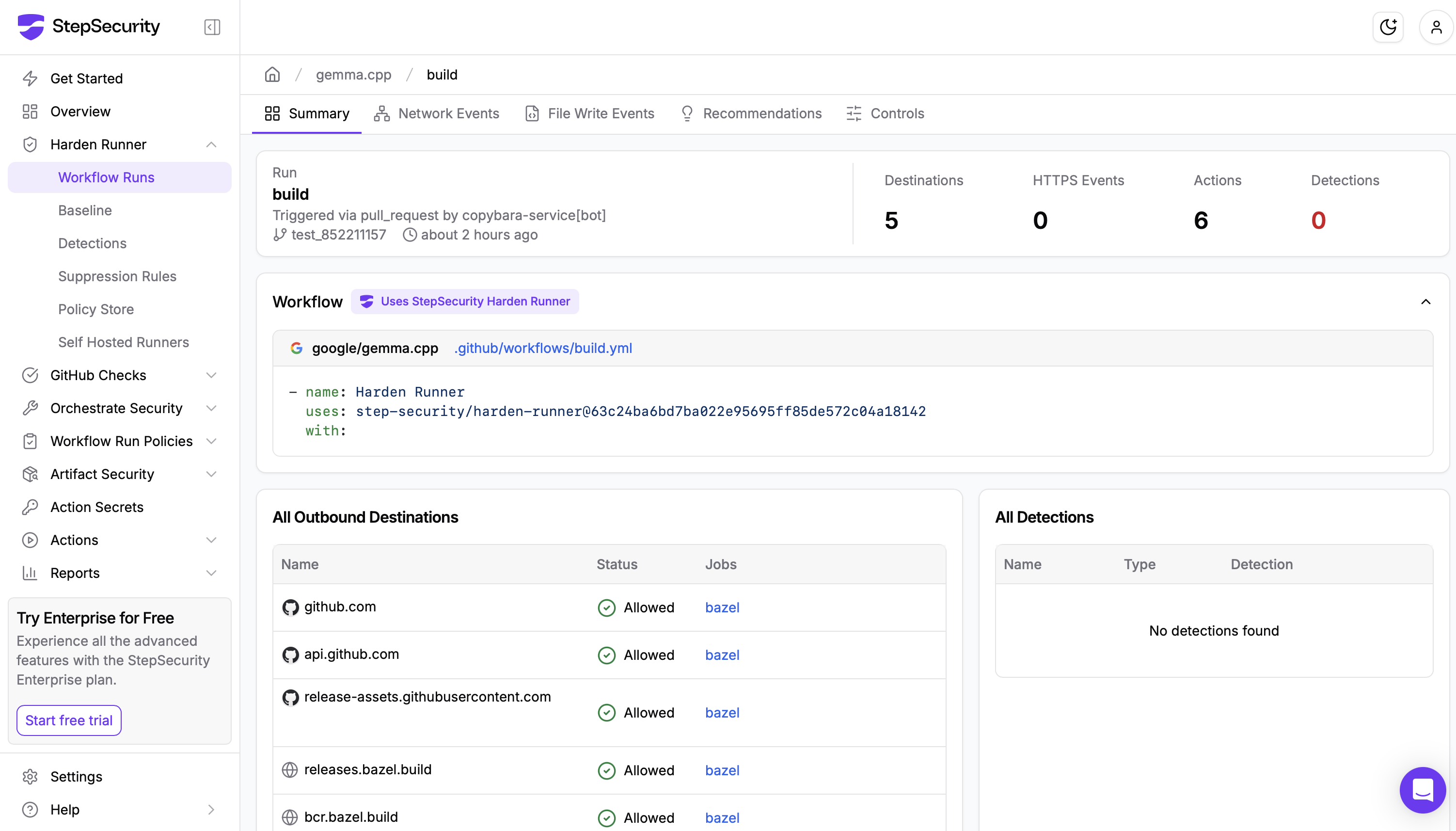
Flank: Detecting a Real Supply Chain Attack
When an independent security researcher demonstrated a supply chain attack on Flank, Google's open-source mobile testing project, Harden-Runner detected it in real time. The researcher exploited a vulnerable GitHub Actions workflow to gain access to an elevated GITHUB_TOKEN with write permissions to the repository. They crafted an innovative exploit that attempted to blend in with normal traffic patterns, downloading and executing code that exfiltrated the token by reading runner worker memory.
Harden-Runner had been monitoring Flank's workflows since December 2022, building baselines of normal network behavior. When the exploit made an outbound call to raw.githubusercontent.com, a domain that had never appeared in previous runs, Harden-Runner immediately flagged it as anomalous. The detection happened despite the researcher's efforts to circumvent monitoring by using familiar GitHub endpoints.
In the researcher's own words: "Ran into StepSecurity Harden-Runner while executing a PoC against a Google OSS repository and it picked up an anomalous curl to raw.githubusercontent.com despite some initial effort I made to blend in. The maintainers had Harden Runner in audit mode, but that telemetry could very well be the difference between a supply chain attack and successful incident response for an organization that actually alerts on it."
Had this been a real attack instead of ethical security research, the compromised token could have been used to tamper with Flank's releases, potentially affecting all downstream users. Harden-Runner's detection provided the visibility needed to identify and respond to the threat in real time.
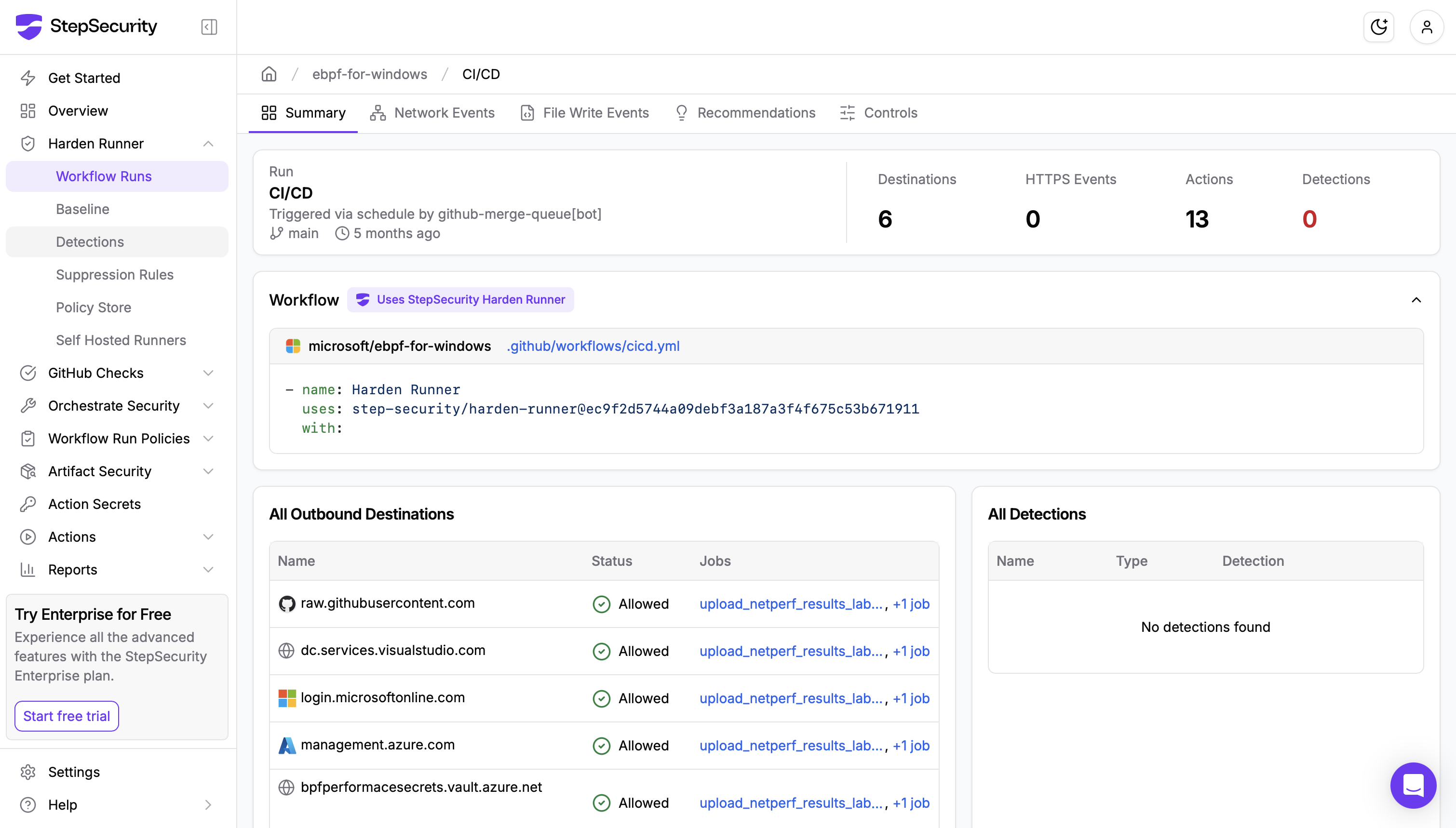
Microsoft Azure Karpenter Provider: Real-Time Detection in a High-Trust Project
Harden-Runner also detected a real-time CI/CD supply chain attack in Microsoft’s open-source Azure Karpenter Provider project. An independent security researcher exploited a misconfigured GitHub Actions workflow that allowed untrusted code to run with elevated permissions, resulting in access to a GITHUB_TOKEN with id-token: write scope. In a real attack, this token could have been used to access cloud resources tied to the workflow.
Because Harden-Runner had been deployed across the project’s workflows, the exploit was detected immediately through anomalous outbound network activity. The malicious run attempted to fetch code from a GitHub gist and exfiltrate credentials to an external domain, both of which deviated from the established baseline of normal workflow behavior. StepSecurity reported the issue to Microsoft’s Security Response Center within an hour, and the disclosure was formally acknowledged by Microsoft.
Building the Platform: Three Years of Innovation
Reaching 10,000 protected repositories required building a platform that adapts to how teams actually work. Since launch, we've focused on making Harden-Runner powerful enough for enterprise environments while remaining simple enough for individual developers.
2023: Expanding Beyond GitHub-Hosted Runners
- Kubernetes-Based Self-Hosted Runners (March 29, 2023): We launched support for Kubernetes-based GitHub Actions runners using Actions Runner Controller (ARC). This brought Harden-Runner's runtime security to organizations running ephemeral runners in their own infrastructure, providing the same visibility and control regardless of where workflows execute.
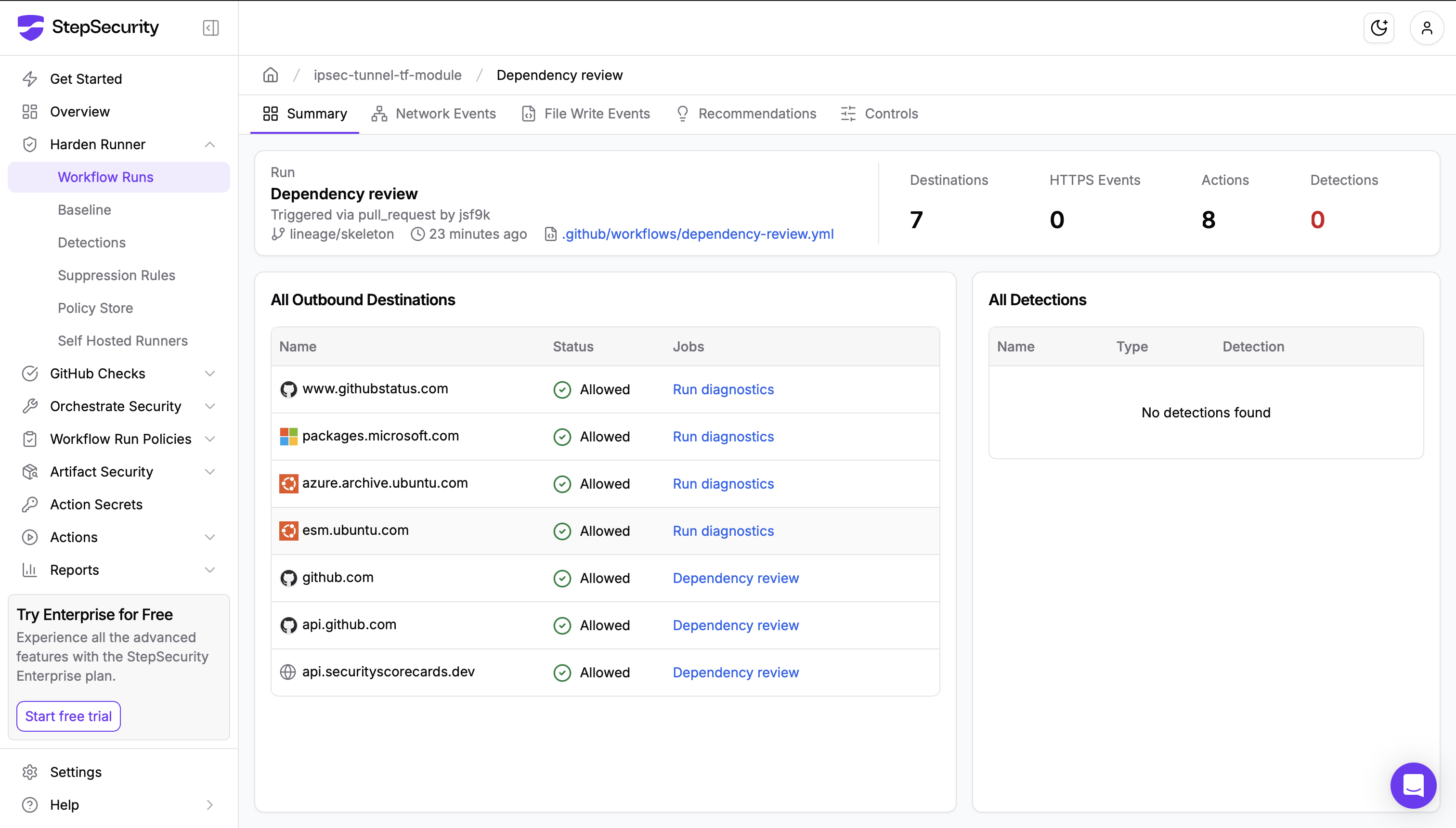
- Policy Store (April 4, 2023): Managing security policies through workflow files created friction. Every policy change required modifying potentially hundreds of workflows. The Policy Store changed this by allowing teams to define and enforce policies centrally.
- Runtime Detections UI (June 6, 2023): We introduced a dedicated UI for investigating runtime detections, making it easier for security teams to triage alerts, understand attack timelines, and respond to incidents. The UI shows exactly what happened during a workflow run: which processes executed, what network calls were made, and which files were accessed.
- Self-Hosted VM Runners (October 5, 2023): Organizations running self-hosted virtual machine runners gained full Harden-Runner support. Whether you're running on AWS, Azure, GCP, or on-premises infrastructure, Harden-Runner provides consistent runtime security across all environments.
2024: Enhanced Visibility and Control
- HTTPS Outbound Request Monitoring (February 20, 2024): We launched support for monitoring outbound HTTPS requests from GitHub-hosted and self-hosted VM runners. This capability provides deep visibility into encrypted traffic, allowing teams to see not just which domains workflows connect to, but the specific API endpoints and methods used. HTTPS monitoring enables more precise security policies and helps detect sophisticated exfiltration attempts that try to hide in legitimate traffic.
- Unified Network Egress Management (September 19, 2024): We introduced unified network egress insights and outbound endpoint management for GitHub Organizations and Actions Runner Controller (ARC) clusters. This feature provides a centralized view of all network activity across your entire GitHub organization or ARC cluster, making it easier to identify patterns, set organization-wide policies, and detect anomalies that span multiple repositories or runners.
2025: Platform Expansion and Intelligence
- Amazon S3 Integration (April 23, 2025): We launched direct export of Harden-Runner insights and detections to Amazon S3, enabling integration with existing security information and event management (SIEM) platforms. Security teams can now incorporate CI/CD runtime data into their broader security operations workflows.
- GitHub-Hosted Custom Runner Images (December 16, 2025): GitHub's introduction of custom runner images created a new opportunity: bake Harden-Runner directly into your infrastructure. Instead of adding Harden-Runner to each workflow, you can now embed it in your custom image. Every workflow that uses the image automatically gets runtime protection. No workflow changes required. This dramatically reduces configuration overhead while ensuring comprehensive coverage.
What the Community Says
The 10,000 repositories protected by Harden-Runner represent thousands of individual decisions to prioritize runtime security. Here's what developers and security engineers are saying:
“Before StepSecurity, detecting the origin of a suspicious outbound network connection was challenging with traditional CNAPPs or IDS solutions, as we’d only see a general alert. StepSecurity gives us complete visibility into which specific Action triggered a connection and even lets us drill down into host processes tied to that Action. Now, we have a clear and actionable picture of every network connection our runners make, and we can respond with confidence”
--Jean-Philippe Lachance, Staff Security Specialist, R&D, Coveo
“It’s easy to get started with GitHub Actions, but using it securely has historically required manual effort and configuration, which isn’t as straightforward. StepSecurity solves this by automating security best practices for workflows, as well as through their Harden-Runner action, which provides protection against exfiltration and source code tampering throughout the lifecycle of a workflow. Leveraging the Harden-Runner action is both painless and an absolute must for any project.”
--Evan Gibler, Staff Security Engineer, Chainguard
"Harden-Runner strikes an elegant balance between ease-of-use, maintainability, and mitigation that I intend to apply to all of my 300+ npm packages. I look forward to the tool's improvement over time."
--Jordan Harband, Open Source Maintainer
"Harden-Runner is a Must-Have GitHub Action to Prevent Supply Chain Attacks. StepSecurity is the one-stop-shop to harden your GitHub Actions and ensure peace of mind."
--Wenqi Glantz, Software Architect
"Harden-runner is an amazing project by StepSecurity! You can easily integrate it in your GitHub Actions and it will block egress traffic and ensure your code isn't overwritten at runtime, to protect against malicious or compromised dependencies."
--Christophe Tafani-Dereeper, Cloud Security Engineer
"Since enabling Harden Runner in our projects, we have much higher confidence and observability into what our build process is doing. This is just one step in a much broader piece of work we are doing to increase the trust in our supply chain security."
--Cam Parry, Senior Site Reliability Engineer, Kapiche
Key Open-Source Projects Secured by the Harden-Runner Community Tier
The Harden-Runner Community Tier is trusted by some of the most widely used open-source projects and ecosystems in the world. These projects sit at the core of modern software development and infrastructure, which makes their CI/CD pipelines especially attractive targets for supply chain attacks.
Today, Harden-Runner helps protect workflows across projects and organizations including:
- Microsoft – Securing CI/CD pipelines that support widely used developer tools and cloud services.
- Google – Protecting open-source workflows that underpin large-scale infrastructure and developer ecosystems.
- CISA (Cybersecurity and Infrastructure Security Agency) – Supporting secure build practices in projects tied to critical infrastructure and national security.
- Kubernetes – Helping safeguard the CI/CD pipelines behind one of the most foundational cloud-native platforms.
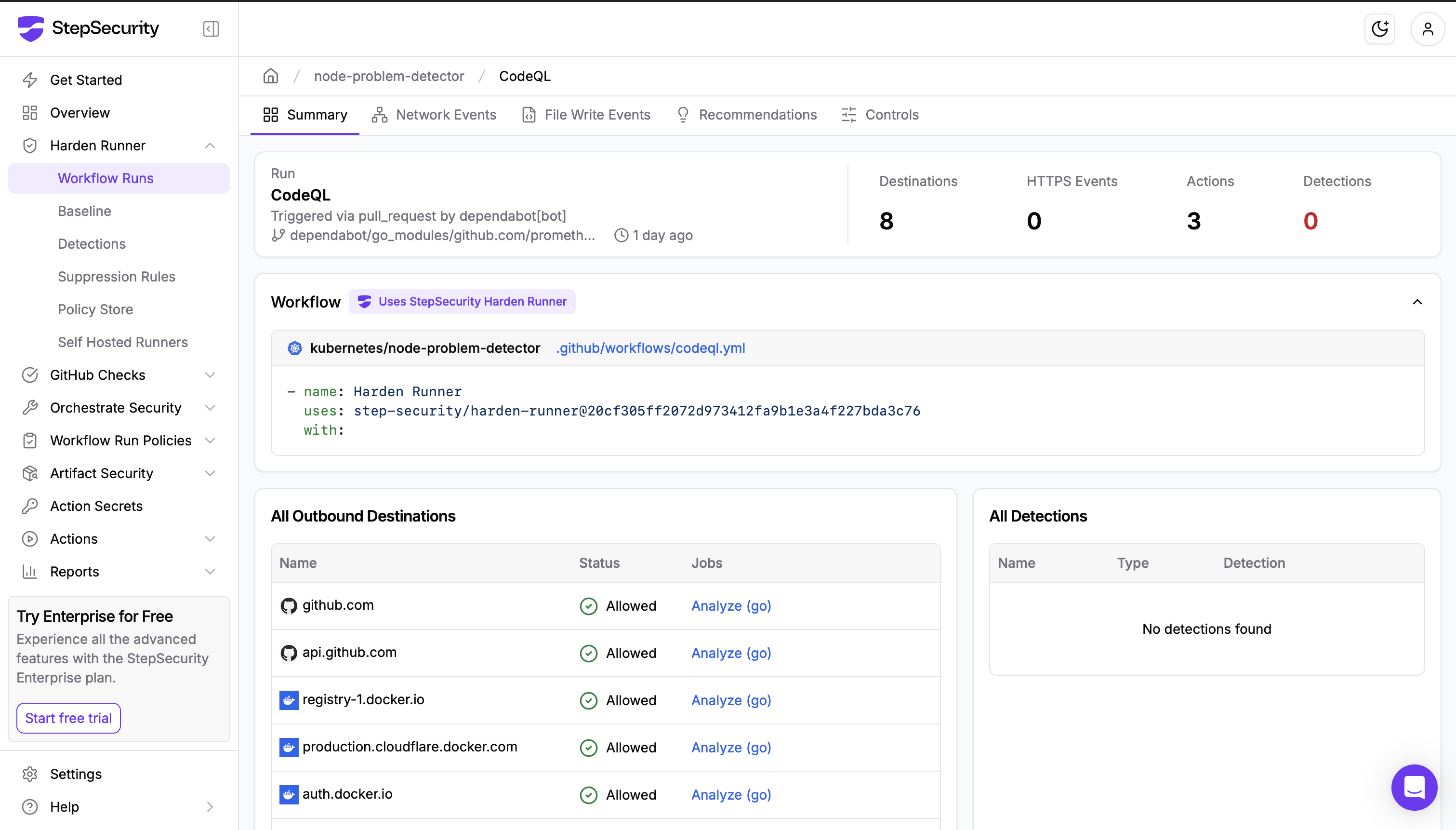
Many more projects use Harden-Runner across the open-source ecosystem. You can see more here
Looking Ahead: The Next 10,000
Reaching 10,000 protected repositories marks a significant milestone, but it's just the beginning. The threats facing CI/CD pipelines continue to evolve, and so must our defenses. We're focused on three key areas:
- Platform Expansion: We're actively developing Harden-Runner support for macOS and Windows runners. These platforms present unique security challenges, and we're working with design partners to ensure we deliver the same level of visibility and control that Linux users expect.
- Deeper Intelligence: As our detection data grows, we're building more sophisticated baseline learning and anomaly detection. The goal is to catch threats earlier while reducing false positives, providing security teams with the high-fidelity signals they need to respond effectively.
- Ecosystem Integration: Security doesn't happen in isolation. We're expanding integrations with security platforms, making it easier for teams to incorporate CI/CD runtime data into their existing security operations.
Join the Next Wave
Whether you're protecting a solo project or enterprise infrastructure, Harden-Runner delivers the runtime visibility and control that modern CI/CD demands. Our Community Tier remains free for all public repositories, making it easy to get started.
Ready to secure your workflows?
Use our Secure Workflow tool to automatically integrate Harden-Runner into your GitHub Actions with minimal configuration. Join the 10,000+ repositories that have made runtime security a default part of their development process.
Together, we're building a future where CI/CD pipelines are secure by default, not as an afterthought, but as a fundamental property of how we build software.
.png)
.png)


